FreeRADIUS is a free and open-source implementation of the RADIUS protocol. It’s the most popular and widely deployed open-source RADIUS server, being also used by many Fortune-500 companies, telecommunications companies, and Tier 1 ISPs.
FreeRADIUS most often refers to the RADIUS server, which is just one component of the FreeRADIUS suite. Other components included are:
- BSD-licensed RADIUS client library
- a PAM1PAM (Pluggable Authentication Modules) is a flexible system used in Linux and other Unix-based systems for managing user authentication. It allows administrators to enforce different authentication policies and methods depending on the specific needs of their system or application. library
- an Apache RADIUS module
- additional utilities and development libraries related to RADIUS
RADIUS (Remote Authentication Dial-In User Service) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for users who connect to a network service. Here are some short descriptions of what each of the terms in AAA means:
- Authentication: the process of determining whether the client (which can be a user, device, or process) is a legitimate user of the system
- Authorization: the process of determining what the client is allowed to do on the network
- Accounting: is the process of monitoring the client’s activity on the network and providing the information necessary to bill for services
What are some real world examples for using the RADIUS protocol?
You can use RADIUS in situations when you have users that need to connect to your network and you need a solution to manage them – they need to authenticate, you give them various authorizations as to what they can do when connected to your network, and you keep track of how they use your network (accounting).
A few rudimentary examples of real world services that use RADIUS are:
- Universities: some may offer free WiFi access for students and staff, so they’ll offer credentials to students and staff and only allow users with valid credentials to authenticate and use the University WiFi
- VPN providers: using RADIUS, you can offer authentication for your users, authorize them to use your service while they haven’t exhausted their allocated bandwidth and paid their subscription, and keep track of their network usage
In this tutorial, we’ll install FreeRADIUS on a server running Ubuntu 22.04/20.04 and configure it to work with MySQL/MariaDB; we’ll also install daloRADIUS, a RADIUS web management panel, which is basically a FreeRADIUS GUI, and then perform a simple test on the RADIUS server to make sure it works.
Table of Contents
Prerequisites
- A server running Ubuntu 22.04/20.04, and we recommend a minimum of 512 RAM and 300MB storage space.
- Being logged in as a non-root sudo user. This is because when you’re acting as root, you can do anything, and the system won’t ask. If you’re not careful, you can harm your system, and if you run malicious/buggy applications with root permissions, the application can harm your system. There is a good reason why this has been the security model for years.
Assuming you’re on a fresh server running Ubuntu 22.04/20.04 install, first, we’ll update the server’s package index and upgrade to the latest packages:
sudo apt update sudo apt upgrade
Skip the setup and instantly deploy a pre-configured FreeRADIUS server with MySQL and daloRADIUS in seconds. Our solution is secure, fully configured, and designed to save you time.
Your servers, managed for you, so you can focus on your business.
Need a custom solution? Our expert team is available for hire. Feel free to contact us.
Install LAMP Stack
The LAMP stack is a group of open-source software that can be used to create web applications and websites. LAMP is an acronym for Linux, Apache, MySQL, and PHP.
Install Apache Web Server
sudo apt -y install apache2
Enable Apache so it starts on boot:
sudo systemctl enable --now apache2
Include Apache’s application profile in UFW’s rules:
sudo ufw allow WWW
WWW. You can also try sudo ufw allow Apache instead.Check access to Apache by visiting the server’s IP or hostname ( http://ip_address )
You should see something like this in your browser:
Install PHP and additional PHP Modules
sudo apt -y install php libapache2-mod-php php-{gd,common,mail,mail-mime,mysql,pear,db,mbstring,xml,curl}
Check the PHP version:
php -v
Check if PHP is working
A quick way you can make sure that PHP works is by creating a simple PHP file in the Apache document root as follows.
Create a file in /var/www/html called phpinfo.php (it can be any name, it doesn’t matter)
sudo nano /var/www/html/phpinfo.php
And add the following line:
Save and close the file.
Now you can visit https://your_server_ip/phpinfo.php, and you’ll see something like:
Now remove the file since it can be used by malicious entities to see information about your server:
sudo rm /var/www/html/phpinfo.php
Install MySQL or MariaDB
MariaDB has been a drop-in replacement for MySQL for years; however, there are some differences. From my experience, both work for our purposes, but you still might want to check the differences to make an informed decision. This is an easily skimmable article on the topic – MariaDB vs MySQL: Key Performance Differences.
I typically go with MariaDB, but you can choose whichever you prefer.
MySQL
sudo apt -y install mysql-server
MariaDB
sudo apt -y install mariadb-server
MySQL/MariaDB comes with a script to set up your password to MySQL/MariaDB, as well as altering some less secure values. To start it run the following command:
sudo mysql_secure_installation
You’ll be asked for the current root MySQL password for root:
Enter current password for root (enter for none):
If you followed this tutorial, you haven’t set it yet, so go ahead and press Enter. You’ll be asked if you want to set a root password – press Y and Enter and set a new root MySQL password.
Validate Password Plugin
You can skip this section if you’re not prompted by the VALIDATE PASSWORD PLUGIN.
If you install MySQL (and not MariaDB), when you run mysql_secure_installation you may be asked if you want your password validated to make sure it’s strong.
This plugin will ask you to select from 3 levels of password strength to validate from, and depending on what you select, your password will be graded and shown to you so you can decide if you want to continue with it or try entering a different one.
VALIDATE PASSWORD PLUGIN can be used to test passwords and improve security. It checks the strength of password and allows the users to set only those passwords which are secure enough. Would you like to setup VALIDATE PASSWORD plugin? Press y|Y for Yes, any other key for No:
I typically select Y, but you can select No if you’re sure of your password.
If you select Y then you’ll be asked to select how strong your password should be.
There are three levels of password validation policy: LOW Length >= 8 MEDIUM Length >= 8, numeric, mixed case, and special characters STRONG Length >= 8, numeric, mixed case, special characters and dictionary file Please enter 0 = LOW, 1 = MEDIUM and 2 = STRONG: 2
In the example, I selected 2.
My password contains lowercase letters, uppercase letters, numbers, and symbols, and it’s over 8 characters. I get password strength 100 and decide I want to continue so I input Y.
Estimated strength of the password: 100 Do you wish to continue with the password provided?(Press y|Y for Yes, any other key for No) : Y
If after you continue with the password provided, you get the following error, then go to our troubleshooting section below:
... Failed! Error: SET PASSWORD has no significance for user 'root'@'localhost' as the authentication method used doesn't store authentication data in the MySQL server. Please consider using ALTER USER instead if you want to change authentication parameters.
Next, you’ll be asked if you want to remove anonymous users, restrict remote root user access to the local machine, remove test databases, and reload tables. Answer y/Y and press enter for Yes to each – unless you have a good reason not to.
Remove anonymous users:
Remove anonymous users? [Y/n] y ... Success!
Disallow root login remotely:
Disallow root login remotely? [Y/n] y ... Success!
Remove the test database:
Remove test database and access to it? [Y/n] y - Dropping test database... ... Success! - Removing privileges on test database... ... Success!
Reload privilege tables:
Reload privilege tables now? [Y/n] y ... Success! Cleaning up...
Now MySQL (or MariaDB) has been installed on your system, and we can proceed with configuring FreeRADIUS to use it.
Install FreeRADIUS and Configure with MySQL/MariaDB on Ubuntu 22.04/20.04
Install FreeRADIUS along with two modules that FreeRADIUS will need:
- freeradius-mysql – MySQL module for FreeRADIUS, so the server can do accounting and authentication using MySQL.
- freeradius-utils – a module that adds additional useful features to the FreeRADIUS server
sudo apt -y install freeradius freeradius-mysql freeradius-utils -y
Test the FreeRADIUS Server
FreeRADIUS is expected to run well with the default configuration.
To quickly check that FreeRADIUS and up and running, we’ll run it in debug mode.
Stop the FreeRADIUS server, as it started automatically after installing it.
sudo systemctl stop freeradius
Run FreeARDIUS in debug mode (remember to use sudo):
sudo freeradius -X
The output should look something like this:
Listening on auth address * port 1812 bound to server default Listening on acct address * port 1813 bound to server default Listening on auth address :: port 1812 bound to server default Listening on acct address :: port 1813 bound to server default Listening on auth address 127.0.0.1 port 18120 bound to server inner-tunnel Listening on proxy address * port 52868 Listening on proxy address :: port 57983 Ready to process requests
Stop debug mode by pressing Ctrl+C.
Start and enable FreeRADIUS service so it runs on system boot:
sudo systemctl enable --now freeradius
Allow FreeRADIUS in Firewall
(If you have UFW running on Ubuntu 22.04/20.04)
FreeRADIUS uses UDP ports 1812 for authentication and 1813 for accounting. You need to make sure those ports are allowed. The method by which you allow them can also depend on the platform you’re using.
If you’re using UFW, then you can open them by running:
sudo ufw allow to any port 1812 proto udp sudo ufw allow to any port 1813 proto udp
Configure FreeRADIUS to use MySQL/MariaDB
We’ll create a database and a database user for FreeRADIUS to use.
You can use any credentials you like, but make sure to remember to replace the credentials that I’m using with your own throughout the rest of the tutorial.
The details we’ll use are:
Database: radius
User: radius
Password: Somestrongpassword_321
To begin, access the MySQL/MariaDB console as root by running the following command and then inputting your password at the prompt:
sudo mysql -u root -p
Create a database and user that will be used by FreeRADIUS:
CREATE DATABASE radius; CREATE USER 'radius'@'localhost' IDENTIFIED by 'Somestrongpassword_321'; GRANT ALL PRIVILEGES ON radius.* TO 'radius'@'localhost'; FLUSH PRIVILEGES; quit;
Now, to populate the database with the RADIUS MySQL schema.
First, we’ll have to switch to using the root user, otherwise, we get Access denied when trying to import, even if we’re using sudo:
sudo su -
Now import the RADIUS MySQL schema:
mysql -u root -p radius < /etc/freeradius/3.0/mods-config/sql/main/mysql/schema.sql
Let’s switch back to our non-root user (I’m using edxd so I’ll switch to that):
sudo su - edxd
You can check the tables just created in the radius database by running the following command and then entering your root MySQL/MariaDB password:
sudo mysql -u root -p -e "use radius;show tables;"
Output:
+------------------+ | Tables_in_radius | +------------------+ | nas | | radacct | | radcheck | | radgroupcheck | | radgroupreply | | radpostauth | | radreply | | radusergroup | +------------------+
Create a soft link to the SQL module to /etc/freeradius/3.0/mods-enabled:
sudo ln -s /etc/freeradius/3.0/mods-available/sql /etc/freeradius/3.0/mods-enabled/
Next, we configure FreeRADIUS to use SQL. To do this open /etc/freeradius/3.0/mods-enabled/sql using your favorite text editor, so we can edit some parameters.
I’ll install and use nano as my text editor and open the file:
sudo apt install nano sudo nano /etc/freeradius/3.0/mods-enabled/sql
There’s quite a bit of text, but most of it is commented out. We’ll just need to edit a few things.
- Change dialect = "sqlite" to dialect = "mysql"
- Change driver = "rlm_sql_null" to driver = "rlm_sql_${dialect}"
- If we use MySQL the FreeRADIUS configuration assumes the use of TLS certs by default. For the purpose of this tutorial, we won’t be using TLS certs, so we’ll comment out the MySQL TLS section by adding a # sign in at the beginning of every line in the tls section. The TLS section looks something like this:
mysql { # If any of the files below are set, TLS encryption is enabled tls { ca_file = "/etc/ssl/certs/my_ca.crt" ca_path = "/etc/ssl/certs/" certificate_file = "/etc/ssl/certs/private/client.crt" private_key_file = "/etc/ssl/certs/private/client.key" cipher = "DHE-RSA-AES256-SHA:AES128-SHA" tls_required = yes tls_check_cert = no tls_check_cert_cn = no } # If yes, (or auto and libmysqlclient reports warnings are # available), will retrieve and log additional warnings from # the server if an error has occured. Defaults to 'auto' warnings = auto }And this is how it looks with the TLS section commented out:
mysql { # If any of the files below are set, TLS encryption is enabled # tls { # ca_file = "/etc/ssl/certs/my_ca.crt" # ca_path = "/etc/ssl/certs/" # certificate_file = "/etc/ssl/certs/private/client.crt" # private_key_file = "/etc/ssl/certs/private/client.key" # cipher = "DHE-RSA-AES256-SHA:AES128-SHA" # tls_required = yes # tls_check_cert = no # tls_check_cert_cn = no #} # If yes, (or auto and libmysqlclient reports warnings are # available), will retrieve and log additional warnings from # the server if an error has occured. Defaults to 'auto' warnings = auto } - Next, we’ll uncomment the Connection info section and add in the connection details to our MySQL/MariaDB database. First, uncomment (remove the # signs) from the beginning of the lines starting with server, port, login, and password.
server– this is the server where the database is located. In this case, it’s the local server, so we can leave “localhost”
port– is set to 3306, which is the default port for the classic MySQL protocol. Leave it as is unless you have changed the MySQL port.
login– this is the database user you created earlier for FreeRADIUS to use. I created the user radius, so I’ll leave it as is. You change it if your user is something else.
password– the password for that MySQL user that you also set earlier. This is its initial state:# Connection info: # # server = "localhost" # port = 3306 # login = "radius" # password = "radpass"
And here it is edited.
# Connection info: # server = "localhost" port = 3306 login = "radius" password = "Somestrongpassword_321"
- A few lines lower, we need to configure the name of the database. By default, it looks like this:
# Database table configuration for everything except Oracle radius_db = "radius"
Instead of radius, input the database you created. Since I created the database radius, I’ll leave it as is:
# Database table configuration for everything except Oracle radius_db = "radius"
- Further down, we’ll uncomment a line containing read_clients = yes. This is to enable FreeRADIUS to read clients from the database.Here is how it looks:
# Set to 'yes' to read radius clients from the database ('nas' table) # Clients will ONLY be read on server startup. # read_clients = yesJust remove the # sign to uncomment it:
# Set to 'yes' to read radius clients from the database ('nas' table) # Clients will ONLY be read on server startup. read_clients = yes - Just a few lines lower, we want client_table = “nas” to be uncommented. It should be uncommented by default, but just check to make sure it looks like this:
# Table to keep radius client info client_table = "nas"
Now change the group rights of the file we just edited:
sudo chgrp -h freerad /etc/freeradius/3.0/mods-available/sql sudo chown -R freerad:freerad /etc/freeradius/3.0/mods-enabled/sql
And restart the FreeRADIUS service:
sudo systemctl restart freeradius.service
Since we’ve done quite a few edits, we should run FreeRADIUS in debug mode so we know if we made any mistake, before going further.
First, stop the FreeRADIUS service since we can’t have 2 instances of the service running simultaneously:
sudo systemctl stop freeradius.service
And run FreeRADIUS in debug mode:
sudo freeradius -X
The output looks something like this:
Listening on auth address * port 1812 bound to server default Listening on acct address * port 1813 bound to server default Listening on auth address :: port 1812 bound to server default Listening on acct address :: port 1813 bound to server default Listening on auth address 127.0.0.1 port 18120 bound to server inner-tunnel Listening on proxy address * port 52025 Listening on proxy address :: port 42807 Ready to process requests
Exit debug mode by pressing Ctrl+C and then start FreeRADIUS again by running:
sudo systemctl start freeradius.service
Now FreeRADIUS is installed on your Ubuntu 22.04/20.04 machine and is configured to work with MySQL or MariaDB.
Next, we’ll install daloRADIUS, which is a web control panel to manage our FreeRADIUS server. This step is optional, for those who want a GUI for their FreeRADIUS server.
Install & Configure daloRADIUS (FreeRADIUS GUI) on Ubuntu 22.04/20.04 (Optional)
First, we’ll download daloRADIUS from the Github repository.
I’ll use wget to download it, so I’ll have to install it since it’s not installed by default and unzip it since we’ll be downloading a .zip file:
sudo apt -y install wget unzip
Now download daloRADIUS and cd into the newly created daloradius-1.3 folder:
wget https://github.com/lirantal/daloradius/archive/1.3.zip unzip 1.3.zip cd daloradius-1.3
Populate the database with the daloRADIUS schema:
sudo mysql -u root -p radius < contrib/db/fr2-mysql-daloradius-and-freeradius.sql sudo mysql -u root -p radius < contrib/db/mysql-daloradius.sql
cd out of the daloradius-1.3 directory, and move the folder into the document root as daloradius:
cd .. sudo mv daloradius-1.3 /var/www/html/daloradius
Next, we’ll change the owner and group for the daloradius folder to www-data:www-data, which are the user and group under which the Apache Web Server runs.
sudo chown -R www-data:www-data /var/www/html/daloradius/
Now, we’ll need to create the daloRADIUS configuration file. Right now, we’re just provided a sample file, so we’ll make a copy from that sample file:
sudo cp /var/www/html/daloradius/library/daloradius.conf.php.sample /var/www/html/daloradius/library/daloradius.conf.php
We’ll also change the permissions for the daloRADIUS configuration file:
sudo chmod 664 /var/www/html/daloradius/library/daloradius.conf.php
Next, we edit a few variables in the daloRADIUS connection file so it can connect to the FreeRADIUS database.
Open the configuration file using your favorite editor:
sudo nano /var/www/html/daloradius/library/daloradius.conf.php
Similarly to what we’ve done earlier when editing the FreeRADIUS config file, we need to adjust the variables for the database user, their password, and the database name. Those are all the edits for the scope of this tutorial.
This is how they initially look in the daloRADIUS configuration file:
$configValues['CONFIG_DB_USER'] = 'root'; $configValues['CONFIG_DB_PASS'] = ''; $configValues['CONFIG_DB_NAME'] = 'radius';
This is how it looks after editing the details for the database I created earlier:
$configValues['CONFIG_DB_USER'] = 'radius'; $configValues['CONFIG_DB_PASS'] = 'Somestrongpassword_321'; $configValues['CONFIG_DB_NAME'] = 'radius'
Lastly, restart FreeRADIUS and Apache to make sure everything works:
sudo systemctl restart freeradius.service apache2
Access daloRADIUS
You can access daloRADIUS through a web browser by visiting:
http://server_ip_address/daloradius
Make sure it’s http:// and that your browser doesn’t automatically change it to https:// because you may not be able to access daloRADIUS since we haven’t configured it to use SSL.
The daloRADIUS start page looks something like this:
Default daloRADIUS username/password:
username: administrator password: radius
Change daloRADIUS username & password
Having default credentials such as administrator/radius is a security vulnerability, and there are bots that scan absolutely all IPs and try known default credentials for certain software.
In this manner, someone can scan all of the possible IPs, and they’re trying to detect if daloRADIUS is installed by visiting http://random_ip/daloradius and they’ll try out to log in using administrator/radius, and chances are they’ll succeed some of the time because some people don’t change their default credentials.
You can change a user password by logging into daloRADIUS > Config (In the top menu) > Operators (In the submenu) > List Operators (In the gray sidebar) > Click on user (in our case administrator) and in the next screen change the password and click Apply.
[Video] Change daloRADIUS Administrator Password
To create a new daloRADIUS user (called Operator), go to Config > Operators (in the submenu) > New Operator (in the gray sidebar) > input Operator Username and Operator Password and click Apply.
[Video] Create New daloRADIUS Operator
To get acquainted with daloRADIOUS, next, we’ll create a NAS Client Table and a user.
We have created an online tool to test the Authentication and Accounting of radius servers.
Testing FreeRADIUS & daloRADIUS
For the last part of this tutorial, we’ll test our FreeRADIUS server and the daloRADIUS web panel.
In short, we’ll send an Authentication Request from another computer to our server to see if it works.
To do this, we’ll need to add a NAS (explanation below), a User, and another computer from where to send the request (this can be your computer, for example).
Note: We have created an online radius testing tool for this purpose.
1. Creating a NAS Client Table in daloRADIUS
For another computer to use our RADIUS server, it first needs to be added to the NAS Client Table.
The Network Access Server (NAS) client table acts as a gateway that guards a protected resource. For another computer to connect to our RADIUS server, it needs to be added to the NAS client table.
The NAS is an intermediary that a client connects to, then the NAS asks the resource (in our case, the RADIUS server) if the credentials are valid, and based on this, the NAS will allow or disallow access to the protected resource.
You can read a bit more about the NAS on this page from the FreeRADIUS wiki.
To add a NAS, go in the daloRADIUS dashboard, Management > NAS (in the blue submenu) > New NAS (in the left, dark gray, sidebar).
NAS IP/Host: the IP or fully qualified hostname from which you’re trying to connect. To allow all, set it “0.0.0.0/0″
NAS Secret: a password for connecting to the NAS, but it’s referred to as a secret. It’s used to communicate between the client/NAS and RADIUS server.
NAS Type: There are a few types that are recognized, including livingston, cisco, portslave. This is passed to the external checklogin program when it is called to detect double logins. For the purposes of this tutorial, we’ll select other.
NAS Shortname: An alias that can be used in place of the IP address or fully qualified hostname provided under NAS IP/Host
For our example, we’ll fill in the following:
NAS IP/Host: IP of another computer we’re using as a client (for testing, you can set it 0.0.0.0/0 to allow all)
NAS Secret: nobodywilleverlearnthissecret!!11!!
NAS Type: other
NAS Shortname: ProductionServer
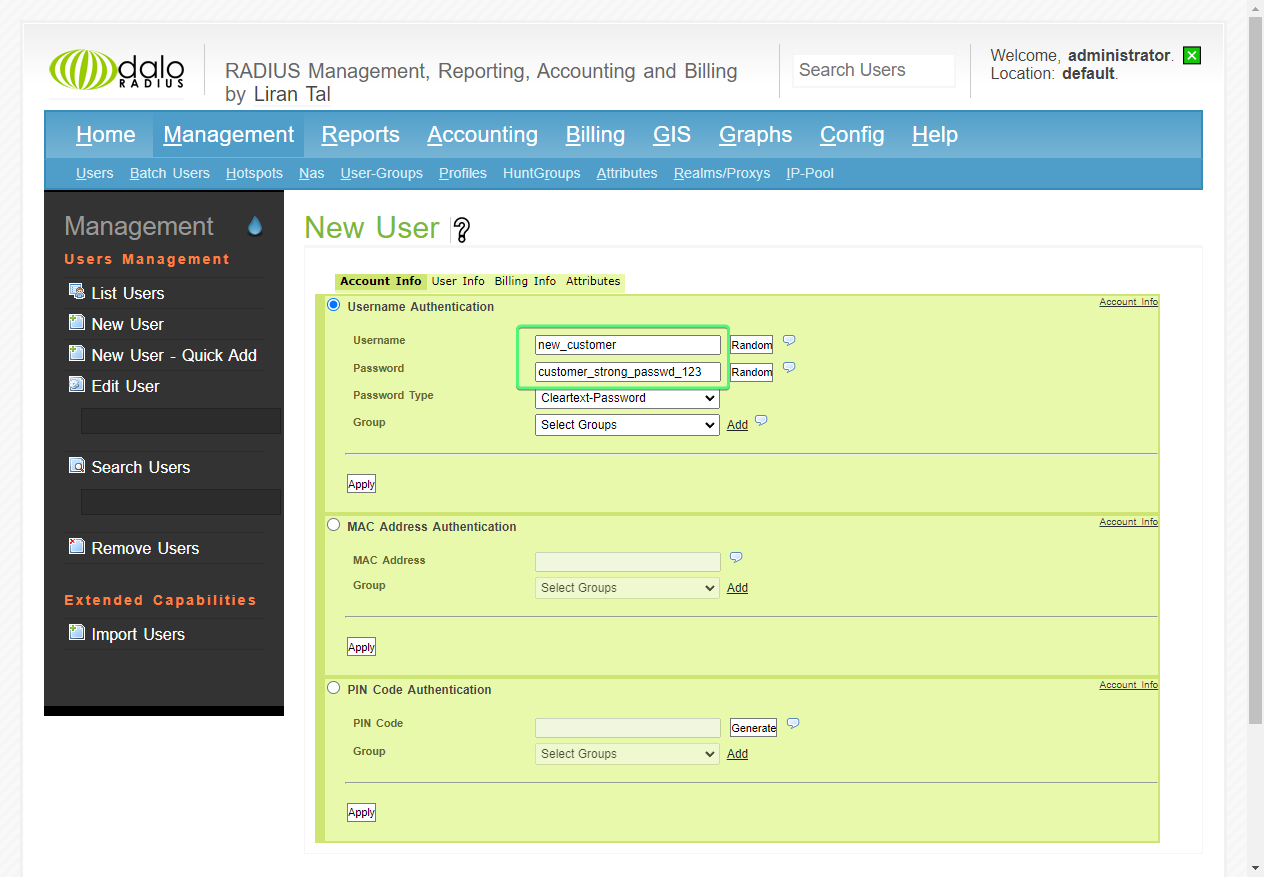
2. Creating a User in daloRADIUS
To test our RADIUS server, we’ll also need to have a user.
We can easily create one by navigating in the top menu to Management > Users (in the blue submenu) >New User (in the left, dark gray sidebar)
For our example, all we need is a Username and Password. There are other attributes, but these will be enough for our purposes.
I’ll fill in the following:
Username: new_customer
Password: customer_strong_passwd_123
3. Run FreeRADIUS in Debug Mode
We want to see for ourselves what’s happening on the server, so we’ll run FreeRADIUS in debug mode.
First stop the running process:
sudo systemctl stop freeradius.service
Run the following command to run FreeRADIUS debug mode:
sudo freeradius -X
Every time a new NAS is added, you need to restart FreeRADIUS so it fetches the updated table.
We’re already doing this in this demo since we’re stopping it and running it in debug mode, but you should remember this in the future.
Now, we’re ready to test the server.
4. Test daloRADIUS with Bytexd Radius Tester
For convenience, we’ve created an online radius testing tool, located at https://bytexd.com/tools/radius/auth-acct-tester
This is what it looks like and how we’ll fill in the details in Bytexd Radius Tool. We’ll use it to send an Authentication Request to the RADIUS server while it’s running in debug mode so we can see firsthand how it accepts the request.

We’ve filled the fields as follows:
RADIUS Server/port: IP of the server we have FreeRADIUS installed on / port 1812
Reply timeout (sec.): 1
Retries: 1
RADIUS Secret key: nobodywilleverlearnthissecret!!11!!
User-Name: new_customer
Password: customer_strong_passwd_123
Now, you can test the RADIUS server. Just click Submit, and if you get an Access-Accept response, we can assume it’s working.
The output in the tester should look something like this:
Sending authentication request to server 40.76.122.52:1812 transmiting Packet, code=1 id=3 length=53 recieved response from the server in 16 milliseconds replay packet code=2 id=3 length=20 response: Access-Accept -------------------attribute dump------------------
And the output in the terminal, where you’re running FreeRADIUS in debug mode, should end with something like this:
... (2) Sent Access-Accept Id 7 from 10.0.2.4:1812 to 213.136.66.127:52163 length 0 (2) Finished request Waking up in 4.9 seconds. (2) Cleaning up request packet ID 7 with timestamp +67 Ready to process requests
Enable TLS/SSL with MySQL and FreeRADIUS
In the above example, we commented out the tls section of the SQL module config file.
Check MySQL SSL Status
First, we’ll need to check if the SSL status of MySQL is enabled or disabled. To do that run the following to use the MySQL console and enter the root MySQL password when prompted.
mysql -u root -p
Next, run the following command to check the SSL status:
SHOW GLOBAL VARIABLES LIKE '%ssl';
If you’ve followed this tutorial until now, then the output should look like this:
+---------------+-------+ | Variable_name | Value | +---------------+-------+ | have_openssl | YES | | have_ssl | YES | +---------------+-------+ 2 rows in set (0.01 sec)
That means the status is enabled, otherwise the value column would say DISABLED.
Configure FreeRADIUS MySQL SSL
Next, we’ll copy our ca.pem certificate file into the certificates folder /etc/ssl/certs:
sudo cp /var/lib/mysql/ca.pem /etc/ssl/certs/ca.pem
Finally, we’ll go back into our FreeRADIUS SQL module configuration file and change:
mysql {
# If any of the files below are set, TLS encryption is enabled
#tls {
# ca_file = "/etc/ssl/certs/my_ca.crt"
# ca_path = "/etc/ssl/certs/"
# certificate_file = "/etc/ssl/certs/private/client.crt"
# private_key_file = "/etc/ssl/certs/private/client.key"
# cipher = "DHE-RSA-AES256-SHA:AES128-SHA"
# tls_required = yes
# tls_check_cert = no
# tls_check_cert_cn = no
}
To:
mysql {
# If any of the files below are set, TLS encryption is enabled
tls {
ca_file = "/etc/ssl/certs/ca.pem"
ca_path = "/etc/ssl/certs/"
# certificate_file = "/etc/ssl/certs/private/client.crt"
# private_key_file = "/etc/ssl/certs/private/client.key"
cipher = "DHE-RSA-AES256-SHA:AES128-SHA"
tls_required = yes
tls_check_cert = no
tls_check_cert_cn = no
}
# If yes, (or auto and libmysqlclient reports warnings are
# available), will retrieve and log additional warnings from
# the server if an error has occured. Defaults to 'auto'
warnings = auto
}
Remember to replace /etc/ssl/certs/my_ca.crt to /etc/ssl/certs/ca.pem.
That’s it. Now you can save it and restart the RADIUS server, and it should work.
Frequent Errors
“Failed binding with auth address […]” when running in debug mode
Failed binding to auth address * port 1812 bound to server default: Address already in use /etc/freeradius/3.0/sites-enabled/default[59]: Error binding to port for 0.0.0.0 port 1812
If you get the following error when running FreeRADIUS in debug mode, it most likely means that the FreeRADIUS service is already running and you need to stop it first.
$ sudo systemctl stop freeradius.service
“Error reading log file: /tmp/daloradius.log”
Make sure that the log file exists and has read/write permission set.
Failed! Error: SET PASSWORD has no significance for user ‘root’@’localhost
To fix this exit, the mysql_secure_installation setup. You’ll most likely have to terminate the session or the mysql_secure_installation process, because Ctrl+C and Ctrl+Z don’t work.
Log in to mysql by running
mysql
Once logged in, you’ll set your password from here instead of the secure installation script:
ALTER USER 'root'@'localhost' IDENTIFIED WITH mysql_native_password BY 'YOUR_PASSWORD'; exit;
Replace YOUR_PASSWORD with a password of your choosing.
Now you can run the mysql_secure_installation again and select n when asked if you want to set your MySQL password.
Conclusion
Well done. Hopefully, you successfully installed FreeRADIUS with MySQL or MariaDB, along with daloRADIUS, on your Ubuntu 22.04/20.04 machine.
If you’ve encountered any issues, then don’t hesitate to contact us in the comment section, email, or on social media, and we’ll try to assist as soon as possible.
Skip the setup and instantly deploy a pre-configured FreeRADIUS server with MySQL and daloRADIUS in seconds. Our solution is secure, fully configured, and designed to save you time.
Your servers, managed for you, so you can focus on your business.
Need a custom solution? Our expert team is available for hire. Feel free to contact us.






hello,
Following The installation manual i installed freeradius, mriadb along with daloradius after the installation i got error in the log section with daloradius and i attached it below.
error reading log file: /tmp/daloradius.log
looked for log file in /tmp/daloradius.log but couldn’t find it.
if you know where your daloradius log file is located, set it’s location in your library/daloradius.conf file
please can you help me how to correct it.
Hello,
Make sure that the file “/tmp/daloradius.log” exists and has the correct permissions set.
how can i fix this problem?
Do you have any guidance on how to add HTTPS to this installation?
Hi Howard,
Thanks for getting in touch.
I’ve been meaning to cover this but haven’t been able to do that yet.
I’m thinking this video tutorial may help https://www.youtube.com/watch?v=nFij84u8_Bw
Let me know if it works out?
Thanks, I will have a look at this. Many thanks, and great tutorial! Bookmarked your site ?
We’re happy to be of service. Thanks so much for the kind words! We very much appreciate it!
hi
when I login into Daloradius it show me
Database connection error
Error Message: DB Error: extension not found
and I used ubuntu20.04LTS, mysql8.0 Daloradius version 1.1-2 and Freeradius version 3.
thanks in advance.
Hi,
Apologies for the delay.
Did you install FreeRADIUS using this tutorial or different one?
Looking forward to hearing from you.
I have followed this tutorial, I have already install Freeradius and daloRADIUS with my sql. but when I tried to login thru daloRADIUS login page, it show error with database extension?
Hi,
Apologies for the delay,
I just went through the tutorial and installed MySQL instead of MariaDB and I’m not getting the error.
Did you manage to solve this?
Hi,
You have posted the exact same comment twice, so I’ll mark the other one with [duplicate comment].
Please let me know if you installed FreeRADIUS by following this tutorial or another tutorial, so I can try to determine the cause of the error.
Thanks!
[duplicate comment]
Hi sir,
i follow the process you mention above and made some modification like installing LAMP using this https://ubuntu.com/server/docs/lamp-applications and I am installing this in Lubuntu 18.04.
Everything went well EXCEPT the last part; using the NTRadPing.
The NAS secrect do not recognize the freeradius server. I try to look in google and give an answer by editing /etc/freeradius/3.0/clients.conf. example below:
client ray {
ipaddr = 192.168.254.0/24
secret = 123
}
Everything is working now and thing that question me is the NAS.
What is NAS?
What is the use of NAS?
Why NAS did not work in this particular.
Hi,
I tried to explain what a NAS is, and the use, etc. I’m thinking maybe this will help clarify? https://wiki.freeradius.org/glossary/NAS
In my mind I see NAS (Network Access Server) as me telling the FreeRADIUS: “Hey, so, don’t let anyone access our stuff if they don’t have this IP (NAS IP/Host) and this password (NAS secret)”.
I think that maybe the term NAS/Network Access Server just makes everything sound more complicated than it actually is, when you’re first exposed to this term. I’m just assuming.
Can you show me a screenshot of NTRadPing with private details blurred out if needed?
I just went through the tutorial to make sure everything works, and I didn’t get any errors.
Looking forward to hearing from you.
thanks I did it.
Hi Alfredo,
Really happy to hear! I appreciate you letting us know. It’s nice knowing this article is useful. 😀
Hi,
thank you very much for tutorial.
I have installed freeradius, mariadb and daloradius by following this tutorial. GUI daloradius is not working. I can see login page but I end up with blank screen after login name and password insertion.
Thanks for the answer.
Hello,
I just went through the tutorial, in case some thing got messed up because of some update, and everything worked, including logging into daloRADIUS.
I have no solid arguments for this, but can you run:
`$ pear install DB`
And then run:
`$ sudo systemctl restart freeradius.service apache2`
Looking forward to hearing from you.
It did not help. The freeradius is working. I have inserted user and NAS by CLI. I have tested function with NTRadPing. But GUI Daloradius still not works. IE reports “This page is not working. HTTP error 500.”. What should be set for “SQL engine” in daloradius.conf.php – mysql?
I have set this:
include (dirname(__FILE__).’/version.php’);
$configValues[‘FREERADIUS_VERSION’] = ‘2’;
$configValues[‘CONFIG_DB_ENGINE’] = ‘mysqli’;
$configValues[‘CONFIG_DB_HOST’] = ‘localhost’;
$configValues[‘CONFIG_DB_PORT’] = ‘3306’;
$configValues[‘CONFIG_DB_USER’] = ‘radius’;
$configValues[‘CONFIG_DB_PASS’] = ‘P@ssw0rd’;
$configValues[‘CONFIG_DB_NAME’] = ‘radius’;
Hello,
Yes SQL Engine should be `$configValues[‘CONFIG_DB_ENGINE’] = ‘mysqli’;`
Apologies for the delay. I’ve been trying to find a solution for this but it’s difficult without being able to test out solutions.
Did you manage to solve it?
I can log into your machine and take a look if you’d like me to. Just let me know via email/twitter. It’s the most painless way I can think of, and I obviously understand if you prefer not to since you may be running a sensitive system and I’m a complete stranger.
Hello! Sorry to necro this year old comment chain, haha. We’re having this same issue! You weren’t able to find a solution were ya?
Thanks 🙂
Jacob
Hello,
/etc/freeradius/3.0/mods-enabled/sql[341]: Reference “${dialect}” not found
Errors reading or parsing /etc/freeradius/3.0/radiusd.conf
I get this error I followed the steps exactly
Hi Tech-lee,
I think this is because the CMS I’m using – WordPress – converts quotes (
"$dialect") to curly quotes (“${dialect}”).If you copy pasted these $dialect lines, then you must’ve copied them along with curly quotes:
Change dialect = “sqlite” to dialect = “mysql” Change driver = “rlm_sql_null” to driver = “rlm_sql_${dialect}”My apologies, I should have caught onto that when writing the tutorial. I was used to this happening on other websites as well, and I overlooked it. It should be fixed now.
Could you
sudo nano /etc/freeradius/3.0/mods-enabled/sqland make the following edits and try again:Change dialect = "sqlite" to dialect = "mysql" Change driver = "rlm_sql_null" to driver = "rlm_sql_${dialect}"I went through the tutorial again and it works for me.
Looking forward to hearing from you.
Hi, i changed sql file to
Change dialect = “{sqlite}” to dialect = “{mysql}”
Change driver = “rlm_sql_null” to driver = “rlm_sql_${dialect}”
# driver = “rlm_sql_null”
driver = “rlm_sql_${dialect}”
And now i have this, after radiusd -X
/etc/raddb/mods-enabled/sql[63]: Expecting section start brace ‘{‘ after “Change dialect”
Errors reading or parsing /etc/raddb/radiusd.conf
Can you help me ?
Hi,
I’m not sure, since I never encountered this. Can you paste a screenshot of the area surrounding driver = “rlm_sql_${dialect}”, please?
hello i have the same problem
here is the conf file
And the result
Hi, can you paste your conf file on https://pastebin.com with any sensitive data removed? I’d like to try it out myself. Thanks!
Yes, here is the link : https://pastebin.com/kpXLcfSE
It seems a closing brace is commented out on line 152. I uncommented it and it worked.
Let know if it works? And thank you for commenting!
On a different note, I see you commented out the tls { } block from mongo, instead of the tls block from mysql. Just pointing that out in case you missed that.
perfect thank you
Thanks so much for the update! Happy to help!
I followed your tutorial. All is well, until Part 4: Test daloRADIUS with NTRadPing
What IP address should I fill in this instruction of yours:
I am confused, since in NTRadPing, I entered the IP address 127.0.0.1 port 1812, since:
I did the step of checking access to Apache by visiting the server’s IP or hostname at http://127.0.0.1 and the step of checking if PHP is working at http://127.0.0.1/phpinfo.php
Fyi, I use Ubuntu 20.04 in VMWare, using my Windows PC. I also use NTRadPing in the same Windows PC.
Hi Haq Fadil,
I suspect that the problem is accessing the VMWare machine. I haven’t tried connecting from a host Windows machine to a VMWare Linux guest, so I’m also trying to figure this out.
When you say that you accessed Apache by visiting
http://127.0.0.1, did you successfully access it from your Windows PC?No, the part where I accessed Apache is from Ubuntu on VMWare
I see. I wanted to make sure.
So it sounds like what you want now is to connect from your host (Windows PC) to your guest (Ubuntu VMWare).
I don’t have experience with this, I’m afraid. I tried a few things earlier but couldn’t get it to work and I don’t have a solution right now.
The best I can do at the moment is recommend you Google things like access guest localhost from host vmware. I don’t think the guest VM and the Windows PC share the same localhost.
Do you absolutely have to use a VMWare VM for this?
Oh, I see… anyway, thanks for the response & recommendation. For that question, actually I use VMWare for this project since I’m not familiar with using Virtual Box. Also, I use virtualization instead of dualbooting my PC is because of a certain BIOS-related problem that may affect dualboot, so I’m not taking risks.
Hello,
All of steps are passed and everything is fine. But when I test the accounting with NTRadPing, the debug result is showing like below.
sql: ERROR: rlm_sql_mysql: ERROR 1054 (Unknown column ‘acctupdatetime’ in ‘field list’): 42S22
And that user are showing offline on Dalo web GUI, even user is online.
Can someone have the solution and help me ?
Hello,
I’ve seen this happen sometimes and I’m not sure why. For some reason the radacct table is missing the acctupdatetime field.
Can you alter the radacct table in the radius database?
Log into MySQL:
Once logged in use the radius database:
And then add acctupdatetime:
Hello,
Thanks on your reply. After I did as your instruction “acctupdatetime” db errror is OK . But another column in field list (framedipv6address , framedipv6prefix, framedinterfaceid, delegatedipv6prefix) are still facing error like below.
sql: ERROR: rlm_sql_mysql: ERROR 1054 (Unknown column ‘framedipv6address’ in ‘field list’): 42S22
sql: ERROR: rlm_sql_mysql: ERROR 1054 (Unknown column ‘framedipv6prefix’ in ‘field list’): 42S22
sql: ERROR: rlm_sql_mysql: ERROR 1054 (Unknown column ‘framedinterfaceid’ in ‘field list’): 42S22
sql: ERROR: rlm_sql_mysql: ERROR 1054 (Unknown column ‘delegatedipv6prefix’ in ‘field list’): 42S22
I fixed as below (drop and create new) fand all errors are resolved as now and I can see the accounting session and user online/offline well.
And can you guess, that below way are good for future ?
Mean any other error still can happens ?
use radius;
DROP TABLE radacct;
CREATE TABLE radacct (
radacctid bigint(21) NOT NULL auto_increment,
acctsessionid varchar(64) NOT NULL default ”,
acctuniqueid varchar(32) NOT NULL default ”,
username varchar(64) NOT NULL default ”,
groupname varchar(64) NOT NULL default ”,
realm varchar(64) default ”,
nasipaddress varchar(15) NOT NULL default ”,
nasportid varchar(15) default NULL,
nasporttype varchar(32) default NULL,
acctstarttime datetime NULL default NULL,
acctupdatetime datetime NULL default NULL,
acctstoptime datetime NULL default NULL,
acctinterval int(12) default NULL,
acctsessiontime int(12) unsigned default NULL,
acctauthentic varchar(32) default NULL,
connectinfo_start varchar(50) default NULL,
connectinfo_stop varchar(50) default NULL,
acctinputoctets bigint(20) default NULL,
acctoutputoctets bigint(20) default NULL,
calledstationid varchar(50) NOT NULL default ”,
callingstationid varchar(50) NOT NULL default ”,
acctterminatecause varchar(32) NOT NULL default ”,
servicetype varchar(32) default NULL,
framedprotocol varchar(32) default NULL,
framedipaddress varchar(15) NOT NULL default ”,
framedipv6address varchar(15) NOT NULL default ”,
framedipv6prefix varchar(15) NOT NULL default ”,
framedinterfaceid varchar(15) NOT NULL default ”,
delegatedipv6prefix varchar(15) NOT NULL default ”,
PRIMARY KEY (radacctid),
UNIQUE KEY acctuniqueid (acctuniqueid),
KEY username (username),
KEY framedipaddress (framedipaddress),
KEY acctsessionid (acctsessionid),
KEY acctsessiontime (acctsessiontime),
KEY acctstarttime (acctstarttime),
KEY acctinterval (acctinterval),
KEY acctstoptime (acctstoptime),
KEY nasipaddress (nasipaddress)
) ENGINE = INNODB;
exit;
Anyway, very thank to you.
Hello,
Happy to hear you were able to fix it!
I think you fixed it and I don’t think you’ll get this error again on this server.
Hi, I’ve reached the ‘Access DaloRADIUS’ step and http://192.168.xx.yy/daloradius redirects to a 404. I can’t seem to find anyone else having this issue on the net. I’ve successfully run freeradius -X with no errors.
I have Librenms running on the same server which is using a config file in the sites-enabled folder inside the Apache2. I believe this may be what is causing the issue. Any ideas on how to remedy this?
You have to put this address and it will start:
“http://192.168.xx.yy/daloradius/login.php”
Thank you for the tutorial, its work well.
Happy to help! Thank you for letting us know!
hello, please help on how to resolve error below
ERROR: (3) eap_peap: ERROR: TLS Alert write:fatal:protocol version
Error: tls: TLS_accept: Error in error
Auth: (5) Login incorrect (eap_peap: TLS Alert write:fatal:protocolversion)
This is the best explained tutorial that has worked for me. Thanks for your detailed explanations and screenshots.
I’m thrilled to hear it was useful to you! Thank you so much for the kind words! They’re greatly appreciated!
Good day. Thank you for the brilliant tutorial. I thoroughly enjoyed going through it. I encountered a problem on the last part on using the NTRadPing test utility. For some reason, I cannot get it to connect. I keep seeing this error in the FreeRADIUS debug screen:
Ready to process requests
Ignoring request to auth address * port 1812 bound to server default from unknown client 192.168.19.1 port 64129 proto udp
Interestingly, I can authenticate just fine when I use the built-in connectivity test tool within daloradius. Is there something I’m failing to do?
yes, same problem in my side.
For people having this problem: you need to comment everything inside <code>/etc/freeradius/3.0/clients.conf</code> and restart freeradius. Then it should work with both this tool and daloRADIUS check tool.
Same issue while working on a freeRADIUS dockerized solution with a Unifi controller request (ignoring request…). But running again freeRADIUS in debug mode i got:
The shared secret was correct. I had to:
Then it worked from inside the container (radtest -x client1 client1-pass 127.0.0.1 0 nas-shared-secret) and from my phone –> Unifi AP –> Unifi Controller –> freeRADIUS docker.
Would be nice to see an article on how to upgrade daloRADIUS only. Example from v. 1.2 to 1.3.
Interesting! I’ll look into it and post one as soon as I can. Thank you very much for the suggestion. It’s greatly appreciated!
Hello George,
This Tutorial was much better than anything i’ve searched for.
successfully installed and ran FreeRadius With MariaDB as well as the GUI
only if you could add some more references such as enabling TLS
Many Thanks,
Hi. Thank you for the kind words. It’s very much appreciated! You’re right, we should add a section on enabling TLS. Thank you for letting us know.
In the meantime perhaps you can try this vid on setting up SSL with MySQL and FreeRADIUS, it is very concise and I’m hoping it will help https://www.youtube.com/watch?v=nFij84u8_Bw
Let me know if it works out? Thanks again!
Hi,
Thank you for this great tutorial.
I have followed every step given and installed it successfully.
But now at the stage where I have to create NAS, I get this error:
Failed to add this new NAS [x . x . x . x ] to database.
I tried by adding both FQDN and IP as well.
Same thing happens when I try to add a user, I get the message that it can’t be added to database but when I reload the page, the data entered exists there.
Can you please few moments and guide me? If log is required , please let me know what and how can I provide that?
Will be grateful for your response.
Regards
Naeem
Hello Naeem
I have same problem with add new NAS
Did you find how to fix this?
Thank you very much Dear
i installed Dalo radius using your tutorial without a single error
Thank you Again For very Detailed Information
God Bless You
Hi,
I have an issue in FreeRADIUS with MySQL or MariaDB, along with daloRADIUS in Ubuntu 20.04 . In daloRADIUS Web Interface I cannot view the Sub Menu. Please see the attached Image for more detail.
DaloRADIUS Version : version 1.3 / 04 Nov 2021.
may I know cause of this issue?
Regards,
Prabath
Hi everything has gone well up until
sudo cp /var/www/html/daloradius/library/daloradius.conf.php.sample /var/www/html/daloradius/library/daloradius.conf.php
there is no library folder ; checked all the lines for any typos;
Thanks, i have found the same issue and still trying to figure out why its not in the sudo ls -l /var/www/html/daloradius/library/ but its in the sudo ls -l /var/www/html/daloradius/common/includes/
according to the latest changes committed 5 days ago https://github.com/lirantal/daloradius/commit/8cff70bd77d1277638019061919445ddb80f6379 there were some folder relocations. Have a look.
Hi
I appreciate you so much. I installed my Daloradius and freeradius server based on your instruction and it is working.
Thank you so much.
Regards
Hi, siavash! Thank you for the kind words! We’re glad to help!
i cannot create back ups and manage backups . When i try to crate backup the error show up that ”Failed creating backup due to directory/file permissions, check that the webserver user has access to create the following file: /var/www/daloradius/var/backup/backup-20230326-051431.sql
Worked first time. Unless I missed it, there is no section on setting up the SSL portion mentioned toward the end.
Auth: (0) Invalid user (sql: Failed to create the pair: Unknown name “Access-Period”): [BqbWc] (from client dockernet port 2 cli A6-3D-6F-BC-77-53)
my number whatsapp
+201004844489
hi
I use radius as authentication for the strongswan service, but when I try to log in using a client connection, it connects briefly and then reconnects repeatedly.
When I check the debug mode of radius, it shows “sql: error: rlm_sql_mysql: error 1054 (unknown column ‘acctupdatetime’ in ‘field list’): 42s22”
Then I cancel Change driver = “rlm_sql_null” to driver = “rlm_sql_${dialect}” and everything is back to normal
I wonder why this is and thank you very much for your contribution
(my english is not very good so i used google translate to write this, sorry)
Regards
I’m very sorry that I don’t know how to delete or reply to my above paragraph. But I have found a way to keep “driver=rlm_sql_${dialect}” and fix the problem: I refer to “https://serverfault.com/questions/1095415/daloradius-error-3-sql-error-rlm-sql -mysql-error-1054-unknown-column-acc” provided a workaround and solved the problem
Apologies for my stupidity and thanks again for your contribution, now it works great!
Regards
Hi, thanks for commenting and for the follow-up! I’m glad you were able to fix it!
This happens sometimes and I’m not clear why. It’s great that you commented because it helps others who have the same issue. Thanks again!
Hello,
I installed freeradius,mariadb everything look fine except graph doesn’t show up. is there anyone know how to fix it?
Hello, I followed the tutorial and I can access Daloradius correctly. When performing the test using the online tool available, I am unable to communicate with the server, the following message appears:
Sent Access-Request Id 136 from 0.0.0.0:35822 to 3.84.109.189:1812 length 45
User-Name = “test”
User-Password=”radius”
Cleartext-Password=”radius”
(0) No reply from server for ID 136 socket 3
I’m running an instance on AWS to do this test, I’ve already released the ports in the security group but I still can’t connect. Would I be able to help? Thank you and congratulations for the tutorial.
add this ip 3.84.109.189 to nas
Awesome work. Really, one of the best guide I ever used!
Hi, Paolo. Thanks for commenting and for the kind words! I’m glad it helped!
i got this error when testing the connectivity, can someone help?
same problem here…did you able to resolve it ?
I think you have create a use using cleartext password other type of passwords are not supported.
hello, your article is very good, but have you used multi schema database on freeradius, can you guide me on this case?
Hi, I have installed daloradius according to the steps above. I can make user and login from wifi. But my accounting is not working can you help.
thanks
Hi,
Thanks for the tutorial. I’m stuck in the testing of the user. I’m getting no reply from the server after submitting. What should be the issue?
Thank you.
log in to the Daloradius and go to management and list your IP as NAS
or if you are using their tool then stop the server sudo systemctl stop freeradius.service
then start the radius server in debug mode sudo freeradius -X and check the IP being ignored
then add that as NAS.
next reboot start server normally server sudo systemctl start freeradius.service
I prefer using Radtest on linux vm. you can donwload radtest utils
I hope this helps.
Hi George
A brilliant article and, as many have said, got me much further than anything else Ive found. I am sure that many of us really appreciate the work you put in here.
The only issue I have now is that I cannot get CHAP to work.
In the diag screen I get the following:
(0) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(0) Auth-Type CHAP {
(0) chap: ERROR: &control:Cleartext-Password is required for authentication
(0) [chap] = fail
(0) } # Auth-Type CHAP = fail
(0) Failed to authenticate the user
I have checked /etc/freeradius/3.0/sites-enabled/default and can confirm that CHAP is enabled.
I have not encrypted the database.
Any thoughts would be appreciated as this thing is so close to working.
Thanks a lot
Martin
the user password must be in clear text not chap
I have followed all the steps but I’m still getting this
Sent Access-Request Id 226 from 0.0.0.0:38002 to 127.0.0.1:1812 length 49
User-Name = “test.user”
User-Password = “Password”
Cleartext-Password = “Password”
(0) No reply from server for ID 226 socket 3
======
updating solution
Restart apache
sudo systemctl restart freeradius.service apache2
Hello All,
Can someone help to set up a corn job to restart apache as soon as a user is added to the DB?
using this command
sudo systemctl stop freeradius.service
Hello,
I did everything as you explained. I created a user from dalo and I am doing a test and it tells me the following.