Whether you are a network engineer or a regular user, learning the basics of some networking tools is just too important.
In this article, we’ve created a list of some of the most used networking tools in Linux, and we’ll try to get you familiar with these tools and their basic usage by using practical examples and explaining some core concepts.
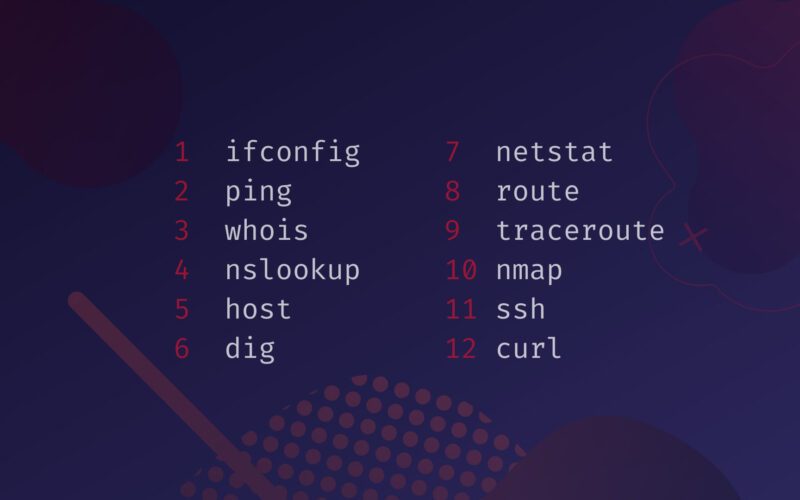
Table of Contents
- ifconfig – List and Configure Network Interfaces
- ping – Check Connectivity/Reachability or DNS Resolution
- whois – Get Whois Information on Domain Names
- nslookup – Find the IP Address of a Hostname and Vice Versa
- host – Advanced DNS Lookup Utility
- dig – DNS Lookup Utility That Provides More Detailed Domain Info
- netstat – Display Listening Ports, Along with Incoming/Outgoing Network Connections
- route – Display and Modify the IP Routing Table
- traceroute – Find Route Taken by Packets Across the Network
- nmap – Network Exploration Tool and Security/Port Scanner
- ssh – Log Into Remote Machines and Execute Commands on Them
- curl – Transfer Data From or To a Server With Many Supported Protocols
- Conclusion
ifconfig – List and Configure Network Interfaces
ifconfig stands for Interface Configuration.
It is a popular command used to find out the IP address of a machine. This command helps you to list your interfaces and show information about each of them.
You can also disable/enable a specific interface and assign static IP addresses to them.
Let’s see what interfaces I have on my machine:
ifconfig
eth1 Link encap:Ethernet HWaddr 00:50:56:c0:00:01
inet addr:169.254.71.51 Bcast:169.254.255.255 Mask:255.255.0.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth2 Link encap:Ethernet HWaddr 00:50:56:c0:00:08
inet addr:169.254.150.137 Bcast:169.254.255.255 Mask:255.255.0.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Global
UP LOOPBACK RUNNING MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
wifi0 Link encap:UNSPEC HWaddr 10-02-B5-99-C2-A3-00-00-00-00-00-00-00-00-00-00
inet addr:192.168.43.111 Bcast:192.168.43.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
I can see two ethernet interfaces (eth1 and eth2) and a Wi-Fi one as well (wifi0).
lo is the loopback device. It is a special virtual network interface used to communicate with processes running on the local machine, without using the network.
The Wi-Fi interface has an IP address of 192.168.43.111 which is the IP address of my machine over the wireless network.
We can also see the MAC address or physical address of the interface marked, which is 10-02-B5-99-C2-A3-00-00-00-00-00-00-00-00-00-00 line 26.
You can list all of the interfaces with the command:
ifconfig -a
For enabling/disabling an interface use the following commands:
ifconfig eth1 down ifconfig eth1 up
You can add a static IP to any of your interfaces like this:
ifconfig eth1 [IP_address]
ping – Check Connectivity/Reachability or DNS Resolution
ping stands for Packet Internet Groper, and this command is used to find out whether a host is reachable or not.
This is a basic tool that is available in almost all operating systems with network capabilities. Ping uses the Internet Control Message Protocol (ICMP) to send an ICMP echo request and waits for the host to reply with an ICMP echo reply.
It outputs the mean round-trip time for the packet to arrive.
This tool can be used to debug your internet connection and if the DNS resolution is working properly.
Here are some examples of how to use the ping command.
Let’s see if our server is reachable or not. Type in the following in your command line:
ping bytexd.com
On Linux systems, the ping command will continuously run until the user stops it. You can use CTRL + C to interrupt or kill it.
On Windows machines, ping only sends 4 echo requests by default. There are options to send the echo request a specified number of times with specified packet size.
PING bytexd.com (172.67.203.243) 56(84) bytes of data. 64 bytes from 172.67.203.243: icmp_seq=1 ttl=52 time=596 ms 64 bytes from 172.67.203.243: icmp_seq=2 ttl=52 time=634 ms 64 bytes from 172.67.203.243: icmp_seq=3 ttl=52 time=595 ms 64 bytes from 172.67.203.243: icmp_seq=4 ttl=52 time=331 ms 64 bytes from 172.67.203.243: icmp_seq=5 ttl=52 time=353 ms ^C --- bytexd.com ping statistics --- 5 packets transmitted, 5 received, 0% packet loss, time 4241ms rtt min/avg/max/mdev = 331.821/502.334/634.674/131.287 ms
The output shows we’re receiving the replies of the server.
We can see the round trip time required for each packet marked in green.
Round trip time measures how long it takes for the packet to arrive from the moment of sending the packet. Notice the last line of the output also says rtt, which stands for Round Trip Time.
The minimum, average, maximum rtt is shown. The last term mdev basically represents the standard deviation in round trip time, i.e., with the mdev being larger the variability in rtt over time will be greater.
whois – Get Whois Information on Domain Names
whois is a protocol that works based on query and response – it stores domain registrar, provider company & owner, etc. information and provides these when queried. Often information gathering starts from here.
We can get some important information about the registered domain, start or expiry dates, and company owners using this tool.
You can think of this being analogous to the information of a house and its buying details.
Whois tool comes pre-installed in most distros of Linux.
Let’s see whois record of our website:
whois bytexd.com
Domain Name: BYTEXD.COM Registry Domain ID: 2518223704_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.namecheap.com Registrar URL: http://www.namecheap.com Updated Date: 2021-03-25T20:17:00Z Creation Date: 2020-04-24T08:57:44Z Registry Expiry Date: 2022-04-24T08:57:44Z Registrar: NameCheap, Inc. Registrar IANA ID: 1068 Registrar Abuse Contact Email: abuse@namecheap.com Registrar Abuse Contact Phone: +1.6613102107 Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited Name Server: ELLE.NS.CLOUDFLARE.COM Name Server: RAY.NS.CLOUDFLARE.COM DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/ >>> Last update of whois database: 2021-05-23T08:37:17Z <<< For more information on Whois status codes, please visit https://icann.org/epp NOTICE: The expiration date displayed in this record is the date the registrar's sponsorship of the domain name registration in the registry is currently set to expire. This date does not necessarily reflect the expiration date of the domain name registrant's agreement with the sponsoring registrar. Users may consult the sponsoring registrar's Whois database to view the registrar's reported date of expiration for this registration.
I’ve deliberately removed the Terms of Use portion from the output.
We can get notice some important information from the output. The domain was bought from namecheap.com. We can also see the creation and expiry dates. The nameservers are also listed in the lookup.
nslookup – Find the IP Address of a Hostname and Vice Versa
The name nslookup comes from Name Server Lookup.
It is a command-line tool that queries the Domain Name Servers (DNS) for the domain name to IP address mapping or some other DNS records.
There are two versions of the tool that are used. The non-interactive and interactive mode.
In the interactive mode, you don’t have to call in the nslookup utility or type nslookup in your command every time.
Nslookup is pre-installed and available in most operating systems.
Let’s find out the IP addresses of bytexd.com with nslookup:
nslookup bytexd.com
Server: 192.168.43.1 Address: 192.168.43.1#53 Non-authoritative answer: Name: bytexd.com Address: 104.21.37.46 Name: bytexd.com Address: 172.67.203.243
The output of the nslookup query shows us the IP addresses of the server where bytexd.com is located.
The IP addresses of bytexd.com are shown in green color. The DNS server that we queried is also shown at the top of the output.
You can see the number 53 written in the address next to the server IP address. That is the port on which DNS operates.
The Non-authoritative answer means that the answer did not come from an authoritative DNS server, rather it came from the cached results of my local DNS server.
Let’s change the DNS server from which we’re querying:
nslookup bytexd.com 8.8.8.8
Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: bytexd.com Address: 172.67.203.243 Name: bytexd.com Address: 104.21.37.46
Here, we changed the server to 8.8.8.8 which is a public DNS server of Google. You can easily enter the interactive mode of nslookup just by entering nslookup without any options. You will see a >, indicating that you’re in the interactive mode. Let’s do some other type of DNS queries in the interactive mode.
We’ll check what are the mail servers bytexd.com uses. Run:
nslookup
nslookup > set type=MX > bytexd.com
Server: 192.168.43.1 Address: 192.168.43.1#53 Non-authoritative answer: bytexd.com mail exchanger = 20 mx2.improvmx.com. bytexd.com mail exchanger = 10 mx1.improvmx.com. Authoritative answers can be found from:
As you can see, the mail exchangers are shown in the output. We changed the DNS query type into a mail exchanger (MX) record.
Now, let’s look at the name servers bytexd.com is using with the NS tag:
> set type=NS > bytexd.com
Server: 192.168.43.1 Address: 192.168.43.1#53 Non-authoritative answer: bytexd.com nameserver = elle.ns.cloudflare.com. bytexd.com nameserver = ray.ns.cloudflare.com. Authoritative answers can be found from:
Now that you know the nameservers of bytexd.com, let’s try to get an Authoritative answer for our DNS query.
But first, we have to know the IP address of one of the name servers. Let’s try nslookup on the nameservers now:
First, get out of the interactive mode by pressing CTRL + C. Now type in:
nslookup elle.ns.cloudflare.com
Server: 192.168.43.1 Address: 192.168.43.1#53 Non-authoritative answer: Name: elle.ns.cloudflare.com Address: 172.64.32.110 Name: elle.ns.cloudflare.com Address: 173.245.58.110 Name: elle.ns.cloudflare.com Address: 108.162.192.110
Now we know the IP address of the nameserver that bytexd.com is using. Let’s get the address of bytexd.com from this nameserver:
nslookup bytexd.com 172.64.32.110
Server: 172.64.32.110 Address: 172.64.32.110#53 Name: bytexd.com Address: 172.67.203.243 Name: bytexd.com Address: 104.21.37.46
Voila! Now you don’t see the Non-authoritative answer written, because the DNS server we queried is actually the Authoritative nameserver for bytexd.com.
host – Advanced DNS Lookup Utility
host is another tool in Linux for querying the DNS records.
Host command is similar to nslookup, however, it is more advanced. If you just type in host and hit enter, you’ll find the syntax and all the uses for it.
Let’s try the host command with our website again:
host bytexd.com
bytexd.com has address 172.67.203.243 bytexd.com has address 104.21.37.46 bytexd.com has IPv6 address 2606:4700:3036::ac43:cbf3 bytexd.com has IPv6 address 2606:4700:3037::6815:252e bytexd.com mail is handled by 10 mx1.improvmx.com. bytexd.com mail is handled by 20 mx2.improvmx.com.
As you can see, the host command reveals more about the domain we were querying.
It showed the IPv4 and the IPv6 addresses along with the mail exchanger information.
You can specify different types of queries with the -t flag followed by the type of the query:
host -t ns bytexd.com
bytexd.com name server elle.ns.cloudflare.com. bytexd.com name server ray.ns.cloudflare.com.
It conveniently gives us a short and direct answer to our queries. Let’s see the SOA (Start of Authority) record:
host -t soa bytexd.com
bytexd.com has SOA record elle.ns.cloudflare.com. dns.cloudflare.com. 2037128925 10000 2400 604800 3600
dig – DNS Lookup Utility That Provides More Detailed Domain Info
dig stands for DNS Information Groper.
It is one of the most popular and powerful DNS lookup tools. It can be used to perform the same tasks as nslookup and host commands, but it is a much more robust tool for debugging and inquiring DNS records.
Let’s familiarize ourselves with the dig command:
dig example.com
; <<>> DiG 9.10.3-P4-Ubuntu <<>> example.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4621 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;example.com. IN A ;; ANSWER SECTION: example.com. 5767 IN A 93.184.216.34 ;; Query time: 3 msec ;; SERVER: 192.168.43.1#53(192.168.43.1) ;; WHEN: Sat May 22 17:45:29 STD 2021 ;; MSG SIZE rcvd: 45
As you can see, the output essentially gives the same information as host and nslookup, but with more details.
By default, the dig command shows the Header of the response/answer that it got from the server. We can see the status has a value of NOERROR in the header, which means dig received a response from the server without any issues. In the question section, we see what the initial query was.
We can see the query type is A which only shows the IP address associated with the domain. In the answer section, the IP address of example.com is shown. Notice that below the answer section dig listed the server from which the query was answered.
We can get a short answer by adding +short:
dig example.com +short
93.184.216.34
This is very convenient for some quick DNS queries. We can also query a custom DNS server instead of our default one:
dig example.com @8.8.8.8 +short
93.184.216.34
Here we used the public DNS server of Google again.
Let’s find out the nameservers of example.com:
dig example.com @8.8.8.8 NS +short
a.iana-servers.net. b.iana-servers.net.
Here’s how to get TXT records with dig:
dig example.com @8.8.8.8 NS +short
"v=spf1 -all" "8j5nfqld20zpcyr8xjw0ydcfq9rk8hgm"
You can also perform a reverse DNS lookup with dig:
dig -x 8.8.8.8
dns.google.
This shows that the IP address of 8.8.8.8 is actually of the DNS server of Google.
netstat – Display Listening Ports, Along with Incoming/Outgoing Network Connections
netstat stands for Network Statistics.
This is an extremely useful utility used by network administrators quite often.
The main function netstat performs is showing the active connections, especially for the Transmission Control Protocol (TCP).
The connections on the system can be monitored and this is a great utility for finding out if there is some malicious program in your computer with active internet connections.
It can also be used to debug issues and secure the system. Netstat has quite broad usage and can be a topic on its own. However, we’ll just show you some useful examples of how to use the command.
Run a simple netstat command to see all the active connections in your system:
netstat -a
This will list out many connections on the command line.
Let’s see how to get specific results. Imagine you wanted to list out the active TCP connections.
We have to combine a and t in the option, which translates to all the connections that are tcp. Run the following:
netstat -at
Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:sunrpc 0.0.0.0:* LISTEN tcp6 0 0 [::]:sunrpc [::]:* LISTEN
Similarly, you’ll use -au flag for the UDP connections:
netstat -au
Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State udp 0 0 0.0.0.0:938 0.0.0.0:* udp 0 0 0.0.0.0:bootpc 0.0.0.0:* udp 0 0 0.0.0.0:sunrpc 0.0.0.0:* udp6 0 0 [::]:938 [::]:* udp6 0 0 [::]:sunrpc [::]:*
You can only get the listening connections by -l flag. You can also combine this with other options.
Now that you know how to see the active connections using netstat, you might be wondering – how to see which processes are associated with the active connections. Use the -p option to get the PID (Process ID) of the processes. Let’s use this with the combination of -at which gives us the active TCP connections:
netstat -atp
Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:sunrpc 0.0.0.0:* LISTEN 338/rpcbind tcp6 0 0 [::]:sunrpc [::]:* LISTEN 338/rpcbind
As you can see now, the program name is rpcbind that is running on PID 338.
I only have this process listening on my machine. Let’s kill it with the kill command, and then try to see if anything shows up when we try netstat:
kill 338
netstat -atp
Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
No program is showing to be connected using TCP protocol now, as expected. If this doesn’t seem interesting to you, I’ll just open my firefox and load a webpage there. While the page loads, let’s run the command netstat to see if it catches anything interesting:
netstat -atp
Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:sunrpc 0.0.0.0:* LISTEN 3147/rpcbind tcp 0 0 blackOS:59484 a-0001.a-msedge.n:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:59850 104.21.37.46:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:59852 104.21.37.46:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:54314 192.0.76.3:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:59000 maa03s42-in-f14.1:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:54312 192.0.76.3:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:59848 104.21.37.46:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:59004 maa03s42-in-f14.1:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:58078 104.21.37.46:http ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:59854 104.21.37.46:https ESTABLISHED 2648/firefox-esr tcp 0 0 blackOS:58080 104.21.37.46:http TIME_WAIT - tcp 0 0 blackOS:59480 a-0001.a-msedge.n:https ESTABLISHED 2648/firefox-esr tcp6 0 0 [::]:sunrpc [::]:* LISTEN 3147/rpcbind
The output is flooded with firefox, and you can see where it is connecting and at what port the connection is taking place. By the way, can you recognize the IP address – 104.21.37.46? If you don’t remember, this is the IP address of bytexd.com. I opened the Firefox browser and typed in bytexd.com and hit enter. Then I performed the netstat command.
In the output, you can see that firefox is the local application that is communicating with the remote bytexd.com server. The local address is the address of my machine with the port number, and the foreign address is the bytexd.com server’s address and https (443) is the port.
Now to finish it up, let’s see how you can find some specific results according to your requirements. We’ll use the | grep to do this. The grep command works like a search:
I’ll start the ssh service on my machine:
service ssh start
Now let’s do the following command to see if any ssh service is running. We can do this in two ways –
netstat -at | grep ssh
tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN tcp6 0 0 [::]:ssh [::]:* LISTEN
As we can see the only result with ssh ports is returned in the output. The second way would be to output the netstat command in numeric with the -n option. This will output the ports with numbers. We know ssh runs on port 22 by default. Let’s filter the numeric output of netstat using grep command:
netstat -atn | grep 22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp6 0 0 :::22 :::* LISTEN
The previous result is returned, only with the ports showing up with numbers.
route – Display and Modify the IP Routing Table
route command modifies the IP routing table. A routing table is exactly what the name suggests. It is a file that contains the information about the network topology immediately around the host, i.e., it tells the host what route to use and how to reach from one point (hop) to the next point (hop) in the network. Your router uses this route table for efficient data transfer between you the source and your destination.
The route command is deprecated for the ip route command. However, we’ll focus mostly on route command in this article.
Let’s find out the routing table on our machine:
route
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 192.168.56.0 * 255.255.255.0 U 256 0 0 eth1 192.168.56.1 * 255.255.255.255 U 256 0 0 eth1 192.168.56.255 * 255.255.255.255 U 256 0 0 eth1 224.0.0.0 * 240.0.0.0 U 256 0 0 eth1 255.255.255.255 * 255.255.255.255 U 256 0 0 eth1 192.168.74.0 * 255.255.255.0 U 256 0 0 eth2 192.168.74.1 * 255.255.255.255 U 256 0 0 eth2 192.168.74.255 * 255.255.255.255 U 256 0 0 eth2 224.0.0.0 * 240.0.0.0 U 256 0 0 eth2 255.255.255.255 * 255.255.255.255 U 256 0 0 eth2 127.0.0.0 * 255.0.0.0 U 256 0 0 lo 127.0.0.1 * 255.255.255.255 U 256 0 0 lo 127.255.255.255 * 255.255.255.255 U 256 0 0 lo 224.0.0.0 * 240.0.0.0 U 256 0 0 lo 255.255.255.255 * 255.255.255.255 U 256 0 0 lo default 192.168.43.1 255.255.255.255 U 0 0 0 wifi0 192.168.43.0 * 255.255.255.0 U 256 0 0 wifi0 192.168.43.111 * 255.255.255.255 U 256 0 0 wifi0 192.168.43.255 * 255.255.255.255 U 256 0 0 wifi0 224.0.0.0 * 240.0.0.0 U 256 0 0 wifi0 255.255.255.255 * 255.255.255.255 U 256 0 0 wifi0
Here, in the routing table of my machine, all the IP addresses are private. And we can see the default gateway is at the 192.168.43.1 address. This is actually the router.
Gateway is the door that connects you with the outside networks as its name suggests. Metric is the measure of how much closer the destination hop is to the host.
The lower the Metric number, the closer the destination is.
So, you might ask – why is all the destination IP address stored in my IP table? How will it connect with the outer network? When my machine requires to connect with any entries that already exist, i.e., inside my private network, the IP table will be used.
However, when none of the destination IP addresses on the table matches the subnet mask of the IP address that I’m trying to reach – the packet will go to the default gateway or the first router.
Now let’s look at the routing table of my router at 192.168.43.1 (Remember, for seeing the routing table of the router you have to access the router, or you can run the route command on the router if it supports. I’ve created the router using another Linux device. So, I’ll run the route command on my router.)
route
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 100.70.79.72 0.0.0.0 255.255.255.252 U 0 0 0 rmnet_data1 192.168.43.0 0.0.0.0 255.255.255.0 U 0 0 0 wlan0
It’s clear that the first destination IP address is public. It is indeed the IP of one of the routers from my ISP. You can add, remove, or blacklist IP addresses on your route table.
traceroute – Find Route Taken by Packets Across the Network
traceroute does what its name suggests. It traces the route through all the nodes in the network to reach a specific node. Traceroute also measures round trip times to reach each node on the path or route. In Windows systems, the equivalent command of traceroute is tracert.
In Windows, the tracert command sends ICMP echo requests just like the ping command. However, in Unix-like operating systems, the traceroute command sends UDP packets by default. You can use the -I flag to send an ICMP packet instead.
Let’s find out what paths our machine takes to reach bytexd.com with the traceroute command:
traceroute bytexd.com
Tracing route to bytexd.com [104.21.37.46] over a maximum of 30 hops: 1 6 ms 3 ms 2 ms 192.168.43.1 2 * * * Request timed out. 3 402 ms 325 ms 316 ms 10.174.174.129 4 * * * Request timed out. 5 459 ms 318 ms 316 ms 10.243.21.22 6 * * * Request timed out. 7 269 ms 256 ms 238 ms 202.56.7.2 8 * 325 ms * 103.15.245.225 9 304 ms 324 ms 324 ms 157.119.185.232 10 342 ms 307 ms 320 ms 116.51.16.244 11 335 ms 402 ms 358 ms ae-11.r23.sngpsi07.sg.bb.gin.ntt.net [129.250.2.93] 12 335 ms 408 ms 408 ms ae-17.r31.tokyjp05.jp.bb.gin.ntt.net [129.250.2.243] 13 406 ms 406 ms 342 ms ae-3.r00.tokyjp08.jp.bb.gin.ntt.net [129.250.6.129] 14 508 ms 490 ms * 61.120.144.42 15 517 ms 512 ms 525 ms 104.21.37.46 Trace complete.
The output shows the nodes (hops) in the path to reach the bytexd.com and each of their round-trip time. The first node is the default gateway in my network (192.168.43.1).
You can change the hop limit with the -m flag:
traceroute -m 10 bytexd.com
nmap – Network Exploration Tool and Security/Port Scanner
nmap stands for Network Mapper.
It is a very powerful tool used for network discovery and mapping. Nmap offers a wide variety of functionality for scanning a network for information gathering, vulnerability analysis, and penetration testing. Network engineers also use this tool for mapping the network topology and debugging.
Nmap is a huge topic that is out of the scope of this article. We have a comprehensive guide to Nmap that covers basic to advanced topics in one article.
We’ll cover some basic commands and scans you can perform with Nmap here. Let’s perform a basic scan on bytexd.com with nmap:
nmap bytexd.com
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-23 13:08 Bangladesh Standard Time Nmap scan report for bytexd.com (172.67.203.243) Host is up (0.41s latency). Other addresses for bytexd.com (not scanned): 104.21.37.46 Not shown: 996 filtered ports PORT STATE SERVICE 80/tcp open http 443/tcp open https 8080/tcp open http-proxy 8443/tcp open https-alt Nmap done: 1 IP address (1 host up) scanned in 34.48 seconds
Doing this scan without any parameters reveals some interesting details about the bytexd.com server.
We can see the open ports on the server and it seems to be a web server with http and https ports open at 80 and 443 respectively. Like this, you can perform different scans to find out more information about a host. If a host is running some vulnerable applications, this information is valuable to secure the host. The default scan performs 1000 ports and finds out the open ports.
If you want to perform a quick scan without searching 1000 ports, you can use the -F flag to enable the Fast scan, which only searches 100 ports.
nmap -F bytexd.com
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-23 13:17 Bangladesh Standard Time Nmap scan report for bytexd.com (104.21.37.46) Host is up (0.22s latency). Other addresses for bytexd.com (not scanned): 172.67.203.243 Not shown: 96 filtered ports PORT STATE SERVICE 80/tcp open http 443/tcp open https 8080/tcp open http-proxy 8443/tcp open https-alt Nmap done: 1 IP address (1 host up) scanned in 21.24 seconds
We see the same output, but, notice that the time for the second scan is lower than the first one. As we mentioned, this scan only looks at 100 ports, thus the scan is quite faster than the 1000 port scan.
Now you might wonder, how to get out more information? Because this much information is not very helpful.
Let’s detect the versions of each service that the bytexd.com server is running with the -sV or the service detection flag:
nmap -F -sV bytexd.com
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-23 13:33 Bangladesh Standard Time Nmap scan report for bytexd.com (172.67.203.243) Host is up (0.17s latency). Other addresses for bytexd.com (not scanned): 104.21.37.46 Not shown: 96 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Cloudflare http proxy 443/tcp open ssl/http Cloudflare http proxy 8080/tcp open http Cloudflare http proxy 8443/tcp open ssl/http Cloudflare http proxy Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 32.65 seconds
As we can see, the service version is also showing up in the output. This is very helpful in determining whether the host is running any vulnerable services. Hackers will try to exploit these vulnerabilities while the network/system administrators will use this information to secure their system.
You can also try an OS detection scan on the remote host with the -O flag:
nmap -F -O bytexd.com
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-23 13:39 Bangladesh Standard Time Nmap scan report for bytexd.com (172.67.203.243) Host is up (0.33s latency). Other addresses for bytexd.com (not scanned): 104.21.37.46 Not shown: 96 filtered ports PORT STATE SERVICE 80/tcp open http 443/tcp open https 8080/tcp open http-proxy 8443/tcp open https-alt Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: phone Running (JUST GUESSING): Google Android 5.X (85%) OS CPE: cpe:/o:google:android:5.0.1 Aggressive OS guesses: Android 5.0.1 (85%) No exact OS matches for host (test conditions non-ideal). OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 19.88 seconds
The output shows the guess for the operating system running on the server. Sometimes, this information is also helpful for the hackers to find out suitable weak points and exploits for the system.
Lastly, we’ll show you the aggressive scan with Nmap (Remember, this type of scans produces a lot of noise and are illegal without permission):
nmap -A bytexd.com
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-23 13:42 Bangladesh Standard Time Nmap scan report for bytexd.com (172.67.203.243) Host is up (0.28s latency). Other addresses for bytexd.com (not scanned): 104.21.37.46 Not shown: 996 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Cloudflare http proxy |_http-server-header: cloudflare |_http-title: Did not follow redirect to https://bytexd.com/ 443/tcp open ssl/http Cloudflare http proxy 8080/tcp open http Cloudflare http proxy 8443/tcp open ssl/http Cloudflare http proxy | ssl-cert: Subject: commonName=sni.cloudflaressl.com/organizationName=Cloudflare, Inc./stateOrProvinceName=CA/countryName=US | Subject Alternative Name: DNS:*.bytexd.com, DNS:sni.cloudflaressl.com, DNS:bytexd.com | Not valid before: 2020-08-01T00:00:00 |_Not valid after: 2021-08-01T12:00:00 Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port OS fingerprint not ideal because: Missing a closed TCP port so results incomplete No OS matches for host Network Distance: 13 hops TRACEROUTE (using port 80/tcp) HOP RTT ADDRESS 1 9.00 ms 192.168.43.1 2 ... 3 271.00 ms 10.170.173.129 4 ... 5 272.00 ms 10.244.24.22 6 ... 7 273.00 ms 202.56.7.237 8 273.00 ms 103.15.40.193 9 274.00 ms 103.230.17.74 10 275.00 ms dsl-ncr-dynamic-089.124.16.125.airtelbroadband.in (125.16.124.89) 11 313.00 ms 116.119.55.176 12 302.00 ms 182.79.223.41 13 289.00 ms 172.67.203.243 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 121.77 seconds
In the first section, we can see the port scan results with version detection shown in green color.
The next section shows some information related to the domain and it is marked in grey color.
Then we see the OS detection will also run in the aggressive scan.
Lastly, we can see the traceroute to bytexd.com and how far away it is.
ssh – Log Into Remote Machines and Execute Commands on Them
SSH is a protocol and it stands for Secure Shell. The ssh command provides an encrypted connection between two hosts using the SSH protocol. By default, this protocol is a CLI (Command Line Interface) based protocol.
If you have openssh installed in your machine, you can start the ssh service by:
sudo service ssh start
Check if the service is running:
sudo service ssh status
● ssh.service - OpenBSD Secure Shell server
Loaded: loaded (/lib/systemd/system/ssh.service; enabled; vendor preset: disabled)
Active: active (running) since Sun 2021-05-23 02:08:31 PDT; 1min 7s ago
Main PID: 3098 (sshd)
CGroup: /system.slice/ssh.service
└─3098 /usr/sbin/sshd -D
May 23 02:08:31 blackOS systemd[1]: Starting OpenBSD Secure Shell server...
May 23 02:08:31 blackOS sshd[3098]: Server listening on 0.0.0.0 port 22.
May 23 02:08:31 blackOS sshd[3098]: Server listening on :: port 22.
May 23 02:08:31 blackOS systemd[1]: Started OpenBSD Secure Shell server.
After checking you can connect to the server with the username and password:
ssh [username@host_address]
Then it’ll ask for the password of the specified user. Enter the password and then you can log in with ssh.
curl – Transfer Data From or To a Server With Many Supported Protocols
curl (also stylized as cURL) stands for client URL.
It is a very popular tool used for sending and receiving data from a server and automating the process.
The command supports several protocols such as HTTP, HTTPS, FTP, and many more.
It is available for Windows, MacOS, and other Unix-like operating systems.
The curl command has a very broad usage with different protocols. We’ve written a tutorial on HTTP protocol requests with curl in detail.
We’ll cover some of the basic commands with cURL here.
You can fetch website data with curl command without using any parameters:
curl example.com
You’ll see the webpage of example.com on your terminal. In the case of redirects, you can use the -L flag to follow redirects.
curl -L bytexd.com
Outputs can be saved to a file using the -o or -O flag:
curl -O https://github.com/pbatard/rufus/releases/download/v3.14/rufus-3.14p.exe
The difference between -O and -o flag is that the latter is used to specify a custom filename.
By default, curl sends HTTP GET requests. We can perform other request methods using the -X flag:
curl -X [method] [more options] [URI]
For example, you can perform a POST request like:
curl -X POST -d "p1=value1" https://httpbin.org/post
Here, the -d flag stands for data, and it allows us to pass the value to the parameter (p1).
Another interesting thing curl can do is show the header of the response. We receive headers with the GET requests but curl does not show it by default. We can use the -I or --head flag here:
curl -I example.com
HTTP/1.1 200 OK Content-Encoding: gzip Accept-Ranges: bytes Age: 447107 Cache-Control: max-age=604800 Content-Type: text/html; charset=UTF-8 Date: Sun, 23 May 2021 10:11:53 GMT Etag: "3147526947" Expires: Sun, 30 May 2021 10:11:53 GMT Last-Modified: Thu, 17 Oct 2019 07:18:26 GMT Server: ECS (nyb/1D07) X-Cache: HIT Content-Length: 648
This is the header of the response from example.com. The first line tells us about the HTTP version and a status code is shown.
The status code the part is 200 OK which essentially means the request has performed successfully without any errors.
Take a look at our curl tutorial to understand all the curl commands from the basics.
Conclusion
In this article, we introduced you to the basics of several networking commands in Linux. This article covers most of the networking tools you will encounter. You can learn more about most of these commands from the help (using the -h flag). All of the commands also have a manual page for you to learn more about them.
If you have any questions or feedback, feel free to contact us or leave a comment below, and we’ll get back to you as soon as possible.

Nearly all of these are deprecated and legacy. You should cover the current tools like ip, iw, ss.