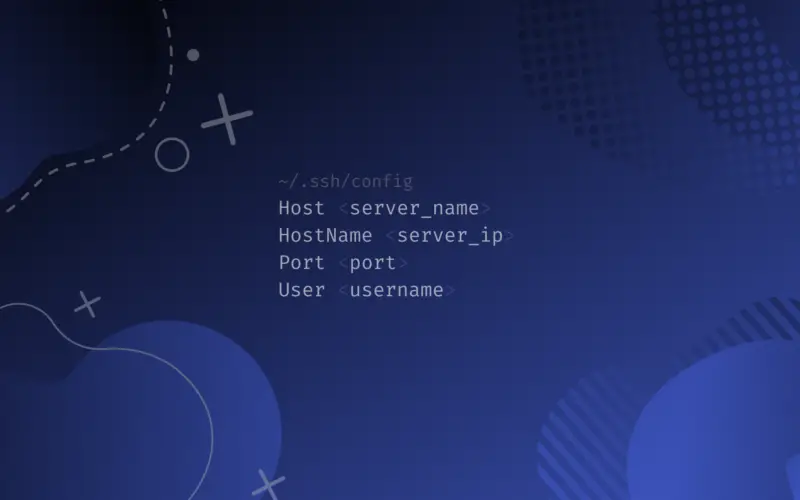
The SSH Config File is a text file that contains configuration information for your SSH client, such as the hostname of the server you are connecting to, your username, and your private key file.
This file is usually located in your home directory, and the path is ~/.ssh/config.
It’s useful to add aliases for your most commonly used SSH connections, so you don’t have to remember your server’s IP addresses, hostnames, usernames, port numbers, private key locations, and other options.
Additionally it’s great for keeping your SSH client’s configuration organized and for sharing your configuration with others, and also for automating your SSH client’s configuration.
In this tutorial we will learn by examples how to use the SSH config file to modify and simplify our networking needs using Linux.
Table of Contents
What is SSH
SSH (The Secure Shell Protocol) is a cryptographic network protocol.
SSH is designed for one computer to act as a server and the other as the client. In cryptographic terms it operates in three components.
- First, the transport layer is for server authentication, confidentiality and integrity. This component makes sure that the server you’re connecting to is really the one you’re trying to connect to and not one impersonating it. It makes sure that the connection is exclusive, that no other device has access to that established connection. It makes sure that the data transferred is interpreted in the client the same as it exists in the server.
- Second, the user authentication protocol validates that the client is indeed allowed to connect to the server.
- Third, the connection protocol multiplexes the tunnel between server and client to make communication channels.
This is the basic explanation how the SSH suite of protocols operate. With these encryption protocols, a computer using SSH can communicate to another computer in a secure encrypted manner even if the network connection is not secure or even if the connection is being snooped on.
Using SSH
Luckily for us SSH is an open source utility, it is installed by default in almost all of the Linux distributions out there. So you shouldn’t worry about installing it as it probably already is. Let’s get to using it.
The most basic functionality of SSH is to login to another computer.
Typically we do this by using the ssh utility followed by the system user of the computer we are connecting to, followed by @ character and the IP of the server computer. In our example below.
ssh root@178.62.251.218
Here we are logging in as the root user to server 178.62.251.218. As it is the first time connecting to this server SSH asks us if this is indeed the server we are trying to connect to. We input yes to proceed with the connection.
It asked us for the root user password and we were let in. Because we knew the password of the root user and the IP of the server, and the server had the SSH server component installed, we were able to login to that computer over the internet.
This connection we established was encrypted and secure.
Home Directory of SSH
Everything related to SSH gets placed in a .ssh hidden directory. This directory is almost always placed in the home directory of our system user.
In this demo we change directory to our .ssh directory. We list the files to see what’s there and notice a file. We open that file with the nano text editor to see what it is.
Remember when we logged in to our server, it told us that the authenticity of the host couldn’t be established?
That is because it was the first time we were logging in to that server. It was a stranger to our computer. Because we told it to continue login in, it saved the fingerprint of that server on a file named known_hosts in our .ssh directory.
This is what we opened and saw in the nano editor. Next time we login it will recognize that server’s fingerprint from our known_hosts file and it won’t ask us again.
If for some reason the fingerprint of that server changes, we will know that the server got manipulated, leading us to further investigation if necessary.
The SSH Config File
If we create a configuration file for SSH it will make our life easier. We can make some customizations to make managing our server connections easier. In the below example we see how to do one.
Inside the .ssh directory we run the following command.
touch config
This command creates an empty file named config without any extension. In Linux files are not obligated to have an extension like other operating systems. The SSH config file needs to be extension-less when using the default settings.
After creating the config file we open it with nano.
nano config
Inside nano we wrote the following configuration.
Host larrycurlymoe HostName 178.62.251.218 Port 22 User root
In this configuration we are telling it:
- that the host will use the nickname larrycurlymoe
- the hostname address is the IP address of our server (178.62.251.218)
- what port number it will use to connect to the server. We’re leaving 22, which is also the default SSH port
- finally that the user we’re logging into is the user root
After we set the config, saved and close it, we ssh into our server but this time instead of needing to write ssh root@178.62.251.218 we simply wrote the nickname we gave that connection in the config file, that is ssh larrycurlymoe.
Now we don’t need to remember complicated usernames and IP addresses, we simply have to remember one nickname.
Now we have two files in our .ssh directory, config and known_hosts.
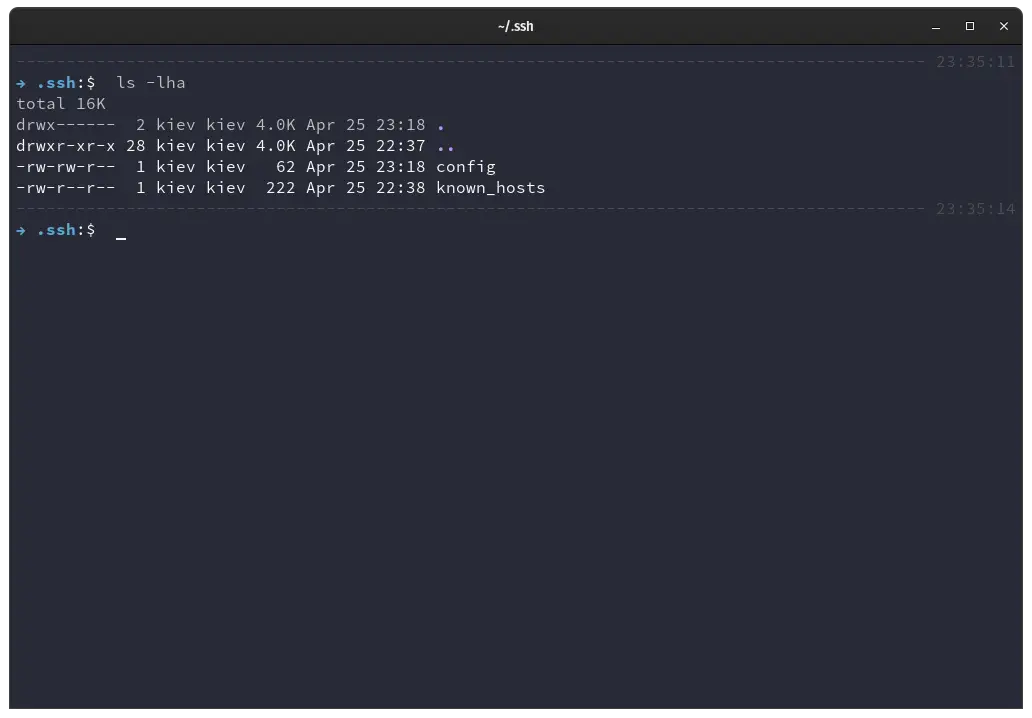
SSH Config Multiple Hostames
We can add as many server hostnames to our config file in the form of one stanza under the other.
Host larrycurlymoe HostName 178.62.251.218 Port 22 User root Host allinthefamily HostName 178.62.251.218 Port 22 User archibunker Host ilovelucy HostName 17.13.25.28 Port 22 User root
Here we edited again the config file with the nano text editor and we pasted a few more hostnames to connect to. We can see that the second entry is connecting to the same server IP but it’s using another system user.
For example, if we’re hosting a web server we make each site be managed under a separate system user.
In that case, if a website on our server would get hacked, the hackers wouldn’t control all of the system but only a single restricted system user.
In the third entry we added a completely separate server. So we learn that on the config file we can add some connection stanza that can be other system users in the same server and other connection stanza can be other servers completely.
Key Pairs In The SSH Config File
In the case that you are using SSH keys instead of passwords we can easily tell our config file which keys to use.
Assuming our SSH key pairs are already set up, we once again edit our config file with the nano text editor.
SSH keys come in pairs with a public key file and a private key file.
In the config file we add the location of the private key that we will use for that connection.
In our example we have three connection entries in our config file.
In our first entry we don’t add anything. In our second entry we add the location of our private key.
IdentityFile ~/.ssh/id_ed25519
In our third entry we add the location of another private key.
IdentityFile ~/.ssh/id_rsa
What happened here is that we added SSH keys to two of our three entries.
- The first entry will not use any SSH keys, it will continue to use passwords to login to that connection.
- The second entry will use our SSH ed25519 key located in our .ssh directory of our system user.
- The third entry will use another separate key, an RSA key, located also in the .ssh directory.
Here we can see that in our SSH config file we can have all sorts of connection combinations for our entries.
We can have some with keys and some with passwords. We can have different keys, and different types of keys. When using SSH keys you don’t need to have only one SSH key pair.
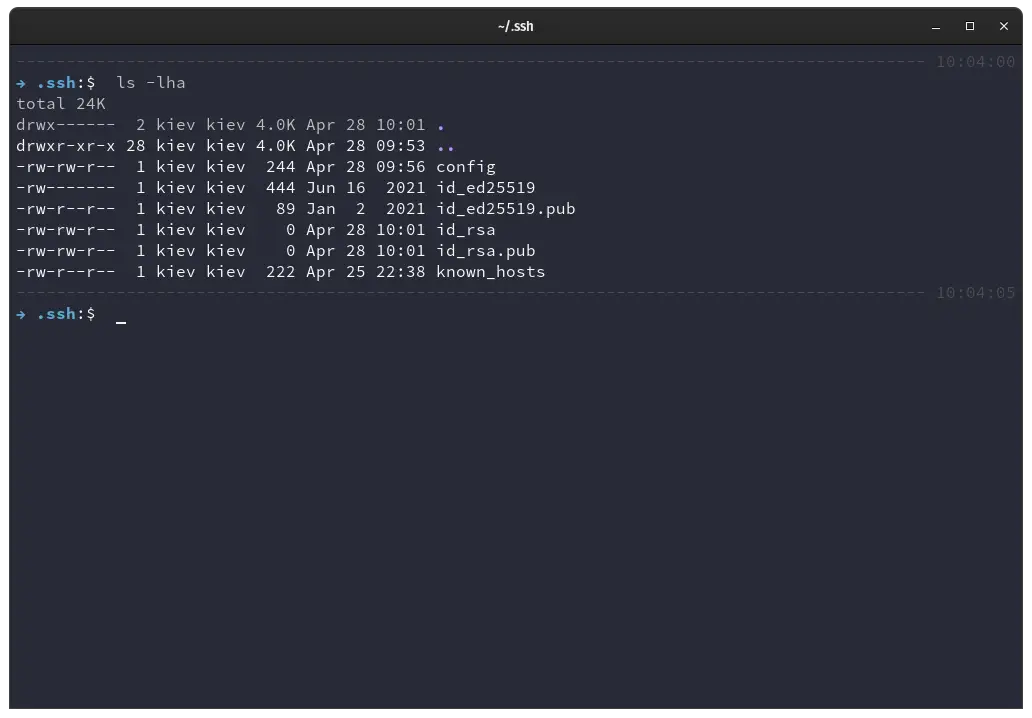
We can see our .ssh directory now has a few files. There is the known_hosts file, the config file, the ed25519 private and public key files and the RSA private and public key files.
While the key files can be placed in any directory in the computer, the .ssh directory is their default location and it’s the recommended place to put them in for newer users.
The complete entry of a connection in our config file should be looking like this.
Host allinthefamily HostName 178.62.251.218 Port 22 User archibunker IdentityFile ~/.ssh/id_ed25519 Host ilovelucy HostName 17.13.25.28 Port 22 User root IdentityFile ~/.ssh/id_rsa
SSH Config File Permission
While the primary way of using SSH and its config file is directly through our command line, there are other applications that can use them too. Graphical applications can use SSH and our config under the hood. Lots of enterprise and backup software utilize them.
In the last screenshot example we noticed something. The config file has a permission rw-rw-r--, this means a 644 code permission, specifically this means that only the user has read and write permissions; the group and others can read only.
Let’s change the file permission for only the user to have read and write access, that is code 600.
chmod 600 ~/.ssh/config
httpv://youtu.be/_E–DNB3tjw
First we list the files in the directory and see config with the rw-rw-r-- permission. With the chmod utility we change it to code 600. We list the directory again and see that config now has the -rw-------. Our config file is set for only the user to have read and write permissions.
While there is little difference between file permissions 600 and 644, some enterprise software that use SSH and the SSH config file are strict with permissions.
Some might specifically request either of these two permissions and if not set correctly they can glitch out or spit out errors before operation.
For the most part using either of these two permissions on the command line will not shield any errors and are safe to use. Change it back to 644 if necessary with the following command.
chmod 644 ~/.ssh/config
SSH Config File All Connections
In the SSH config file we can consolidate the configuration depending on our needs. Say for example we want all the connections to log all connection activity. Continuing with our example config, we would do that with the following style.
Host larrycurlymoe HostName 178.62.251.218 Port 22 User root Host allinthefamily HostName 178.62.251.218 Port 22 User archibunker IdentityFile ~/.ssh/id_ed25519 Host ilovelucy HostName 17.13.25.28 Port 22 User root IdentityFile ~/.ssh/id_rsa Host * LogLevel INFO
Here each connection stanza has a name to be invoked with, there’s another connection stanza with the * character that in Linux syntax it means all. So when making a connection, each connection will apply it’s configuration but it will also take the additional configuration of Host * stanza.
In this case this stanza is telling all connections the level of logging to make when establishing a connection.
Overriding a Configuration
So far we have learned how to config our SSH connections to make things simpler by saving the connection information in our config file. There are times though we would prefer to use our connection with a different set of configuration, temporarily. We achieve this by overriding it when we SSH.
Here is the original example.
Host larrycurlymoe HostName 178.62.251.218 Port 22 User root Host allinthefamily HostName 178.62.251.218 Port 22 User archibunker IdentityFile ~/.ssh/id_ed25519
The first entry larrycurlymoe is using the root system user every time it connects.
Instead of login in as root we will login as the archibunker system user.
ssh -o "User=archibunker" larrycurlymoe
Here we use the connection information for larrycurlymoe but login in as archibunker.
Following that command we would be prompted with a password prompt because larrycurlymoe is not set to use SSH keys.
With the -o option we are using all of the connection info of the larrycurlymoe stanza but overriding some of it.
In this example we didn’t want to login directly with the allinthefamily connection info because we wanted to login with a password and not with SSH keys.
By overriding things we can work with established connections configurations quickly.
Conclusion
In this tutorial we learned all about the SSH config file. What is the SSH config file and how to make one. Where to store it and how to format it. Hopefully you start using it. Using SSH key pairs we could skip the whole password prompt thing. Stay tuned for our guide on how to use SSH keys to increase the security of our connections, and make things even easier for us to manage our server connections.


![How to Use the fd Command in Linux ('find' Alternative) 19 $ fd [options]](https://bytexd.com/wp-content/uploads/2022/06/How-to-Use-the-fd-Command-in-Linux-‘find-Alternative-380x220.png)

