[powerkit_collapsible title=”Not using Debian 10/Debian 11? Choose a different version or distro.”]
Ubuntu 20.04
CentOS 8
[/powerkit_collapsible]
FreeRADIUS is the most widely-deployed, open-source, and free RADIUS implementation. It works as a daemon (operates in the background) in Unix and Unix-like servers.
The RADIUS protocol allows you to authenticate users over a network, authorize them for various actions, and monitor their usage of the network. This framework is referred to as AAA (Authentication, Authorization, and Accounting).
According to a survey result, FreeRADIUS is used to authenticate over one-thirds of the users on the internet.
By default, FreeRADIUS has a command line interface, and any changes are made by editing the configuration files that are highly customizable. Since it’s open-source, you can even make changes in the code of the software.
Objectives
In this article, we will discuss how to install FreeRADIUS and daloRADIUS on Debian 10 and Debian 11, and how to configure it to use MySQL or MariaDB. We will also install and configure daloRADIUS, a web interface to manage FreeRADIUS.
Finally we will test our setup to make sure both the FreeRADIUS server and daloRADIUS are working properly.
Table of Contents
Prerequisites
- A server running Debian 10 or Debian 11 with a recommended minimum of 512MB RAM and at least 300MB free storage space.
- A non-root sudo user, because acting as root can cause harm to your system if you’re not careful. You can do everything and the system won’t ask. If you run a command to format a disk by mistake, then it’s done and you can destroy your system. Acting as a non-root sudo user has been the security model for years for good reason.
Skip the setup and instantly deploy a pre-configured FreeRADIUS server with MySQL and daloRADIUS in seconds. Our solution is secure, fully configured, and designed to save you time.
Your servers, managed for you, so you can focus on your business.
Need a custom solution? Our expert team is available for hire. Feel free to contact us.
Install LAMP Stack
LAMP stack is a very common web server stack named after its first four components Linux, Apache, MySQL, and PHP. LAMP stack can not only run static pages but also dynamic ones where the content can change anytime.
In the LAMP stack, the process starts at Apache when a user requests a web page. If the request is for a PHP file, then Apache forwards it to PHP, which loads the files and executes the code. PHP also collaborates with MySQL if it needs any data from the database. That all runs on the Linux operating system.
Although, LAMP stack was named after the original components, it’s no longer limited to the four components.
First update the package index:
sudo apt update
Install Apache
Apache also known as the Apache HTTP server is an open-source and free web server software. Apache has been around for over 20 years and powers nearly 40% of the websites around the world.
Despite the name, Apache is not a physical server, but a software that establishes a connection between the browser and server and delivers files to and from them. It’s a cross-platform software and works on both Windows and Unix servers.
Install Apache and enable it so it starts on boot:
sudo apt -y install apache2 sudo systemctl enable --now apache2
Make sure to allow it in your firewall. If you’re using UFW run the following command to allow it:
sudo ufw allow WWW
[powerkit_alert type=”info” dismissible=”false” multiline=”true”]Sidenote: If that does not work then the web server profile in UFW is probably called something else than WWW. You can also try sudo ufw allow Apache instead.[/powerkit_alert]
You can check if it’s working by visiting your server’s IP address in your browser. You should see something like the following screenshot:
Install MySQL/MariaDB
We often hear MySQL and MariaDB mentioned together, but the two database management systems are in fact different.
MySQL is an open-source relational database management system (RDBMS). It makes use of SQL (structured query language) to access, update, and manipulate data stored in the database. It also keeps the stored data organized.
MariaDB was developed in response to the rising concerns regarding the acquisition of MySQL by Oracle. It’s a fork of MySQL that was developed with the intention to keep the MySQL code free and open-source. It’s developed and maintained by the original developers of MySQL and uses the same database structure and indexes as MySQL. That way users can switch from MySQL to MariaDB without having to alter their application or losing data.
To install MySQL run:
sudo apt -y install mysql-server
Or to install MariaDB run:
sudo apt -y install mariadb-server
Secure MySQL/MariaDB by running the following script, which helps you remove less secure values:
sudo mysql_secure_installation
You’ll be asked to set a password if you haven’t already and then if you want to remove anonymous users, disallow root login remotely, remove the test database and reload tables. Unless you have other plans and know what you are doing, I recommend pressing Enter to all of those.
Validate Password Plugin (If you installed MySQL)
If you installed MySQL (and not MariaDB) you also go through a step where the script asks you if you want to set up the Validate Password Plugin, which basically helps you make sure that you’ve set up a strong password.
The instructions in the console should guide you through the process.
Now MySQL or MariaDB should be set up on your system.
Install PHP & Additional PHP Modules
Run the following command to install PHP and some additional PHP modules:
sudo apt -y install php libapache2-mod-php php-{gd,common,mail,mail-mime,mysql,pear,mbstring,xml,curl}
Check the PHP version to make sure the installation was successful:
php -v
My output:
PHP 7.3.27-1~deb10u1 (cli) (built: Feb 13 2021 16:31:40) ( NTS )
Copyright (c) 1997-2018 The PHP Group
Zend Engine v3.3.27, Copyright (c) 1998-2018 Zend Technologies
with Zend OPcache v7.3.27-1~deb10u1, Copyright (c) 1999-2018, by Zend Technologies
Install FreeRADIUS
Run the following command to install FreeRADIUS along with two additional modules we’ll need, freeradius-utils and freeradius-mysql:
sudo apt -y install freeradius freeradius-mysql freeradius-utils -y
Allow FreeRADIUS in Firewall
If you’re using a firewall, make sure to allow access to ports 1812 and 1813, which are used by RADIUS.
On Debian, if you’re using UFW run the following to allow access:
sudo ufw allow to any port 1812 proto udp sudo ufw allow to any port 1813 proto udp
Test the RADIUS Server
We’ll quickly run the RADIUS server in debug mode to check if we get any errors.
First stop FreeRADIUS:
sudo systemctl stop freeradius
And run it in debug mode:
sudo freeradius -X
The output should be quite long and end with something like this:
Listening on auth address * port 1812 bound to server default Listening on acct address * port 1813 bound to server default Listening on auth address :: port 1812 bound to server default Listening on acct address :: port 1813 bound to server default Listening on auth address 127.0.0.1 port 18120 bound to server inner-tunnel Listening on proxy address * port 37040 Listening on proxy address :: port 54623 Ready to process requests
Configure FreeRADIUS to Use MySQL/MariaDB
By default FreeRADIUS isn’t configured to use MySQL or MariaDB. We’ll change that.
First we’ll create a new database and credentials for it, whichFreeRADIUS will use.
We’ll use the following database name and credentials:
Database name: radius_db
Database User: radius_user
Database User Password: Somestrongpassword_321
Log into MySQL or MariaDB as root by running the following command, then fill in the root MySQL password when prompted:
sudo mysql -u root -p
Create the database and credentials that will be used by FreeRADIUS:
MariaDB [(none)]> CREATE DATABASE radius_db; MariaDB [(none)]> CREATE USER 'radius_user'@'localhost' IDENTIFIED BY 'Somestrongpassword_321'; MariaDB [(none)]> GRANT ALL ON radius_db.* TO radius_user@localhost IDENTIFIED BY "Somestrongpassword_321"; MariaDB [(none)]> FLUSH PRIVILEGES; MariaDB [(none)]> quit;
Next we’ll import the RADIUS MySQL schema provided by FreeRADIUS.
Switch to root for this operation, otherwise, you may get Access denied when trying to import:
sudo su -
Now import the MySQL schema into the database you created earlier (radius_db) by running the following command:
mysql -u root -p radius_db < /etc/freeradius/3.0/mods-config/sql/main/mysql/schema.sql
It should now be imported. Now let’s switch back to your non-root sudo user:
sudo su - edxd
You can now check the tables in the database to confirm the schema has been imported:
sudo mysql -u root -p -e "use radius_db;show tables;"
Example output when checking the tables in the radius_db database:
+------------------+ | Tables_in_radius_db | +------------------+ | nas | | radacct | | radcheck | | radgroupcheck | | radgroupreply | | radpostauth | | radreply | | radusergroup | +------------------+
Create a symbolic link from the SQL module into the /etc/freeradius/3.0/mods-enabled directory:
sudo ln -s /etc/freeradius/3.0/mods-available/sql /etc/freeradius/3.0/mods-enabled/
Next, we configure FreeRADIUS to use MySQL/MariaDB. To do this we edit /etc/freeradius/3.0/mods-available/sql with our favorite text editor. I’ll use nano:
sudo apt install nano sudo nano /etc/freeradius/3.0/mods-enabled/sql
We’ll make the following edits:
- Change
driver = "rlm_sql_null"todriver = "rlm_sql_mysql" - Change
dialect = "sqlite"todialect = "mysql" - FreeRADIUS assumes that we’ll be using TLS certs by default, if we switch to MySQL. Setting them up is beyond the scope of this tutorial, so we’ll comment out the TLS section.This is how it looks initially:
mysql { # If any of the files below are set, TLS encryption is enabled tls { ca_file = "/etc/ssl/certs/my_ca.crt" ca_path = "/etc/ssl/certs/" certificate_file = "/etc/ssl/certs/private/client.crt" private_key_file = "/etc/ssl/certs/private/client.key" cipher = "DHE-RSA-AES256-SHA:AES128-SHA" tls_required = yes tls_check_cert = no tls_check_cert_cn = no } # If yes, (or auto and libmysqlclient reports warnings are # available), will retrieve and log additional warnings from # the server if an error has occured. Defaults to 'auto' warnings = auto }And this is how it looks after we’ve commented it out:
mysql { # If any of the files below are set, TLS encryption is enabled # tls { # ca_file = "/etc/ssl/certs/my_ca.crt" # ca_path = "/etc/ssl/certs/" # certificate_file = "/etc/ssl/certs/private/client.crt" # private_key_file = "/etc/ssl/certs/private/client.key" # cipher = "DHE-RSA-AES256-SHA:AES128-SHA" # tls_required = yes # tls_check_cert = no # tls_check_cert_cn = no #} # If yes, (or auto and libmysqlclient reports warnings are # available), will retrieve and log additional warnings from # the server if an error has occured. Defaults to 'auto' warnings = auto } - Search for
Connection info, right under it you’ll uncommentserver,port,login,passwordand change them to the MySQL credentials you created earlier for FreeRADIUS.This is the section in its initial state:# Connection info: # # server = "localhost" # port = 3306 # login = "radius" # password = "radpass"
And we’ll uncomment
server,port,login,passwordand change the values.# Connection info: # server = "localhost" port = 3306 login = "radius_user" password = "Somestrongpassword_321"
- A few lines further down look for
radius_dband change the default value to the database name that you created earlier. In my case it’s “radius_db”# Database table configuration for everything except Oracle radius_db = "radius_db"
- Further down find a line with
read_clients = yesthat is commented out, and uncomment it.Here is it’s initial state:# Set to 'yes' to read radius clients from the database ('nas' table) # Clients will ONLY be read on server startup. # read_clients = yesAnd here it is after we edit it:
# Set to 'yes' to read radius clients from the database ('nas' table) # Clients will ONLY be read on server startup. read_clients = yes - Lastly, further down there should be a line
client_table = “nas”. It should be uncommented by default. Just make sure it is uncommented and looks like this:# Table to keep radius client info client_table = "nas"
Now change the group rights of the file we just edited:
sudo chgrp -h freerad /etc/freeradius/3.0/mods-available/sql sudo chown -R freerad:freerad /etc/freeradius/3.0/mods-enabled/sql
And restart the FreeRADIUS service:
sudo systemctl restart freeradius.service
Finally, we’ll run FreeRADIUS in debug mode to make sure everything works.
First stop the currently running service:
sudo systemctl stop freeradius.service
And run the following command to run FreeRADIUS in debug mode:
sudo freeradius -X
The end of the output should look something like this:
Listening on auth address * port 1812 bound to server default Listening on acct address * port 1813 bound to server default Listening on auth address :: port 1812 bound to server default Listening on acct address :: port 1813 bound to server default Listening on auth address 127.0.0.1 port 18120 bound to server inner-tunnel Listening on proxy address * port 52025 Listening on proxy address :: port 42807 Ready to process requests
Press Ctrl+C to exit debug mode.
And start the FreeRADIUS service again.
sudo systemctl start freeradius.service
Now FreeRADIUS should be installed on your Debian 10 or Debian 11 machine. Next we’ll install a GUI called daloRADIUS to easily manage FreeRADIUS.
Install and Configure daloRADIUS (FreeRADIUS GUI)
DaloRADIUS is an advanced web-based RADIUS server that’s aimed at managing hotspots and ISP deployments. It’s written in PHP and JavaScript, and supports many database backends including MySQL, PostgreSQL, and SQLite.
We’ll download daloRADIUS from the Github repository:
If not already installed, install wget and unzip:
sudo apt -y install wget unzip
Download and extract daloRADIUS and cd into the resulting folder, which is daloradius-master:
wget https://github.com/lirantal/daloradius/archive/master.zip unzip master.zip cd daloradius-master
Now we’ll populate the database we use for FreeRADIUS with the daloRADIUS schema. It’s the database we created earlier – in my case radius_db.
First switch to root, otherwise you may get Access Denied:
sudo su -
Now run the following commands to import the daloRADIUS SQL schema:
sudo mysql -u root -p radius_db < contrib/db/fr2-mysql-daloradius-and-freeradius.sql sudo mysql -u root -p radius_db < contrib/db/mysql-daloradius.sql
Switch back to the non-root sudo user:
sudo su - edxd
cd out of the daloradius-master directory and move the folder into the document root and rename it as daloradius:
cd .. sudo mv daloradius-master /var/www/html/daloradius
Change the owner and the group for the daloradius folder to www-data:www-data, which are the owner and group under which Apache Web Server runs.
sudo chown -R www-data:www-data /var/www/html/daloradius/
Next we’ll need to create the daloRADIUS configuration file. daloRADIUS comes with a template for the configuration file, named /var/www/html/daloradius/library/daloradius.conf.php.sample which we’ll just copy.
sudo cp /var/www/html/daloradius/library/daloradius.conf.php.sample /var/www/html/daloradius/library/daloradius.conf.php
Change permissions for the configuration file to 664:
sudo chmod 664 /var/www/html/daloradius/library/daloradius.conf.php
Next we’ll edit a few values in the daloRADIUS configuration file so it connects to the database we created earlier for FreeRADIUS.
sudo nano /var/www/html/daloradius/library/daloradius.conf.php
We’ll change the following values:
$configValues['CONFIG_DB_USER'] = 'root'; $configValues['CONFIG_DB_PASS'] = ''; $configValues['CONFIG_DB_NAME'] = 'radius';
Here is how I have changed them, in accordance to the database name, user, and password that I have created earlier.
$configValues['CONFIG_DB_USER'] = 'radius_user'; $configValues['CONFIG_DB_PASS'] = 'Somestrongpassword_321'; $configValues['CONFIG_DB_NAME'] = 'radius_db'
Lastly restart daloRADIUS and Apache:
sudo systemctl restart freeradius.service apache2
Access daloRADIUS
First we’ll need to install the DB and MDB2 modules using PEAR:
sudo pear install DB sudo pear install MDB2
To access daloRADIUS visit IP or domain name of the machine in your browser, followed by /daloradius – for example http://your_server_ip/daloradius
Unless you configured SSL, make sure it’s http:// and the browser doesn’t change it to https://, as this may happen sometimes.
This is how daloRADIUS looks like:
The default login credentials are:
username: administrator
password: radius
Test FreeRADIUS & daloRADIUS
1. Creating a NAS Client Table
A NAS (Network Access Server) client table acts as a gateway to a protected resource. For another device to connect to our FreeRADIUS server, it needs to be added to the NAS client table.
Add a NAS client table by logging into the daloRADIUS dashboard. Then navigate to Management > NAS (in the blue submenu) > New NAS (in the left, dark gray sidebar)
The minimum options we need to fill in are the following:
NAS IP/Host: the IP of the computer from which you’ll connect
NAS Secret: a password
NAS Type: you can fill in everything here
NAS Shortname: a shortname for your convenience
I’ll fill in the following:
NAS IP/Host: the IP of my machine from which I’m trying to connect
NAS Secret: nobodywilleverlearnthissecret!!11!!
NAS Type: other
NAS Shortname: ProductionServer
2. Creating a daloRADIUS User
To test our server we’ll also need a user.
Create one by navigating in the top menu to Management > Users (in the blue submenu) > New User (in the left, dark gray sidebar)
For our example I’ll create the user with the following credentials:
Username: new_customer
Password: customer_strong_passwd_123
There are other fields available when creating a user, but those are enough for our purposes.
3. Run FreeRADIUS in Debug Mode
Next we’ll run FreeRADIUS in debug mode so we can see what happens when we send an authentication request to it.
First stop the running process:
sudo systemctl stop freeradius.service
And run the following command to run FreeRADIUS in debug mode:
sudo freeradius -X
[powerkit_alert type=”warning” dismissible=”false” multiline=”true”]Important
Every time you add a new NAS table you need to restart the FreeRADIUS server so it fetches the updated table.[/powerkit_alert]
4. Test the FreeRADIUS Server with NTRadPing
A convenient way to test the server is by using a free Windows software called NTRadPing.
You can download it here https://community.microfocus.com/t5/OES-Tips-Information/NTRadPing-1-5-RADIUS-Test-Utility/ta-p/1777768
This is a direct link to the archive https://community.microfocus.com/dcvta86296/attachments/dcvta86296/OES_Tips/148/1/ntradping.zip
This is the VirusTotal report so you know it’s safe https://www.virustotal.com/gui/file/e1b3318b884e4643a043ec5e3104638016c343c447424c244fc1da4f6e7165ec/detection
Just unzip the archive and run the executable to run NTRadPing. This is how it looks like:
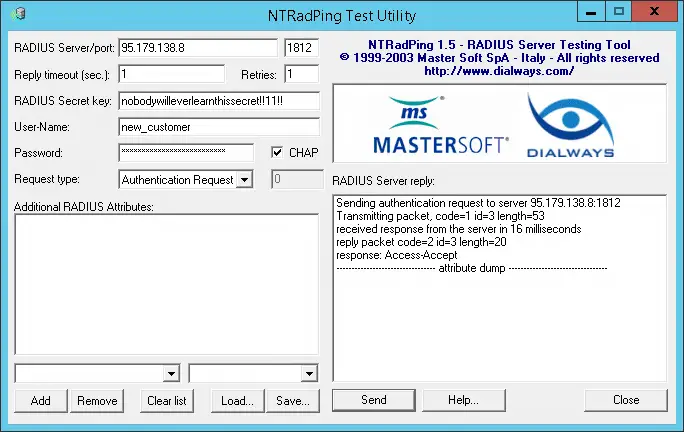
We’ll use it to send an authentication request to our server running FreeRADIUS in debug mode.
We’ll fill in the fields as follows:
RADIUS Server/port: IP of the FreeRADIUS server / port 1812
Reply timeout (sec.): 1
Retries: 1
RADIUS Secret Key: nobodywilleverlearnthissecret!!11!!
User-Name: new_customer
Password: customer_strong_passwd_123
Check the CHAP checkbox so the request is made using a CHAP password, instead of a PAP password.
Now click the Send button to send the authentication request.
If you receive an Access-Accept response, then we can assume it works.
The output of NTRadPing should look something like this:
Sending authentication request to server 40.76.122.52:1812 transmiting Packet, code=1 id=3 length=53 recieved response from the server in 16 milliseconds replay packet code=2 id=3 length=20 response: Access-Accept -------------------attribute dump------------------
And the output in the terminal, where we’re running FreeRADIUS in debug mode, should end with something like this:
... (2) Sent Access-Accept Id 7 from 10.0.2.4:1812 to 213.136.66.127:52163 length 0 (2) Finished request Waking up in 4.9 seconds. (2) Cleaning up request packet ID 7 with timestamp +67 Ready to process requests
Frequent Errors
“Failed binding with auth address […]” when running in debug mode
Failed binding to auth address * port 1812 bound to server default: Address already in use /etc/freeradius/3.0/sites-enabled/default[59]: Error binding to port for 0.0.0.0 port 1812
This error occurs when you’re trying to run FreeRADIUS but there is another instance of FreeRADIUS already running, so you’ll need to run the following command to stop it:
sudo systemctl stop freeradius.service
Conclusion
Well done. Hopefully you’ve successfully installed FreeRADIUS on Debian 10 or Debian 11, along with installing and configuring daloRADIUS, and then successfully tested the FreeRADIUS server.
If you’ve encountered any issues, then feel free to let us know in the comments or contact us, and we’ll get back to you as soon as we can.
Skip the setup and instantly deploy a pre-configured FreeRADIUS server with MySQL and daloRADIUS in seconds. Our solution is secure, fully configured, and designed to save you time.
Your servers, managed for you, so you can focus on your business.
Need a custom solution? Our expert team is available for hire. Feel free to contact us.






after i edit the /etc/freeradius/3.0/mods-enabled/sql
and run the command systemctl restart freeradius.service i get an error, cant do that cuz have an exit error code.
Then i debug the freeradius and get that couldn’t connect to MySQL server cuz Access Denied for the user we create early… can you help me please
Great tutorial but there seems to be an issue with the below.
Correct it with the edited version and you should be good to go.
Current:
Create the database and credentials that will be used by FreeRADIUS:
MariaDB [(none)]> CREATE DATABASE radius_db;MariaDB [(none)]> GRANT ALL ON radius_user.* TO radius_db@localhost IDENTIFIED BY “Somestrongpassword_321”;
MariaDB [(none)]> FLUSH PRIVILEGES;
MariaDB [(none)]> quit;
Edit:
MariaDB [(none)]> CREATE DATABASE radius_db;MariaDB [(none)]> GRANT ALL ON radius_db.* TO radius_user@localhost IDENTIFIED BY “Somestrongpassword_321”;
MariaDB [(none)]> FLUSH PRIVILEGES;
MariaDB [(none)]> quit;
Hi. It’s corrected now.
I don’t know how I could have missed that.
Thanks so much!
Great tutorial! As a noob of sorts, I could copy-paste the commands with minimal changes.
I did come across 2 problems..
After an error, followed by some Google-fu, I found that I had to rework the following for it to work (yay!)…
CREATE DATABASE radius_db;
CREATE USER ‘radius_user’@’localhost’ IDENTIFIED BY ‘Somestrongpassword_321’;
GRANT ALL PRIVILEGES ON radius_db.* TO ‘radius_user’@’localhost’;
FLUSH PRIVILEGES;
quit;
But now I’m stuck.. I didn’t get any errors for the rest of the installation, and I got the login screen, but when I enter the credentials I get a blank page athttp:///daloradius/dologin.php
Can’t seem to find a clear answer as to why…
please help
…and thanks in advance!
Hello,
Thank you for getting in touch and for your inpu. I’m sorry to hear you’re having difficulties.
[1] Regarding the MariaDB issue. I have updated it according to your edits. I mistakenly assumed the GRANT statement would automatically create a user in every scenario, but it doesn’t as you have pointed out.
[2] Regarding Daloradius. Just to make sure, when trying to log into Daloradius, are you getting a blank page or an error 500?
I have gone through the tutorial and I somehow forgot to add in the following section before accessing Daloradius (I’m very sorry for having missed that):
> First we’ll need to install the DB and MDB2 modules using PEAR:
Without the above command you’d most likely get error 500.
Hi,
I tried installing the DB and MDB2 modules as suggested,
…and it worked!
Awesome!
Btw, Just in case it helps, wrt..
[2] Regarding Daloradius. Just to make sure, when trying to log into Daloradius, are you getting a blank page or an error 500?
I just got a blank page, no error or warning.
Nice! I’m really glad to hear that!
Understood. Thank you very much for the info.
Thanks for this Manual. You may change the command under ‘Configure FreeRADIUS to Use MySQL/MariaDB’ where you get the ‘Tables_in_Radius’ output to ‘$ Sudo mysql -uroot -p -e “use radius_db;show tables” ‘
Not sure about the NTRadping utility though. In my my case i don’t need to configure any NAS to get a positive effect, leaving the secret key empty just works. Even If I configure a NAS with different credentials, still works. In conclusion: NAS configuration has no effect whatsoever on the NTradping utility. As long as I have IP, port, username and password right, it works.
Has anybody else this, and is this a clue why I can’t authenticate any devices to the radius server yet?
THANKS a lot…
Very useful tutorial it helped me a lot…
Justo one issue… I did it on Debian 9. When installing daloradius, I got an error due to a missing DB.php. I solved it by installing with pear install DB.
Then it works for me… even I try with user defined in text files end user added via daloradius and both worked
Hi Jose!
I’m very happy to hear that it worked out and the tutorial helped.
Regarding pear install DB – I’ll go through the tutorial again on Debian 10 and 9 so I can see it first hand when it happens and will update it.
Thanks so much for letting me know. I appreciate it!
To be accurate, the error was when I tried to access the web interface, it showed me a blank page, so it was necessary to edit php.ini and put display_errors on and restart apache and then I could see the error due to a missing DB.php
“You can check now check the tables in the database to confirm the schema has been imported:
sudo mysql -u root -p radius_db < /etc/freeradius/3.0/mods-config/sql/main/mysql/schema.sql” This should be the command to display the table, it’s just the same as the previous command. Thanks for the tut.
Hi Jeff!
Thanks for catching that and letting me know. I very much appreciate it! I don’t know how I missed that.
It’s now updated.
Thank you!
I have a Issu.
I become by http://172.16.11.10/daloradius this Url in the Firefox: http://172.16.11.10/login.php and this message: Not FoundThe requested URL was not found on this server.
What happen?
This blog daloRADIUS contains issues since daloRADIUS repo is updated by the developer. Blog owner, could you please update this blog based on the latest daloRADIUS version?
Example: sudo mysql -u root -p radius_db < contrib/db/fr2-mysql-daloradius-and-freeradius.sql
sudo mysql -u root -p radius_db < contrib/db/mysql-daloradius.sql
I can´t install MYSQL on Debian 12, can you post the repositories where I can find it?