The usermod command allows us to modify an existing user account. With the usermod command, we can make different types of modifications, such as:
- add a user to a group
- change a user shell
- change the login name
- change the home directory
- change the User ID (UID)
Let’s proceed to take a look at this concept.
Objectives
This tutorial will cover the fundamentals of the usermod command, as well as some of its different use cases.
Table of Contents
- Objectives
- Prerequisites
- Methods to Modify a User Account
- Prerequisite to Modify a User Account
- Getting Help on the usermod Command
- Commenting the User Account
- Use usermod to Change a User’s Home Directory
- Setting Expiry Date on a User Account
- Changing the Primary User Group
- Adding Supplementary Groups to a User Account
- Locking and Unlocking the User Account
- Change the Login Shell
- Move a User’s Home Directory to Another Location
- Create an Un-encrypted Password for a User
- Change the Login Name for a User
- Conclusion
Prerequisites
- Access to a Linux machine
- Acting as a non-root sudo user to ensure a secure environment
Methods to Modify a User Account
Typically, in Linux, there are two ways to modify a user account. We can use the Graphical User Interface (GUI) tool to make certain changes, such as resetting the password or using a command-line utility to make such changes.
Novice users may prefer to perform operations, such as modifying the user account using the GUI tool.
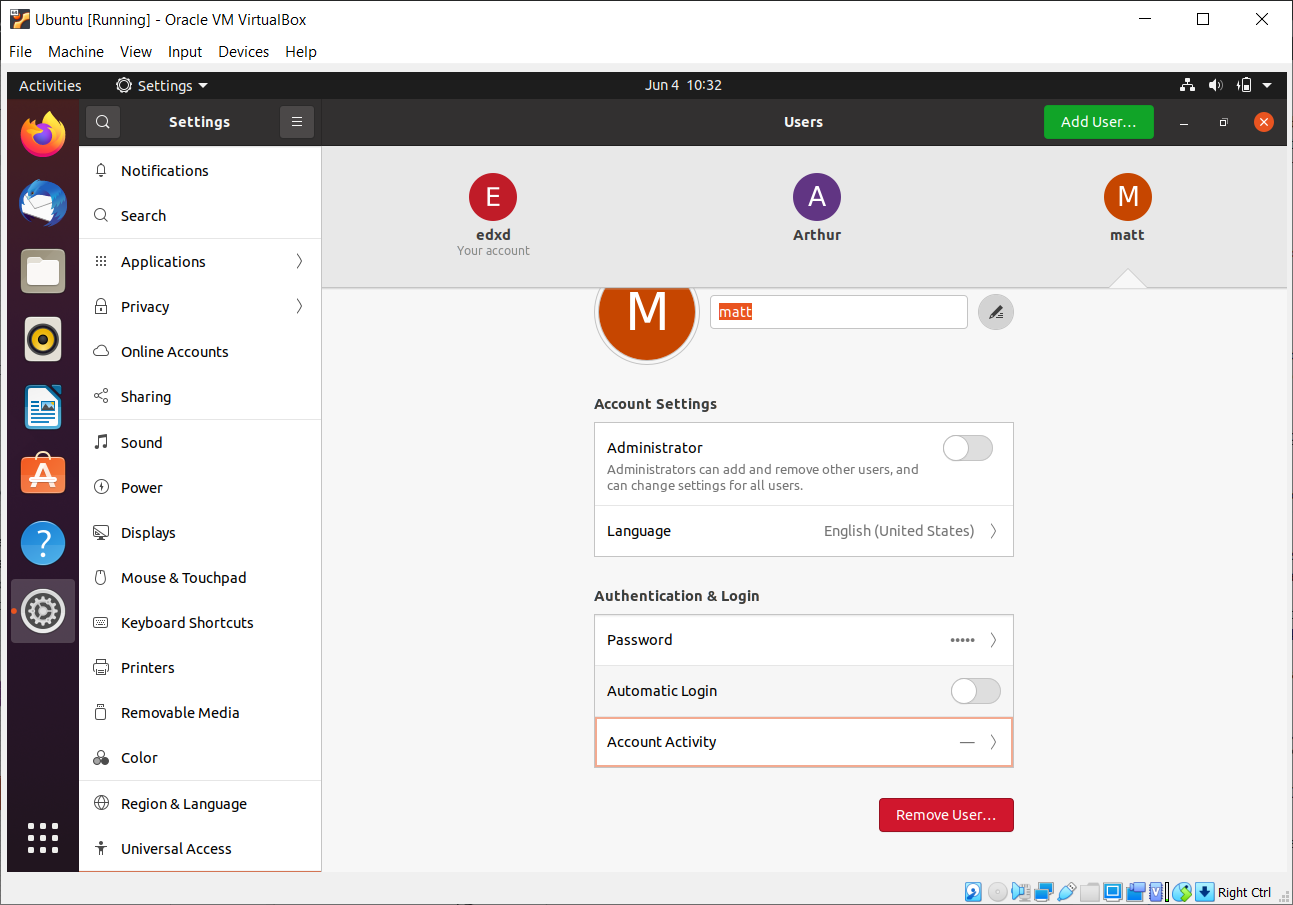
It is important to note that the GUI tool works in a limited capacity and provides only a handful of options, which may or may not always serve our purpose.
To make more types of modifications, we prefer using the command-line. Neither way can be considered correct or incorrect. It depends on the expertise, preference, and need. Simple operations like resetting the password can be done using GUI, but if there are more operations, such as changing the user ID, such as 1001, we have to use the command-line.
Prerequisite to Modify a User Account
Before we proceed to modify a user account, there are certain prerequisites we need to meet. These are:
- The user account must exist
- We need to have the administrative privileges to execute the usermod command
Getting Help on the usermod Command
The usermod command has several switches or parameters. We may never end up using all of them, but we will use several key ones, such as:
- -c
- -d
- -e
- -g
We will look at these key parameters very soon. Before we do that, we need to check the help. Three commands can be used to get help on parameters – usermod, usermod --h, or usermod -help:
All three commands provide the same output:
Usage: usermod [options] LOGIN
Options:
-b, --badnames allow bad names
-c, --comment COMMENT new value of the GECOS field
-d, --home HOME_DIR new home directory for the user account
-e, --expiredate EXPIRE_DATE set account expiration date to EXPIRE_DATE
-f, --inactive INACTIVE set password inactive after expiration
to INACTIVE
-g, --gid GROUP force use GROUP as new primary group
-G, --groups GROUPS new list of supplementary GROUPS
-a, --append append the user to the supplemental GROUPS
mentioned by the -G option without removing
the user from other groups
-h, --help display this help message and exit
-l, --login NEW_LOGIN new value of the login name
-L, --lock lock the user account
-m, --move-home move contents of the home directory to the
new location (use only with -d)
-o, --non-unique allow using duplicate (non-unique) UID
-p, --password PASSWORD use encrypted password for the new password
-R, --root CHROOT_DIR directory to chroot into
-P, --prefix PREFIX_DIR prefix directory where are located the /etc/* files
-s, --shell SHELL new login shell for the user account
-u, --uid UID new UID for the user account
-U, --unlock unlock the user account
-v, --add-subuids FIRST-LAST add range of subordinate uids
-V, --del-subuids FIRST-LAST remove range of subordinate uids
-w, --add-subgids FIRST-LAST add range of subordinate gids
-W, --del-subgids FIRST-LAST remove range of subordinate gids
-Z, --selinux-user SEUSER new SELinux user mapping for the user account
Now we’ll move ahead and use various parameters to perform certain operations. So, let’s get started.
Commenting the User Account
Let’s assume that we had created a user account a while back – in my example it’s matt. Now, we don’t remember why we had created this user account. For such reasons, it’s ideal to comment on user accounts.
Let’s go ahead and do this with the following command:
sudo usermod -c "Temporary user for Production Team" matt
We’ll be prompted for a password because we used sudo. After we provide the password for the user account, edxd, no output is displayed.
After commenting on the user matt, we need to verify it, which can be done with the finger command. In Ubuntu, the finger command is not available by default. We need to install it using the following command:
sudo apt install finger
After we install it, we can use the following command:
finger matt
The output displays the comment in the Name field.
Login: matt Name: Temporary user for Production Team Directory: /home/matt Shell: /bin/bash Never logged in. No mail. No Plan.
Let’s try an alternate method to view the comment. Try the following command:
grep "matt" /etc/passwd
Notice that the comment is mentioned after UID.
matt:x:1001:1001:Temporary user for Production Team:/home/matt:/bin/bash
Use usermod to Change a User’s Home Directory
As you can see in the output above, where we used finger matt, the home directory for matt is currently /home/matt.
When we create a user, by default, a home directory is created for the user. The home directory is named as /home/<username>. For example, for the user edxd, the home directory is /home/edxd.
We will now continue with the user matt to change the home directory, which can be done with the usermod command and the -d parameter, followed by the new home directory path.
We’ll also use the -m parameter to create the home directory if it does not exist. If you don’t use it, then the directory won’t be created.
Let’s try it out:
sudo usermod -d /home/test matt
There will be no output.
After changing the home directory, we can verify it using either of the following commands:
finger matt
OR
grep "matt" /etc/passwd
Notice that the home directory is now set to /home/test.
Login: matt Name: Temporary user for Production Team Directory: /home/test Shell: /bin/bash Never logged in. No mail. No Plan.
Setting Expiry Date on a User Account
In Linux, when a user account is created by default, there is no expiry date set. However, there can be scenarios where we want the user date to become inactive after a certain date. To do this, we can set the expiry date.
For example, let’s assume that matt, a temporary user in the organization, has a contract expiring on Oct 30th 2021. After this date, the user account should not be working and should become inactive unless manually enabled. We can leave the default settings, and then we will need to remember to disable or make the account inactive.
Otherwise, we can simply set the expiration date, which is an advisable method from the security perspective.
We have a user named matt. We can verify the expiry date for this account by running the following command:
sudo chage -l matt
When we run this command, we get several details, such as:
- Last password change
- Password expires
- Password inactive
- Account expires
- Minimum number of days between password change
- Maximum number of days between password change
- Number of days of warning before password expires
Last password change : Aug 12, 2021 Password expires : never Password inactive : never Account expires : never Minimum number of days between password change : 0 Maximum number of days between password change : 99999 Number of days of warning before password expires : 7
Let’s move ahead to set the expiry date on the user account.
To do this, we need to again use the usermod command with the -e parameter. We execute the following command:
sudo usermod -e 2021-08-30 matt
Notice that no output is returned. This means that the command was executed successfully. In this command, we used the -e parameter, which is used for setting the expiry date on the account. Then, we set the date on which the account should expire.
It is important to note that the date is 2021-10-30, which is in the YYYY-MM-DD format.
Let’s now verify the expiry date for the user matt:
chage -l matt
Notice that the account expiry date is now set to 2021-08-30.
Last password change : Aug 12, 2021 Password expires : never Password inactive : never Account expires : Aug 30, 2021 Minimum number of days between password change : 0 Maximum number of days between password change : 99999 Number of days of warning before password expires : 7
Changing the Primary User Group
When we create a user in Linux, it creates a default group with the same name. For example, when the user matt was created, a new group named matt was also created.
By default, the user is put into the same group. For example, matt is part of the group named matt, which is the default primary user group.
The usermod command, however, provides the flexibility to change the default primary group for the user. For example, if we need to change the group named matt to testusers, we can do it with the -g parameter of the usermod command.
Before we move ahead to change the group, we should verify the group for the user matt. We need to execute the following command:
id matt
Notice that the group name is matt, as shown in the exhibit below.
uid=1001(matt) gid=1001(matt) groups=1001(matt)
Now, let’s go ahead and change the primary group by executing the following command:
sudo usermod -g testusers matt
Notice that no output is returned. This means that the command was executed successfully.
Let’s now quickly verify the primary group for matt:
id matt
Notice that the primary group for matt is now testusers. The question is, how are we sure that testusers are the primary group for matt? The answer is in the gid field, which lists the Group ID number and the group name.
uid=1001(matt) gid=1002(testusers) groups=1002(testusers)
Adding Supplementary Groups to a User Account
In the previous section, we learned how to change the primary default group for a user.
Now, we will add supplementary groups to the same user, which is matt. When we need to add the supplementary group to a user, instead of using -g, we need to use the -G parameter.
When we executed the id command after changing the primary group, we noticed that matt is now part of the testusers (primary group) We will add a supplementary group named testers to matt’s user account with the following command:
sudo usermod -G testers matt
The command returns no output.
Let’s now quickly verify the supplementary groups for matt:
id matt
You can see now that the supplementary group for matt is now testers.
uid=1001(matt) gid=1002(testusers) groups=1002(testusers),1003(testers)
Let’s add another supplementary group, called anothergroup.
sudo usermod -G anothergroup matt
Now we’ll verify the groups for matt again:
id matt
uid=1001(matt) gid=1002(testusers) groups=1002(testusers),1005(anothergroup)
The catch here is that the -G option removes the existing supplementary group and adds a new one. This means that if matt is part of several supplementary groups, all of them will be removed.
So, is there a solution that can help us retain the existing supplementary groups and add another one? Yes, there is. We need to use the -a along with the -G parameter. The catch is that the -a parameter must be used before the -G parameter or does not get recognized. We are going to append the matt group to matt’s user account:
sudo usermod -a -G testers matt
The command returns no output.
Let’s now quickly verify the supplementary groups for matt:
id matt
Notice that this time the existing testers group is not removed, but rather matt is added.
uid=1001(matt) gid=1002(testusers) groups=1002(testusers),1003(testers),1005(anothergroup)
Locking and Unlocking the User Account
There may be situations in which you have to lock a user account.
- Delete the user account and recreate it when the contractor returns
- Lock the user account and unlock when the contractor returns
Deleting a user account and re-creating it is not a good option. This is because the user’s profile is also deleted. The user may end up losing data due to this.
However, a better option is to change the password and then lock the user account. When the contractor returns, you can unlock it.
When in a locked state, the user cannot log on to the system.
Here, we are going to focus on locking and unlocking the user account. Locking the user account is done with the -L option. Let’s see how this is done.
sudo usermod -L matt
The command does not return any output, which means that the command is executed successfully.
Let’s verify if matt’s account has been locked. We can verify this from the /etc/shadow file by executing the following command:
sudo cat /etc/shadow
matt:!$6$4IG8zAwWASwUby4.$i9.A9CLSEma8nAnel4/PDl1KmTQ95jjnwiU647bveSM3SRHmw3OZptrpwD.DzEszRRSVP//cYcwU5wcRkjYiy0:18851:0:99999:7::18869:
Notice that there is an exclamation mark after matt:. When a user account is in a locked state, an exclamation mark is added.
The /etc/shadow file, which is a system file, maintains the encrypted passwords for the user accounts. Only users with the administrative privileges have access to the /etc/shadow file.
After we have locked matt’s user account, we can also unlock it with the -U parameter. Let’s go ahead and unlock matt’s account with the following command:
sudo usermod -U matt
The command does not return any output, which means that the command is executed successfully.
Let’s verify the unlocking of matt’s user account from the /etc/shadow file. Notice that the exclamation mark has disappeared.
matt:$6$4IG8zAwWASwUby4.$i9.A9CLSEma8nAnel4/PDl1KmTQ95jjnwiU647bveSM3SRHmw3OZptrpwD.DzEszRRSVP//cYcwU5wcRkjYiy0:18851:0:99999:7::18869:
Change the Login Shell
When we create a user account in Linux, a login shell is assigned to the user by default. We can change the login shell. However, before we proceed in changing the user shell, we need to find out the shell that has been assigned to the user. To do that, we execute the following command:
grep -E "matt" /etc/passwd
matt:x:1001:1002:Temporary user for Production Team:/home/test:/bin/bash
What we did is extract the information from the /etc/passwd file for the user named matt. Notice the end of the output. The login shell is mentioned as /bin/bash.
We can now go ahead and change the shell to a different one. Let’s change it to sh. To do this, we need to execute the following command:
sudo usermod -s /bin/bash matt
We need to verify whether the login shell has been changed. To do this, we once again execute the usermod command.
usermod -E "matt" /etc/passwd
matt:x:1001:1002:Temporary user for Production Team:/home/test:/bin/sh
The login shell is now changed to /bin/sh.
Move a User’s Home Directory to Another Location
There are situations when we need to move a user’s home directory to another location in some scenarios. In most cases, by default, the user’s home directory is located in /home. We can change the location without impacting the user account.
Let’s first verify the current location of the home directory for the user matt.
Before we start to move the user’s home directory, we need to know where it is located. To find this out, once again, we need to execute the grep command and extract information from /etc/passwd:
grep -E "matt" /etc/passwd
matt:x:1001:1002:Temporary user for Production Team:/home/test:/bin/sh
Notice the home directory is mentioned as /home/test.
Let’s create a file in this directory so that we can later verify that it was indeed moved. We need to execute the following command:
sudo touch /home/test/move.txt
It is now time to move matt’s home directory to a different location. We need to execute the following command:
usermod -d /var/matt/ -m matt
Notice that the command executes successfully. The -d parameter is for the destination home directory for the user, and -m is used to move the contents along with the home directory. If the new home directory does not exist, it will be created when this command is executed.
Let’s quickly verify the contents of the /var/matt home directory by executing the following command:
sudo ls -l /var/matt
Notice that the move.txt file is now in the /var/matt directory.
-rw-r--r-- 1 root root 0 Aug 14 02:50 move.txt
So, since we have moved the home directory for matt, what happens to the /home/test directory? Let’s find it out by using the following command:
sudo ls /home/test
ls: cannot access '/home/test': No such file or directory
The directory no longer exists. It has been moved to a new location as /var/matt along with the move.txt file.
Create an Un-encrypted Password for a User
Previously, we learned that the/etc/shadow file is a system file and maintains the encrypted passwords for the user accounts. However, we can still store a user’s password in an unencrypted state. Let’s do this with the help of the usermod command.
Let’s assume that we want to assign a new unencrypted password to matt. We need to execute the following command, replacing <password> with our desired password:
sudo usermod -p <password> matt
The -p parameter is used for assigning an unencrypted password to a user.
I’ll set the password test:
sudo usermod -p test matt
The command won’t have any output if successful.
Let’s go ahead and verify if the /etc/shadow file actually stores an unencrypted password. Execute the following command:
sudo grep -E "matt" /etc/shadow
As we can see, the /etc/shadow file did store matt’s password (test) without encrypting it.
matt:test:18853:0:99999:7::18869:
Change the Login Name for a User
Each user that needs to log on to the Linux system needs a login name. We can verify if the username exists from the /etc/passwd file. Let’s see the login name for matt using the following command:
grep matt /etc/passwd
Well, the login name does exist. It is the first name, matt:
matt:x:1001:1002:Temporary user for Production Team:/var/matt:/bin/sh
Let’s assume that we need to change this login name from matt to edxduser. Even though it is not recommended to change the login name, but in some circumstances, we may have to do it. Let’s execute the following command:
sudo usermod -l edxduser matt
We need to use the -l parameter to change the login name. Then, we need to specify the username that we need to change to, which is edxduser. As the last option in this command, we need to use the existing login name, which is matt in this case.
After running the above command it won’t have output if successful.
Let’s quickly verify if edxduser exists in the /etc/passwd file:
grep edxduser /etc/passwd
matt is now replaced with edxduser. As we can see, the home directory is still /var/matt:
edxduser:x:1001:1002:Temporary user for Production Team:/var/matt:/bin/sh
Conclusion
Well done. Hopefully, this tutorial helped you understand the fundamentals of the usermod command in Linux. If you encountered any issues, please feel free to leave a comment or contact us, and we’ll get back to we as soon as we can.