In most modern operating systems, there are various levels of authorities a user can have, which governs who have the power to access files on the system.
Sometimes you need to execute a command as the root user (or as another user without logging-out and logging in again!), but in this case you should have the authority to do so! If you can’t that means you are not in the sudo group, neither you are in the sudoers file!, in this article, we are going to explain both ways to grant a user that authority. (Note: sudo is the acronym for Super User DO).
Table of Contents
Add the User to the Sudo Group
This way is the default in all Debian-based systems. Members of this group can execute any command as root (and in turn as any other user in the system), so the process is fairly straight-forward.
You have to login as a user that has the authority to execute commands as root (the first user which is created when setting up your machine will have that authority by default).

Open-up a terminal window either graphically or by pressing t while holding both Alt and Shift keys.
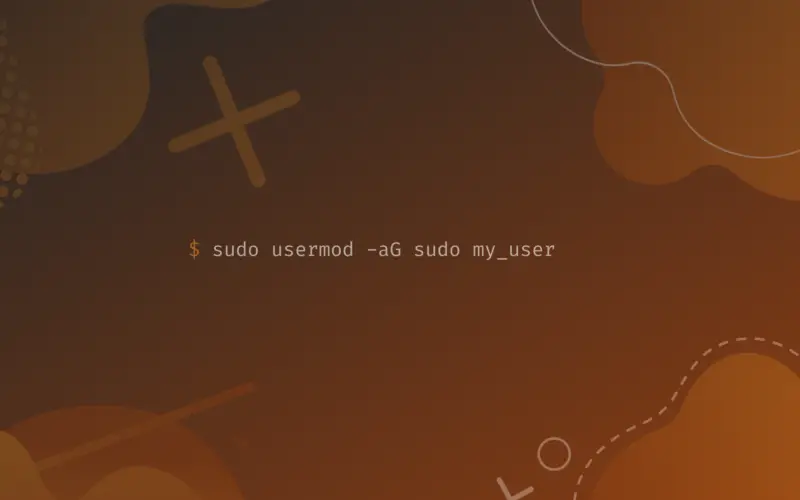
Execute the next command to add the user rootie to the sudo group (don’t forget to pass-in your password).
sudo usermod -aG sudo rootie

The flag a stands for append, and G stands for group, you need to change rootie by your targeted user’s name.
You can check if the previous command ran successfully by running any command as root.
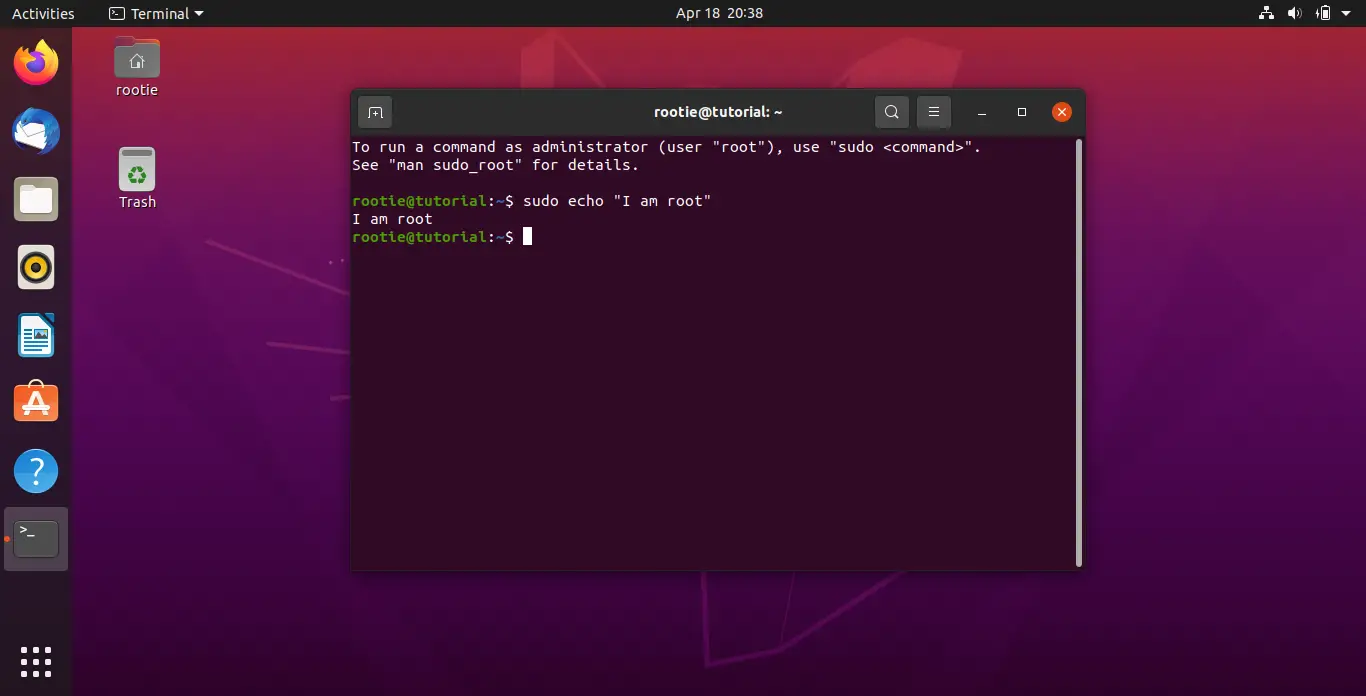
sudo echo "I am root"
If the output is the phrase in quotes, that means you are in sudo group now!
Add the User to the Sudoers File Separately
This file contains rules that controls user’s and groups authorities, you can also change and customize all the levels of permissions for a user or a group. You can grant or inhibit any access for a user or a group by changing the rules in that file.
The default sudoers file is located in /etc/sudoers, and hence it controls sensitive authorities and permissions you can’t edit this file using any text editor, you can only use a specific command to edit that file, to make sure you don’t mess up the file and accidentally lose super user privileges altogether.
You have to login as a user that has the authority to execute commands as root (the first user which is created when setting up your machine will have that authority by default).
Open-up a terminal window either graphically or by pressing t while holding both Alt and Shift keys.
Execute the next command to edit the sudoers file (pass your password!). In Ubuntu 22.04 and 20.04 it opens up nano editor by default:
sudo visudo
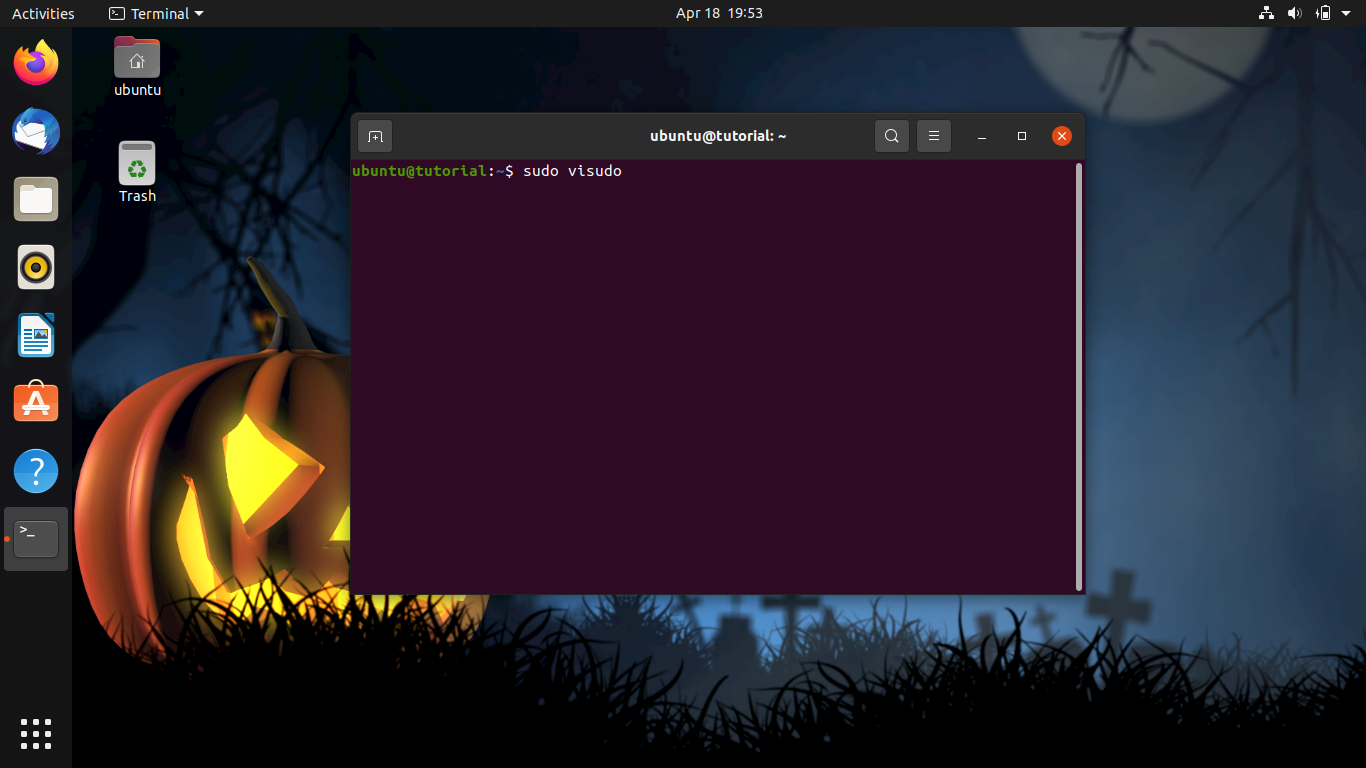

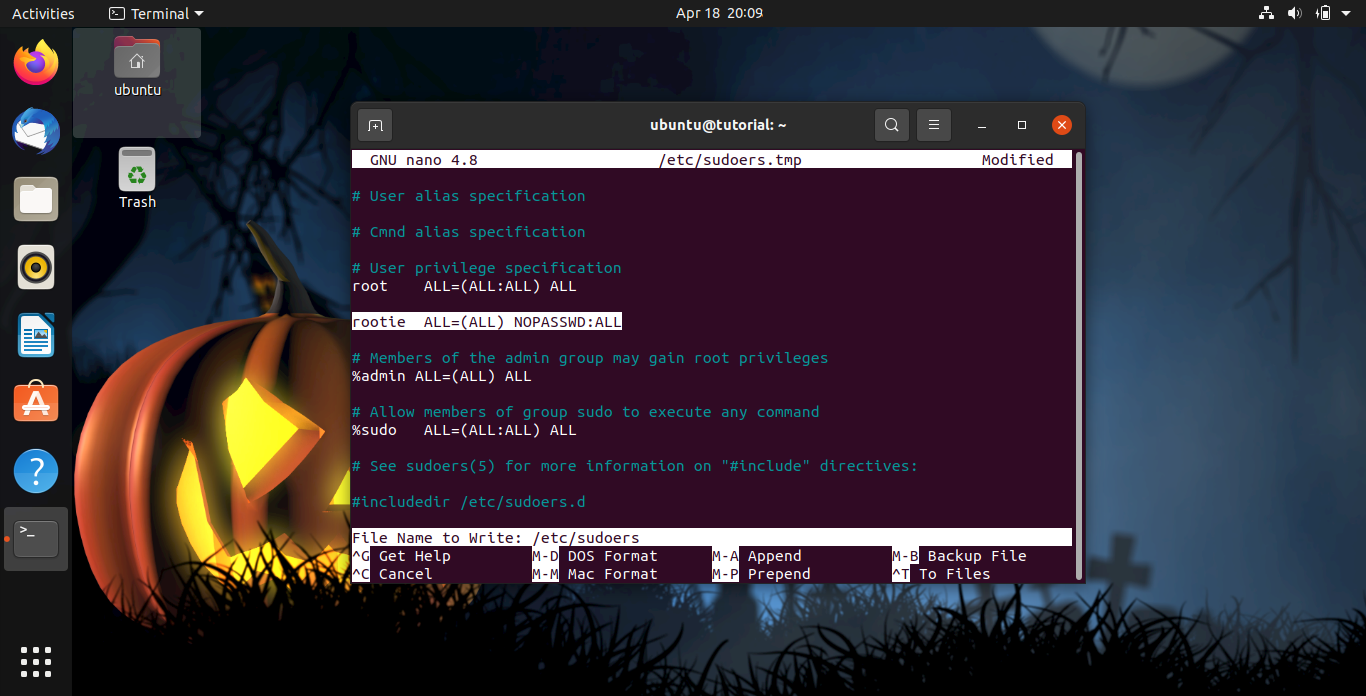
Go to near the end of the file, just below the last entry in the section that says # User privilege specification, and add the following line.
And add the following line:
rootie ALL=(ALL) NOPASSWD:ALL
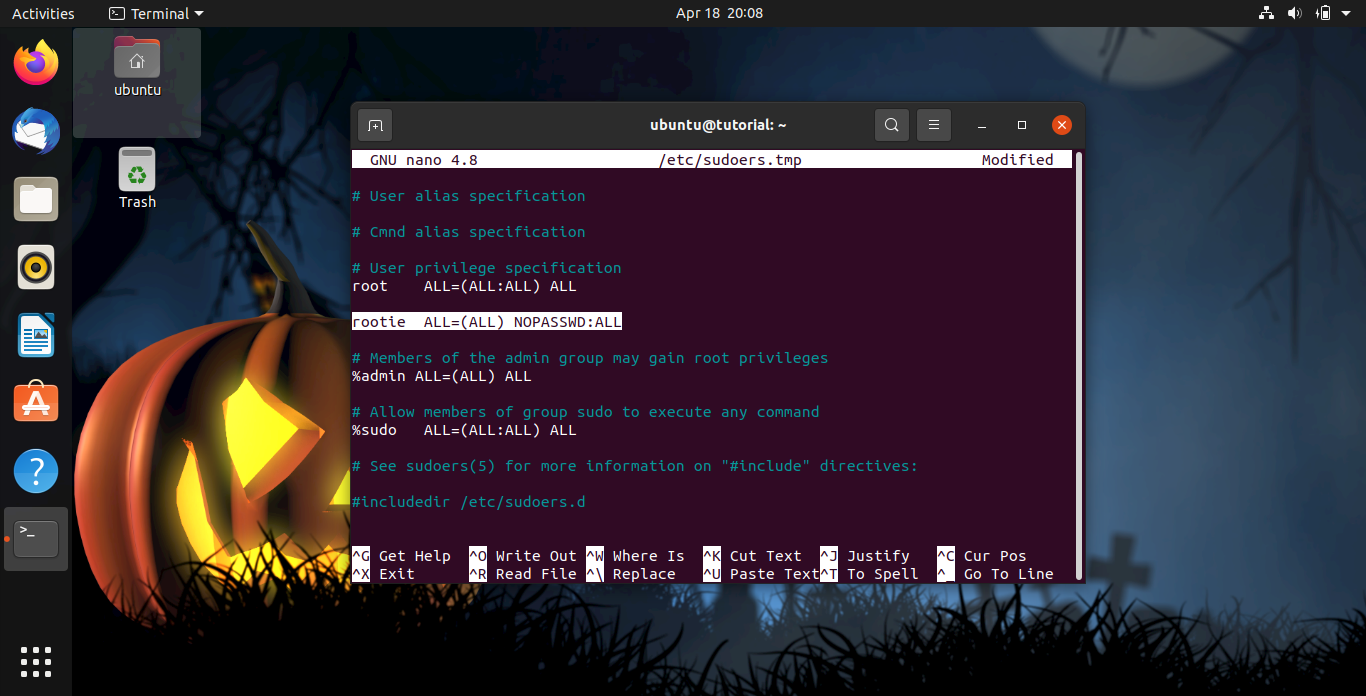
Hit Ctrl+x to exit, it will ask you if you want to save the modified buffer, enter y, and then rename it to /etc/sudoers, then answer y to rewrite.
You can check if the method was successful (or not) by running any command as root in you user’s account:
sudo echo "I am root"
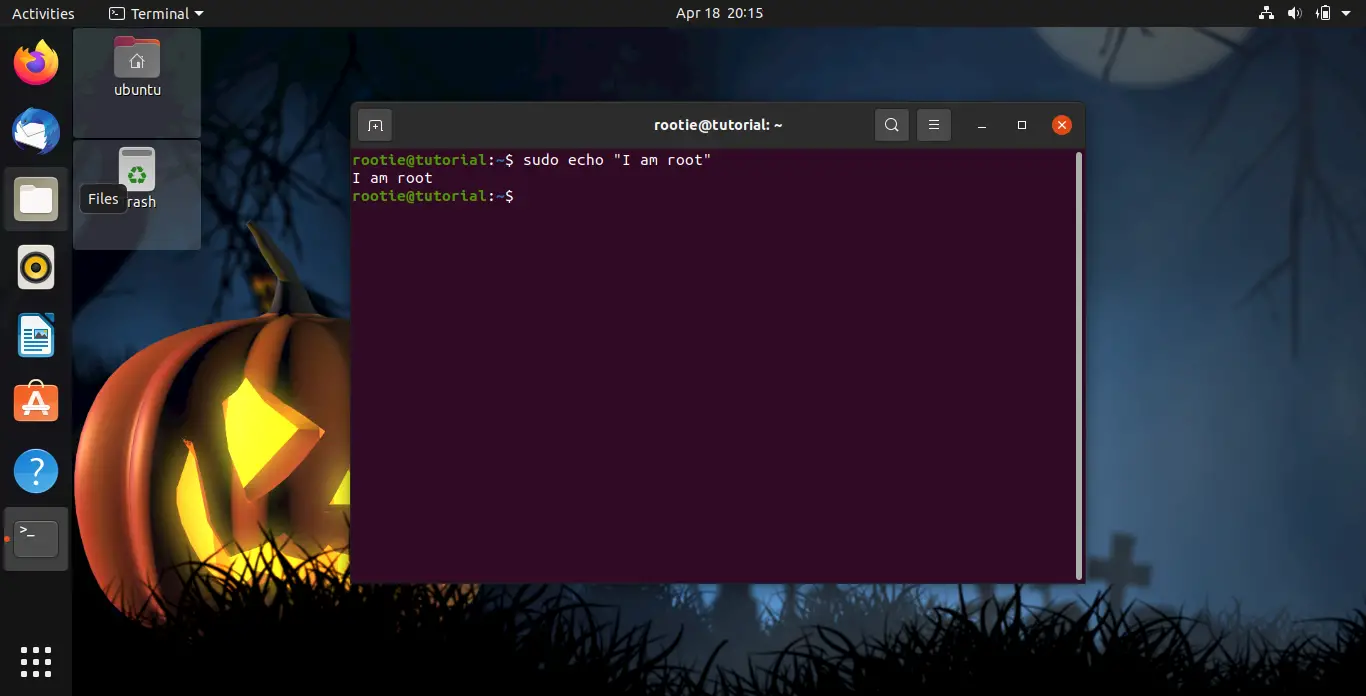
If the output is the phrase in quotes, that means you’ve granted the user rootie all super user privileges.
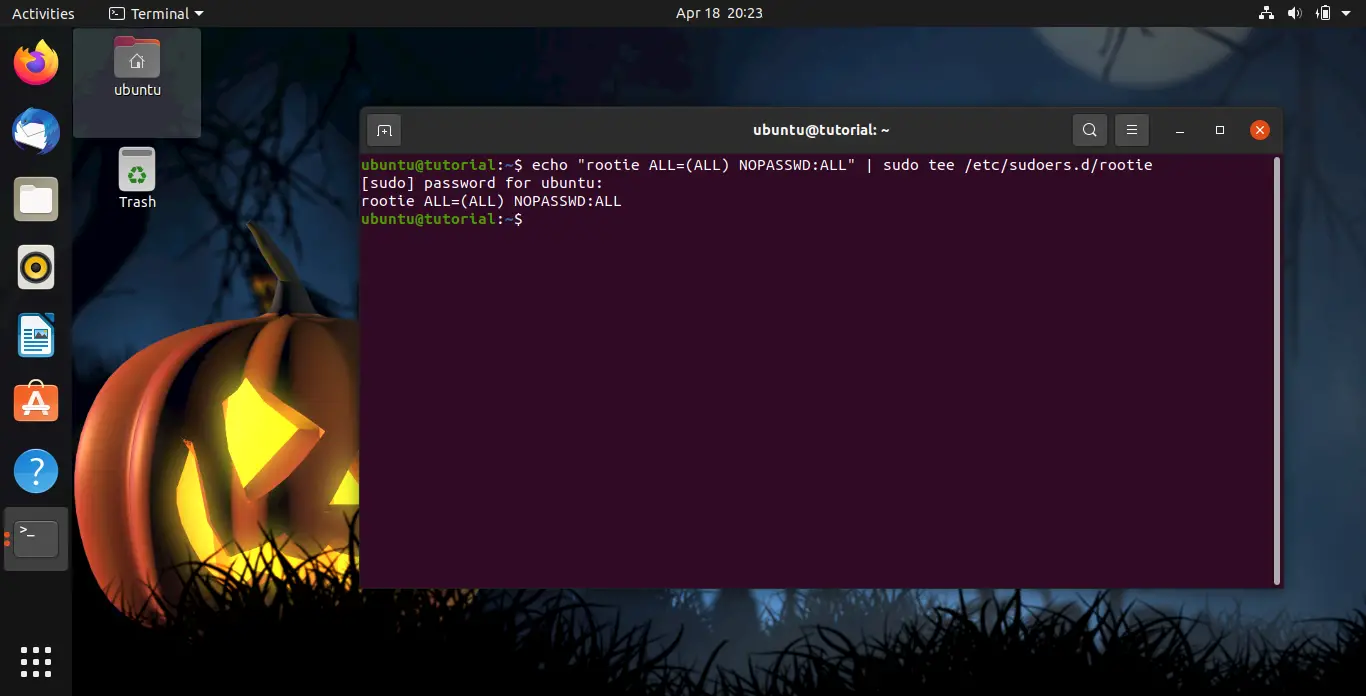
Or better than editing the default file, you can add a new file (conventionally named the same as the user’s name) to the directory /etc/sudoers.d, in the new file you add the same rules as above.
echo "rootie ALL=(ALL) NOPASSWD:ALL" | sudo tee /etc/sudoers.d/rootie
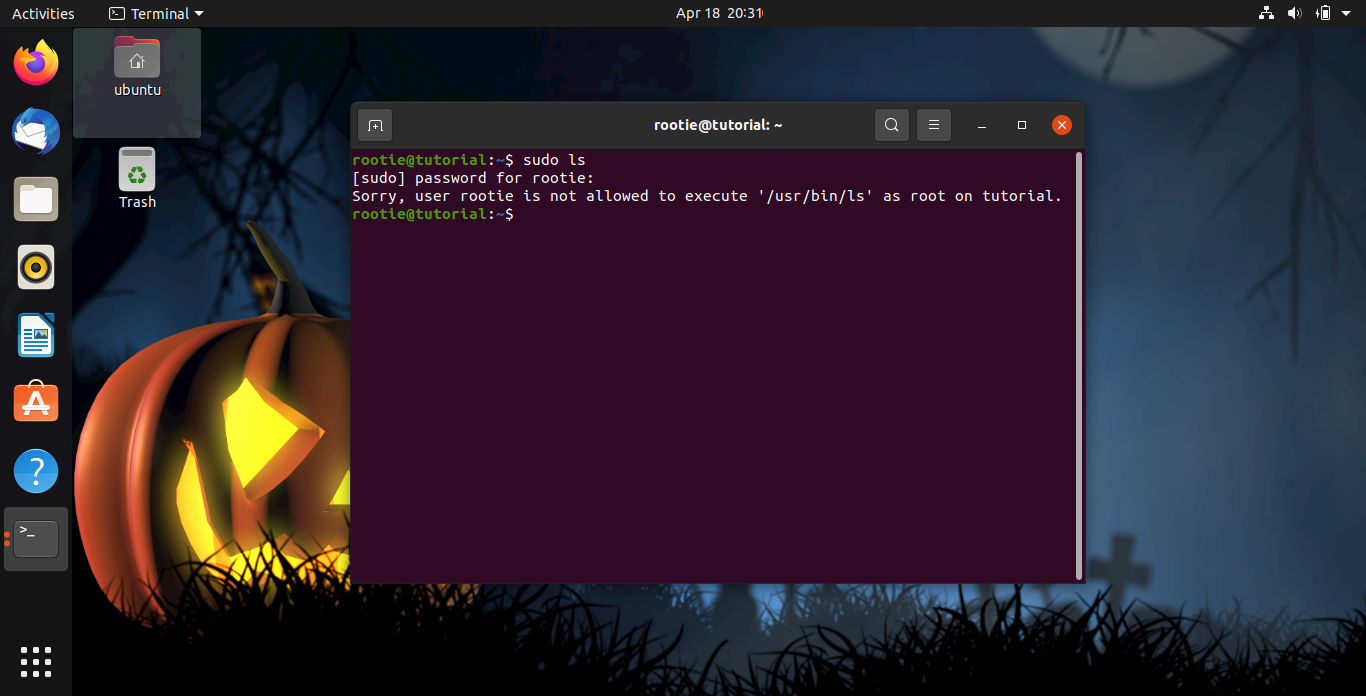
You can also allow specific commands to be executed as root by changing the NOPASSWD segment and adding the commands which you want to give the user of executing as root (here I add just echo and pwd commands):
rootie ALL=(ALL) NOPASSWD:/bin/echo, /bin/pwd

Conclusion
Adding a user to the sudo group is simple and straight-forward, yet limiting, but adding the user to the sudoers file is powerful, so you can know exactly which user has which authority, and it is easier this way to grant or revoke any privilege of the user by just editing one line.
![How to Install and Use Telnet on Linux 27 telnet [options] host [port] on light blue background](https://bytexd.com/wp-content/uploads/2022/06/How-to-Install-and-Use-Telnet-on-Linux-380x220.png)



