In this tutorial, we’ll explain how to use SSH port forwarding and create a secure tunnel over the network, i.e., SSH Tunneling.
Have you ever used a VPN (Virtual Private Network)? We use VPN to access regionally restricted content, secure browsing, and many more.
VPN allows public internet users to connect to a private network and browse the internet as if they (public users) were on the private network.
Thus, it is called a “Virtual” Private Network.
On the other hand, SSH (Secure Shell) is a protocol that uses the client-server communication model to provide a secure channel for operating network services.
SSH provides encryption and can secure any network services over an unsecured network.
However, SSH can be used in many ways other than this – transfer files, forward local or remote ports (used as a tunnel), etc.
SSH Tunneling (SSH port forwarding) can also be used to create a basic VPN that allows us to access contents that are blocked by the firewall or regionally restricted.
We’ll begin this tutorial by first learning about what ports are and what do we mean by port forwarding.
Table of Contents
Ports and Port Forwarding
Since we want to cover port forwarding in this article, you must know how the ports function, why, and how port forwarding is done.
What are ports?
Ports act as communication endpoints.
What do we mean by that?
The operating system creates different logical ports for different applications/services to communicate over the network.
If you want to learn more about ports and understand how they operate, take a look at this article on IP addresses, basic concepts and terms explained.
In short, the IP address and ports work together to create a network endpoint that sends and receives data from other network endpoints.
These network endpoints are made with the IP address, and the port is called a network socket.
Different applications/services have different ports that they use for communication. For example, the SSH service has a default port of 22. This means the SSH application/service runs on port 22 by default, and all the data received or sent by the SSH application/service comes to or goes out from port 22.
Now let’s talk about port forwarding.
What is port forwarding?
Port forwarding is a kind of network address translation in which packets are redirected from one IP address and port combination (socket) to another while passing through a network gateway – a router or firewall.
In simple terms, port forwarding allows users from the internet or public network to connect to a host or a server that is behind a router or a firewall within a private network.
Chances are, your home network will be hidden from the public internet because it is behind your router, and the router will have the public IP facing the internet.
Now, if you were to initiate a connection from the outside network or the internet, the connection will come to your router at first using the public IP of the router. However, your router has no way of knowing where to send this data forward.
This is where the concept of port forwarding comes in handy.
Port forwarding is also known as port mapping. The idea is that you will specify the port number for the service and tie it to the IP address of the server in your router or the gateway. This way the router will know where (or which IP address) to send the traffic to when the connection requests from outside networks are asking to connect to that specific port.
Most modern routers support port forwarding.
To set up the port forwarding, you will have to access the control panel or interface of the router. You can do this by finding out the private IP address of the router/gateway and browsing to that address using a web browser. Even though all routers are different in how their user interface is organized, you will find this option with relative ease.
When setting up port forwarding, you will specify the port of the service and the private IP address of the device that the service is running on (server). For example, if you have set up an FTP server in your home, and the FTP service is running on port 21 with the server having an IP address of 192.168.1.10 – you will use this private IP address and port 21 in your router to set up port forwarding.
How does port forwarding enable outside connection now?
Let’s say your router has a public IP address of 200.X.X.X. When you want to connect to your home FTP server from the internet, you will first connect to the router that is on 200.X.X.X. After that, the router will notice that you want to connect to port 21 and forward your connection request to the server on 192.168.1.10 address because of enabling the port forwarding option.
The SSH command
In this tutorial, we will be using the SSH client command line utility on the Linux operating system.
SSH (SSH client) is a program for logging into a remote machine and for executing commands on a remote machine.
As previously mentioned, we can use SSH to forward ports and create secure communication as well. We will be using the SSH client for these purposes here. The utility can be accessed by using the ssh command.
SSH comes preinstalled in most Linux distributions. You will find the manual of the command by typing in man ssh in the command line.
For other operating systems than Linux, there are many SSH client applications that you can use. For example, Windows users can use a graphical user interface tool called PuTTY.
You can also create your own SSH server on the local network to test out the port forwarding done in this tutorial. You will need to have the username and the password to connect with an SSH server locally or remotely.
The ssh command has a basic syntax as the following:
ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-B bind_interface]
[-b bind_address] [-c cipher_spec] [-D [bind_address:]port]
[-E log_file] [-e escape_char] [-F configfile] [-I pkcs11]
[-i identity_file] [-J destination] [-L address]
[-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option]
[-p port] [-Q query_option] [-R address] [-S ctl_path]
[-W host:port] [-w local_tun[:remote_tun]] destination
[command]
We generally require the -D, -L, -R, and -p options to perform port forwarding or create an SSH tunnel.
What is SSH Tunneling?
The SSH protocol uses client-server architecture for communication, i.e., the client requests and the server provides the response.
As explained at the beginning of the article, this protocol can be used to secure any communication between two network services. SSH Tunneling is the way to create a secure communication channel.
Think of it as acting as an imaginary tunnel that provides a secure pathway for the data sent and received between two endpoints. In more technical terms, SSH Tunneling allows us to forward data from one port to another port in a secure way.
Types of SSH Tunneling or SSH Port Forwarding
SSH Tunneling can be used to bypass a firewall that blocks a specific port. It can also be used to create a SOCKS proxy that allows us to request the page from the proxy server – browse the internet as a different machine.
SSH Tunneling is also used to connect to remote networks that are within a company or business. There are different types of SSH Tunneling or port forwarding we can set up for different use cases. Let’s learn about the types of SSH port forwarding there are.
Local Port Forwarding
In local port forwarding, the client machine forwards a port to the server machine, and the server then sends the connection to its desired destination. (The server itself could be the destination as well.)
In this type of connection, the client listens to a specific socket (or on a specific port) and whenever any connection is made to this socket, the client forwards the connection to the destination socket (IP and Port) over the secure tunnel.
Take a look at the image below to understand how the local forwarding is done.
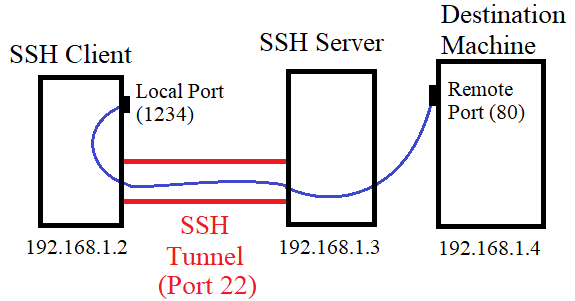
In the figure, the SSH client machine (192.168.1.2) on the left wants to connect to the destination machine (192.168.1.4) port 80. The SSH server is located at 192.168.1.3 address.
For this purpose, the client machine creates an SSH tunnel (marked in red) with the SSH server and starts listening on a local port (1234). After that, if any connection is made to the local port 1234, the client forwards the connection through the SSH Tunnel to the server.
The server then acts as the intermediary and sends the connection to the destination machine 192.168.1.4 and port 80. This is how local port forwarding allows an application on the client machine to connect to a local port and send data to the destination machine over the deployed secure SSH Tunnel.
When to use the Local Port Forwarding?
Now you may be thinking this is all nice and good. But why would I need to use local port forwarding?
That’s a very good question. Think about it this way – imagine the application you are using sends data without any encryption. If this is the case then you could easily use SSH Tunneling to secure the data transmission.
Another use case would be if your local firewall were to block the direct connection to port 80. In this case, you could easily bypass the firewall using SSH local port forwarding. Take a look at that image again – here, the client’s firewall will see that all the connection is being made over port 22 or the SSH Tunnel you created.
Thus, it will not block the connection, and you will be able to connect to the desired remote port (80).
Setting up Local Port Forwarding
You can find all the options that you can use with the SSH command by taking a look at the command manual. Type in man ssh and come down to the -L flag, which is used for the local port forwarding. You will find the description of how the local forwarding works.
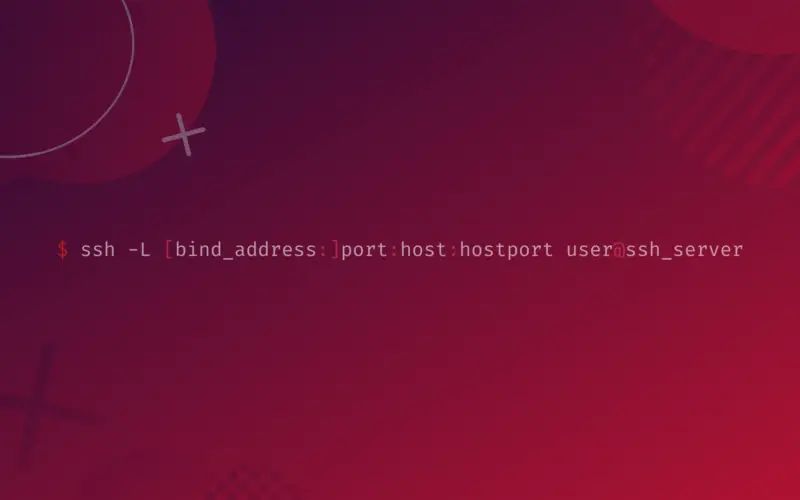
The general syntax for SSH local forwarding is:
ssh -L [bind_address:]port:host:hostport user@ssh_server
Here, the bind address is the IP address of the network interface on which the local port will be listening. If not specified, it takes the default value of localhost or 127.0.0.1 as the address.
The second field is the local port that will be listening. The field host is the address of the destination, and hostport is for the destination or remote port. You will also have to specify the username and password for the SSH connection to establish.
If you have SSH running on a port other than the default port 22, use the -p flag and specify that port.
For example, to set up local port forwarding as illustrated in the figure of local port forwarding, we’ll use the following command:
ssh -L 1234:192.168.1.4:80 user_name@192.168.1.3
Remote Port Forwarding or Reverse Tunneling
In this type of port forwarding, the SSH server itself connects back to the remote socket (IP & port).
In other words, the SSH server listens on a specific port and forwards incoming connections to the client machine over the secure SSH tunnel, eventually to the destination socket.
The destination could also be the client itself. The difference between this type of port forwarding and local port forwarding is that the server rather than the client forwards the connection.
Let’s take a look at the following diagram to understand this type of port forwarding better.
![]()
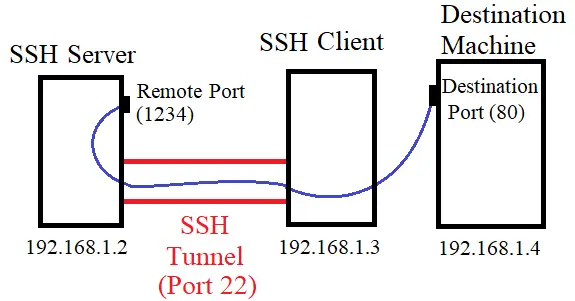
In the figure, the SSH client machine (192.168.1.3) will initiate the SSH connection with the server creating the secure SSH tunnel.
The client machine will also specify the remote port (1234) on which the server (192.168.1.2) will listen for any incoming connection.
After that, if any connection is made to the remote port 1234, the server will forward the connection through the SSH Tunnel to the client machine.
The client machine will then connect to the destination socket (192.168.1.4:80).
In this case, the client acts as the intermediary and sends the connection over to the destination machine 192.168.1.4 and port 80.
However, the client could also be the destination, e.g., some port on 192.168.1.3 address.
This is how remote port forwarding allows any application to connect to a remote port on the server and send data to the destination machine over the deployed secure SSH Tunnel.
When to use the Remote Port Forwarding?
Remote port forwarding is used when you want to access something that is within an internal or private network and there is no direct access from the outside.
For example, imagine you want to create an HTTP server on your personal home computer on port 80. But your computer does not have a public IP that can accept outside connections directly. So, you cannot connect to your server from an outside network, e.g., when you are in school or work.
In this case, you could use a remote SSH server that you can connect from your home in order to set up remote port forwarding.
Your home PC will act as the SSH client and the destination (port 80) here. You will request the SSH server to assign a remote port (let’s say port 1234) on which the server will listen for incoming connections. After setting it up, whenever any connection from the outside is made to port 1234 on the SSH server, the connection will be forwarded to your home PC (port 80) through the secure SSH tunnel. Now you can connect to your home PC (HTTP server on port 80) from wherever you want, as long as the remote SSH server port 1234 is reachable from the outside.
Setting up a Reverse Tunnel
To find the option for reverse tunnel or remote port forwarding, type in man ssh and find the -R flag, which is used for the remote port forwarding. There will also be a description of how remote forwarding works.
The general syntax for creating a reverse tunnel or SSH remote forwarding is:
ssh -R [bind_address:]port:host:hostport user@ssh_server
Here, the bind address is the IP address of the network interface on which the remote port will be listening. If not specified, the remote server will bind on all the interfaces.
The second field (port) is the remote port on the server that will be listening.
The field host is the address of the destination and hostport is for the destination port.
You will also have to specify the username and password for the SSH connection to establish.
If you have SSH running on a port other than the default port 22, use the -p flag and specify that port.
For example, to set up remote port forwarding as illustrated in the figure of remote port forwarding, we’ll use the following command:
ssh -R 1234:192.168.1.4:80 user_name@192.168.1.2
Dynamic Port Forwarding
Now that you know how local and remote port forwarding works, you might wonder if you could use SSH port forwarding as a proxy.
As stated before, the answer is yes.
The SSH server, in this case would act as a SOCKS proxy server, being the intermediary server.
We call this type of port forwarding dynamic port forwarding.
It is an application-level port forwarding similar to local port forwarding. The only difference is that the destination port is not specified.
We have to modify each application to use this SSH server, just as we would set up our browser to use any proxy server. This is accomplished by allocating a socket on our local machine or the SSH Client to listen to the specified port.
When a connection is established to this port, it is forwarded over the secure channel, and the application protocol is then used to determine which remote machine to connect to.
At the moment, SOCKS4 and SOCKS5 are supported, and SSH acts as a SOCKS server. Only root has the ability to forward privileged ports.
When to use Dynamic Port Forwarding?
We could use this type of port forwarding in many types of scenarios.
We could simply use the SSH server as a proxy server for bypassing firewalls or accessing regionally restricted content.
Imagine you are using an application that doesn’t provide any encryption over the sent data.
You could use dynamic port forwarding to configure the application to use the SSH SOCKS proxy server to secure communication. If you want to do this, for example, on Google Chrome, you would need to modify the network settings.
You will have to access the proxy settings and change the proxy server socket as you configured the dynamic port forwarding.
Setting up Dynamic Port Forwarding
You can find the description about Dynamic port forwarding by looking up the -D flag within the manual of the SSH command (man ssh).
The general syntax for creating a reverse tunnel or SSH remote forwarding is:
ssh -D [bind_address:]port user@ssh_server
Here, the bind address is the IP address of the local host on which the local port will be opened for listening.
If not specified, the value of the bind-address will be the localhost or 127.0.0.1 address.
The second field (port) is the local port on your client machine.
You will also have to specify the username and password for the SSH connection to establish. If you have SSH running on a port other than the default port 22, use the -p flag and specify that port.
For example, to set up Dynamic port forwarding considering the client and server addresses were to be as the first figure, we’ll use the following command:
ssh -D 1234 user_name@192.168.1.3
Conclusion
In this article, we talked about different types of SSH tunneling or SSH port forwarding. You also learned the basic concept of port forwarding and how it works.
SSH tunneling is used in real life in different types of scenarios, as explained before. We used the SSH command on the Linux operating system in this article.
You will find all the required information about this command in the manual of the command.
If you read the article thoroughly, you already know a lot of nerdy stuff about port forwarding than others. We hope you liked the article. If you have any questions or comments for us, leave them down below, and we’ll get back to you as soon as possible. Thank you for reading.