The Secure Shell or better known as SSH is the most used method to admin remote servers.
It’s an encrypted protocol so that two computers can communicate securely over the internet or any local network.
It works on the command line, invoking any of the utilities of the openssh secure networking application suite.
In this tutorial we’ll show you how to set up SSH keys on Ubuntu 22.04. SSH keys provide a more secure way of logging into a server with SSH than using a password alone.
In Linux servers, all services exposed to the internet, like a web server should be running under their own system user. And each system user should have their own set of SSH keys.
Table of Contents
Setting Up SSH Keys
While the conventional way to use a SSH connection is with a password, setting up SSH key pairs is the recommended way to use SSH.
Making SSH keys initiated connections secured from eavesdropping by man in the middle attackers or service providers.
Since Ubuntu 22.04 is the latest Ubuntu Long Term Support version released in April 2022, compatibility with clients will not be a concern. So the keys we set up can be of any algorithm we choose including the newer ones like ed25519.
In the example below we will login with SSH into a Ubuntu 22.04 server and set up SSH keys for it. The process is identical if setting up an Ubuntu Desktop computer.
ssh-keygen -t ed25519
With the ssh-keygen utility, that is part of the openssh suite, we command it to create a key. With the -t option we tell it which algorithm to use. In this case we are using the ed25519 algorithm which uses elliptic curve cryptography.
First it asks us to give it a name.
Enter file in which to save the key (/root/.ssh/id_ed25519):
We leave it empty so that it will use the default name. Then it asks us to give the key a passphrase.
Enter passphrase (empty for no passphrase):
We give it one. A passphrase is like a password that must be input for everything the key is going to be used for. After that is done ssh-keygen generates a cryptographic key. They come in the form of two files, one to be used as a private key and one to be used as a public key.
Your identification has been saved in /root/.ssh/id_ed25519 Your public key has been saved in /root/.ssh/id_ed25519.pub
The public key file has a .pub extension. And with that we have created a SSH key that we can use to connect to another server in an encrypted manner.
Checking SSH Key Fingerprint
Sometimes when working with servers with SSH keys already setup by other DevOps, it’s important to know what type of SSH keys they are. A simple way to find out information about the SSH key is with the same ssh-keygen utility.
ssh-keygen -l -f ~/.ssh/id_ed25519
We command again ssh-keygen this time with the -l option. The -l option tells it to give us the key’s fingerprint information. We also use the -f option to indicate the location of the key. Once done it will output us the fingerprint.
256 SHA256:Le5ulI2BxEMC0wbRb9KUdtLerM4lK6vt6sWGJUFcy98 root@2204Machine (ED25519)
Let’s explain the fingerprint:
- 256 is the key length in bits.
- SHA256:Le5ulI2BxEMC0wbRb9KUdtLerM4lK6vt6sWGJUFcy98 is the key’s fingerprint in SHA256 sequence
- root@2204Machine is the system user and hostname of the server
- (ED25519) is the algorithm used in the key
It’s important to check a SSH key’s fingerprint to know with which type of keys are we working with, specially in a multi admin environment or if you have inherited the server management from someone else.
Copy Public Key To Another Server
Now that we have a SSH key to use and we know everything about this key, it’s time to connect to another server to use them. We do by copying our public key to the server we want to connect to.
With another utility that is part of the openssh networking suite, ssh-copy-id , we will command it to copy our public key to the server we are connecting to.
ssh-copy-id root@188.166.41.75
After running the command we get a warning about the authenticity of the host not being established.
The authenticity of host 188.166.41.75 (188.166.41.75) can’t be established.
ECDSA key fingerprint is SHA256:kg7XIoEPT7i1OOjuoupqqUahuV1joZ1H8yEBcgG7aVo. Are you sure you want to continue connecting (yes/no/[fingerprint])? Yes
This means that it’s the first time we are logging in to this server. It doesn’t mean that it’s not encrypted or that the server has been hacked like some novice users worry about.
Every time we connect to a server for the first time, ssh adds the fingerprint of that server to a file called known_hosts.
After we agree to continue connecting, this server’s fingerprint will be added to that file.
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@188.166.41.75's password:
Then the ssh-copy-id utility attempts to log in with the new key to the server just in case it’s already present there and not being added a second time.
Since our public SSH key is not in that server, ssh-copy-id proceeds to install our public key requesting us for the system user password for it to be able to login and install the key.
Number of key(s) added: 1
Now try logging into the machine, with:
ssh root@188.166.41.75
And check to make sure that only the key(s) you wanted were added.
Finally it confirms that the public key was installed. Now our 2204Machine server will be able to connect with SSH using cryptographic keys.
If we have multiple keys in our system, with the -i option we can specify which key to use based on its location.
ssh-copy-id -i ~/.ssh/id_rsa.pub root@188.166.41.75
With that we have finished setting up SSH keys on an Ubuntu 22.04 server.
Copying SSH Keys On Server That Has Disabled Passwords
Disabling password authentication in SSH is the recommended practice industry wide.
Sometimes the password connection attempts are thousands per hour or even more. So much so that if our server is on the low end side with a small amount of resources, it can slow it down significantly.
By leaving password authentication on, our server accepts all password login attempts from everybody. After an attempt is established, the server has to process that attempt by determining if the password is correct. Imagine that happening hundreds of times per minute, our CPU is being wasted, potentially creating a Denial of Service attack.
This is why it’s always recommended to turn off passwords.
But to be able to use the ssh-copy-id utility to copy our ssh keys to another server, first it needs to log in with a password.
Only then our connection happens with the keys. So what to do if password authentication has been disabled on the server? We have to copy the public key manually.
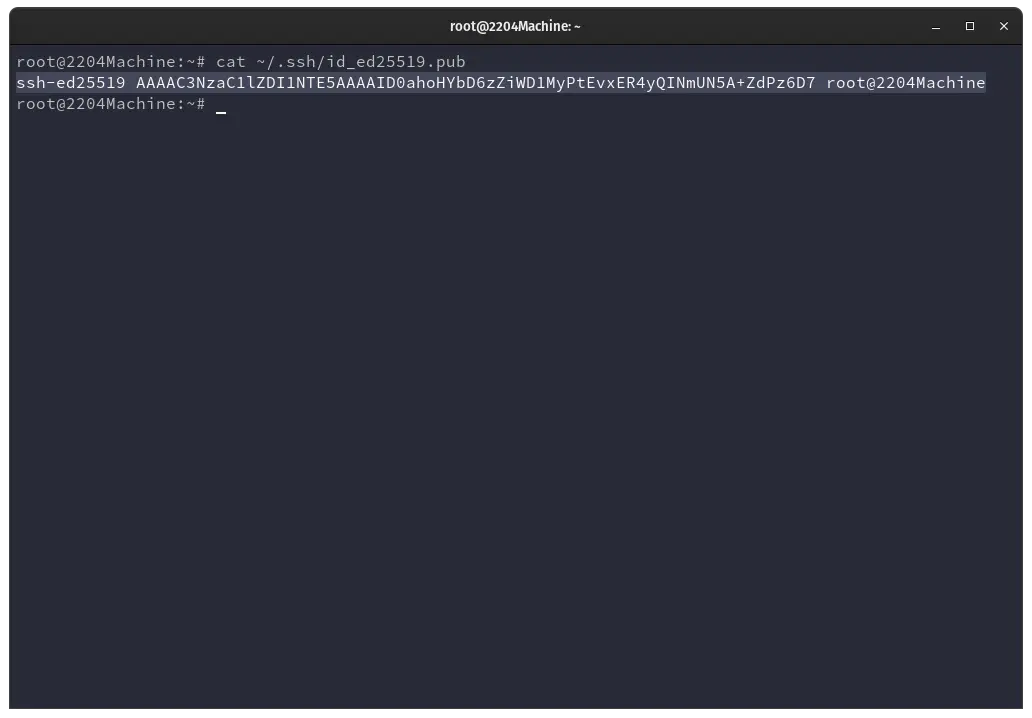
cat ~/.ssh/id_ed25519.pub
We will use the cat command to output the content of our public key. After running the cat command on our public key, the content of the public key gets printed on our command line.
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAID0ahoHYbD6zZiWD1MyPtEvxER4yQINmUN5A+ZdPz6D7 root@2204Machine
This output is our public key. From start to end we must copy it all.
Then we manually have to paste our key we just copied to a file on our server called authorized_keys, located in the .ssh directory of our system user’s home.
How we copy this key to the authorized_keys file is the tricky part.
If you currently have another system user with SSH access to the server, you must log in with that user to add the key. We do that with the following command.
Once we log in to a system user that currently has access to the server, we will change directory with sudo cd to the .ssh directory of the system user we want to add the public key to.
In Ubuntu 22.04 the structure of system user’s home directories are /home/systemuser/.ssh and the .ssh directory is where the authorized_keys file is located at. Substitute the systemuser portion with the real system user name in your server.
sudo cd /home/systemuser/.ssh
After we sudo cd /home/systemuser/.ssh we command the echo utility to appent to the authorized_keys file with our public ssh key. In Linux >> indicates to append to a file, while a single > indicates to replace it.
Be careful when echoing content to a file, a single > might replace valuable information and is not recoverable.
echo ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAID0ahoHYbD6zZiWD1MyPtEvxER4yQINmUN5A+ZdPz6D7 root@2204Machine >> authorized_keys
Having another user with current SSH access is the way to copy a public key to give that key access to the server.
If you don’t have another system user with current SSH access, lots of server providers nowadays have backdoor access to your server or console access.
Usually going to the dashboard of your server provider’s website, look for a place in the server management page to input your public key we copied.
How To Disable SSH Password Authentication On Ubuntu 22.04
Now we know all about SSH keys. That they are more secure and more convenient than password authentication.
That password login attempts expose our server to possible attacks, it’s time to learn how to disable SSH password authentication to make our server environment even more secure.
We need to edit the SSH configuration file. We find this file inside the /etc/ssh directory. As such we need sudo permission to be able to access it. If your system user doesn’t have sudo privileges it will not be able to modify this configuration.
sudo nano /etc/ssh/sshd_config
We edit the SSH configuration with an editor, in our example we invoke the nano text editor behind the sudo command. We then look for the following directive.
PasswordAuthentication yes
We edit the file by changing the yes to a no. We saved and closed the configuration file. After we’ve made our change we have to restart the ssh service in order for it to apply our changes. We do that with the systemctl utility behind the sudo command.
sudo systemctl restart ssh
After this change, password logins to our server will be disabled. There’s no going back. Make sure that you have a system user with SSH keys already installed in the server. Preferably more than one user, and at least one of them that has sudo privileges.
There’s no way to regain access and your server will be uncontrollable. Only thing that you would be able to do at that point is to take the server offline.
Don’t be afraid to disable password authentication though, it’s the proper way to secure and protect a server.
Conclusion
If we are using Ubuntu 22.04 server or desktop, and we are connecting via SSH to other computers, the best way to do it is by using SSH keys.
Today we learned how to set up SSH keys on Ubuntu 22.04 with the ssh-keygen utility. How to copy our keys to our remote machines the easy way via ssh-copy-id and the manual way.
We learned why we need to disable SSH password authentication and how to do it. The Secure Shell protocol is a staple in the Linux world and learning how to use cryptographic ssh keys is the best investment you can make in your daily Linux life.