The SSH (Secure SHell) protocol is a remote shell protocol that creates a secure channel (by using an encrypted connection), for accessing servers on an insecure network (like the Internet itself).
SSH replaced unencrypted protocols like telnet, rsh and rlogin. Nowadays it is the standard protocol used for accessing the CLI (Command Line Interface) on Linux servers. It also provides other features like remote command execution, file transfers, graphical console access and tcp port forwarding, always using an encrypted channel. Usually, we use SSH by client program ssh on Linux.
In this tutorial we’ll explore 2 methods to connect to SSH without typing a password. The first method is setting up passwordless SSH login using public key authentication, and the second is by passing the password non-interactively to SSH with SSHPass.
[] denotes an optional parameter, and < > denotes a mandatory one. These are the same conventions used on most Linux manual pages.Table of Contents
The ssh Command
The ssh command syntax:
ssh username@server [options]
or
ssh -l username server [options]
Where:
- username: is the name of the remote user to use for connection. If it’s not informed, ssh will use the username of the current logged user.
- server: remote server name or IP address.
- Options: optional flags to modify the behavior of ssh, like:
-P<port> for specifying a different port than 22 to connect to-Cto enable compression- etc. Check the manual page of
ssh(man 1 ssh) for a complete list of options.
Running this command will ask for a password. After informing the password, the access is granted and we are connected to the remote host.
Another common scenario where SSH is used is with remote commands execution, where we inform a command. The command will run on the remote server and the results (if any) are displayed on the local screen. This is very useful for gathering information and executing remote tasks, like backups:
ssh username@server "tar czvf /tmp/etc_backup.tar.gz /etc"
This command will create a file called etc_backup.tar.gz in the /tmp directory, with all files and folders of /etc directory (which has the configurations of our Linux machine). Then, we could run another command for downloading this backup from the remote machine to local machine:
scp username@server:/tmp/etc_backup.tar.gz /root
Again, both commands (ssh and scp) will ask for a password, and (for security reasons) they do not provide a convenient way to pass the password in the command line. This can be a nuisance if we want to execute this automatically on a regular basis, for example as a cron task. Fortunately, there are two methods for working around this: public key authentication and sshpass.
Passwordless SSH Login Using Public Key Authentication
Also known as PubKey Authentication, it consists in creating a pair of cryptographic keys: a public and a private key. The public key goes on the server.
You can imagine it as a keylock protecting a gate that is exposed and is useless without the key.
The private key is the key that stays with the user, and is presented to the server by the ssh command when we want to connect to it (unlocking the “gate” and granting access).
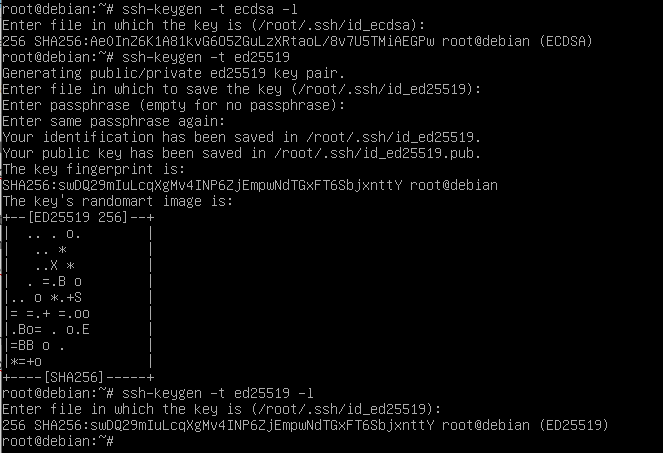
Generating the keys pair:
ssh-keygen [options]
Main options:
-t<type>: specify the key type. Accepted values are dsa, rsa, ecdsa and ed25519. If not specified, rsa is used.-b<bits>: specify the key size. The minimum recommended value for rsa keys is 2048 which is also the default value.-f<file>: specify the filename of the key file. By default, the private key is stored on $HOME/.ssh/id_<type> and the public key on $HOME/.ssh/id_<type>.pub
If invoked without any flags, ssh-keygen will generate a RSA key pair, 2048 bits long. The command will execute the following steps:
- Ask for a file to store the key. The value inside the round brackets is the default and will be used unless something else is typed.
- Create the $HOME/.ssh directory, if it does not exist yet.
- Ask twice for a passphrase. If used, the passphrase will encrypt the private key and will be asked every time the key is used. As we want a non-interactive way to access the SSH server, leave the passphrase empty, by just typing Enter twice.
- And it’s done! The keys where created at $HOME/.ssh directory, and the key fingerprint is presented:
Installing the Public Key
We can install the public key on the remote server by using the ssh-copy-id tool
ssh-copy-id
Syntax:
ssh-copy-id [options] [user@]machine
Options
-i<public key file>: specify the public key file to use. The default value is $HOME/.ssh/id_rsa.pub- user: the username at the remote machine to install the key to. If not informed, will be used the current logged user.
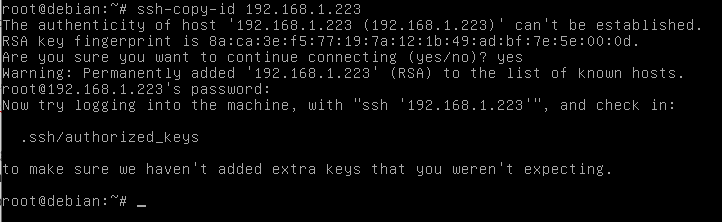
You’ll be asked for the password as usual. After that, the public key is installed and we can test it.
Testing
After installing the key, we can run the ssh command against the remote machine. This time, we should be able to connect without being asked a password:
Syntax:
ssh -l user host
Or if we are using a private key with a non-default name or in a non-default location
ssh -i /path/to/private/key -l user host
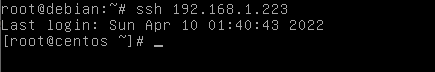
Sucess! Now, all SSH comnands executed by user root towards user root on machine 192.168.1.223 will connect without ask for a password.
Pass Password to SSH or SCP using SSHPass
Although it is the preferred method (on a security basis), sometimes we are unable to use PubKey authentication.
For example, we may need to connect to a hardware device that does not support the install of a public key (like some network switches), or the server may have Pubkey authentication turned off. In this case, we can resort to sshpass command. This command will receive a password and call ssh or scp command using the provisioned password.
Installling sshpass
The sshpass command is not installed by default, but is available on most Linux distros. You can install it by executing the following command:
apt -y install sshpass
or
yum -y install sshpass
Provisioning the Password
We can inform the password by three methods:
- informing it directly on the command line
- storing it on a file (and protecting the file accordingly) or
- using an environment variable called SSHPass
Note: For the examples below, we will use mySuperComplexSecretPassword as the user password.
Informing the password on the command line
This method is pretty straightforward. We use the -p flag, followed by the password to use:
sshpass -p"mySuperComplexSecretPassword" <ssh command goes here>
Using a password file
This method is pretty straightforward and permanent: you only execute it once and will work as long the password on the file is correct. Create a file called mypasswordfile.txt (you can, and should, use another name):
touch mypasswordfile.txt
Put your password inside the file, on the first line:
echo "mySuperComplexSecretPassword" > mypasswordfile.txt
Set the file’s permissions so only you can read it:
chmod 400 mypasswordfile.txt
Now, we use the -f flag, with the file we created
sshpass -fmypasswordfile.txt <ssh command goes here>
Using an environment variable
In this method we need to declare an environment variable called SSHPass, with the desired password as value. Basically, it can be done two ways:
export SSHPASS=mySuperComplexSecretPassword sshpass -e <ssh command goes here>
Or in line with the command:
SSHPASS=mySuperComplexSecretPassword sshpass -e <ssh command goes here>
Both methods will work the same way.
Running the SSH Command
After defining how we will present the password to sshpass, we can then run the desired command, which is pretty simple: we can just prepend the ssh or scp command with the proper sshpass command. Some examples below:
| Without sshpass | With sshpass |
|---|---|
| ssh root@myserver.com | SSHPASS=mypass sshpass -e root@myserver.com |
| scp -r root@myserver.com:/etc /tmp | sshpass -p”mypass” scp -r root@myserver.com:/etc /tmp |
Conclusion
In this tutorial we covered how to set up passwordless SSH login by using public key authentication, and how to login using SSHPass by passing the password to SSH. If you have any feedback or questions feel free to leave a comment and we’ll get back to you as soon as we can.