OpenSSL is a set of crypto and hash tools that can be used to encrypt data and verify signatures. It’s a command line tool that can be used to generate keys, encrypt and decrypt data, sign and verify signatures, and generate and verify CSRs.
In this tutorial, we’ll cover some of the most common OpenSSL commands and how to use them. We’ll also discuss important terms and concepts related to encryption and digital signatures.
Table of Contents
OpenSSL Concepts and Keywords
SSL (Secure Sockets Layer): The old, now deprecated, cryptographic protocol for establishing secure channels. Available in versions 1, 2, and 3 (all are obsolete due to security vulnerabilities and should not be used anymore).
TLS (Transport Layer Security): The actual cryptographic protocol, the successor of SSL. Available in versions 1.0, 1.1 (both deprecated), 1.2 and 1.3.
Public Key Certificate: They provide authenticity (as one peer proves its identity to the other) and privacy (as the communication is encrypted end-to-end).
About the domains, a certificate can be valid for a single domain (www.example.com), multiple domains (www.example.com and mail.example.com), or a wildcard certificate, that is valid for all subdomains of a domain (*.example.com)
Server Certificate: the most common certificate, used to encrypt the communication between a server (usually a web or mail server) and the client, and also to prove to the client that the server is who it claims to be.
Client Certificate: used to authenticate the client to the server, instead of using the traditional username/password pair (tough sometimes the certificate and the username/password are used together).
Self-signed Certificate: a self-made certificate, will not provide authenticity (because it is not signed by a CA), but still provides privacy (by encrypting the connection).
CA (Certificate Authority): a company or entity that issues and signs SSL/TLS certificates. It is based on the concept of a Chain of trust, where the CA itself has a certificate, that is trusted by the clients’ applications. This certificate is then used to digitally sign other certificates.
PKI (Private Key Infrastructure): An environment for keeping a CA. Contains tools for create, sign, store and revoke CAs, certificates
CSR (Certificate Sign Request): Ideally, the private key should not leave the host machine, as it is the private part of the pair. For creating a certificate signed by a CA, a user can generate a CSR. The CSR contains a public key derivated from the private key. The CSR is then sent to the CA, who will sign it and generate a certificate (which is also public, and useless without the respective key, that never left the host machine). Then, the certificate and its key can then be installed in the desired system.
PEM (Privacy Enhanced Mail): is a format where a DER certificate is encoded using base64. Its commonly used for CSRs, keys, and certificates in Linux systems. The data for the certificate is enclosed between specific headers:
-----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- -----BEGIN CERTIFICATE REQUEST----- and -----END CERTIFICATE REQUEST----- -----BEGIN RSA PRIVATE KEY----- and -----END RSA PRIVATE KEY-----
Due to this format, we can have more than an item (for example, the certificate and the private key) in the same file.
PKCS#12: another format for storing certificates and keys. It is a binary file, that contains the certificate, the chain certificate (of the CA), and the certificate key, all in one file. Its commonly used on Windows systems.
CRL (certificate revoke list): Every certificate has a serial number. If a certificate is revoked (for example, if it is believed to be leaked), we can add its serial number to a CRL. This way we can check the CRL and if the certificate is listed there, we do not accept it even if it is otherwise valid. CRLs can be kept both as a file or as an online service.
Example OpenSSL Subcommands
OpenSSL command is made of several subcommands, each one of them providing different functionality. This is a list of the main subcommands, their syntax, and usage.
openssl.cnf config file. The file’s location may change depending on the Linux Distro that is being used. You can find the OpenSSL config directory (where the config file is stored) by executing openssl version -d. Also (for subcommands that use the config file), you can specify a different config file using the -config option or declaring an environment variable called OPENSSL_CONF pointing to the configuration file.ca
Commands for managing a CA (Certificate Autority).
OpenSSL ca subcommand syntax:
openssl ca [options]
passwd
This command is used to generate password hashes.
OpenSSL passwd subcommand syntax:
openssl passwd [options] [pasword]
Options:
-crypt: use the crypt algorithm (default)-1: use MD5 algorithm-5: use sha256 algorithm-6: use sha512 algorithm (this is the algorithm used in Linux modern distributions for storing the password in the /etc/shadow file).-in <file>: read passwords from file-stdin: read passwords from stdin-salt <string>: use the specified salt. The salt is a piece of data that is prepended to the password before it is hashed, to make it harder to match the hashed password to the original one.
pkey
Manipulates private keys. Allows conversions between formats and printing a PK info.
OpenSSL pkey subcommand syntax:
openssl pkey [options]
Options:
-inform <DER|PEM>: specify the input format as DER or PEM (the default).-outform <DER|PEM>: specify the output format as DER or PEM (the default).-in <file>: the file to read the key from. If it’s not informed, the key is expected from the standard input (stdin). If the key is encrypted, a passphrase will be prompted.-out <file>: the file to write the key to. If it’s not informed, the key is sent to standard output (stdout).-passin <arg>: the input password source (check section Password Format below)-passout <arg>: the input password source (check section Password Format below)
rand
This command is used to generate pseudo-random data. It can be used to generate random data for use as a password or key.
OpenSSL rand subcommand syntax:
openssl rand [options] num
Options:
num: the number of bytes to output-out: write to file instead of standard output-base64: encode output into base64-hex: shows the output as a hex string
s_client
SSL/TLS client for connecting and diagnosing SSL servers.
OpenSSL s_client subcommand syntax:
openssl s_client [options]
Options:
-connect <host:port>: defines the host and port to connect to.-bind <[host][:port]>: defines the host and/or port to use to connect to the remote host.-proxy <host:port>: defines the host and port of the proxy to use with the -connect flag.-4: forces use of IPv4-6: forces use of IPv6-cert <file>: certificate file to use. The default is not using a certificate.-certform <PEM|DER>: the certificate file format. The default is PEM.-key <file>: key file to use. The default is not using the certificate file (if informed).-keyform <PEM|DER>:-pass <arg>: the private key password source (check section Password Format below)
version
Shows the OpenSSL version and other info.
OpenSSL version subcommand syntax:
openssl version [options]
Options:
-a: shows all options-d: shows config directory path-v: shows library version
Password Format
pass:password – the password is informed directly
env:var_name – the password is stored in an environment variable called var_name
file:pathname – the first line of the file informed contains the password. If the same file is informed for the -passin and -passout options, then the file’s first line will be used for the input password and the second line for the output password.
fd:number – for reading the password from a file descriptor
stdin – read the password from standard input (stdin)
Examples of Using OpenSSL Subcommands:
Customize OpenSSL config file (optional)
Locate OpenSSL config directory.
openssl version -d
Copy system openssl.cnf file to the current directory for customization:
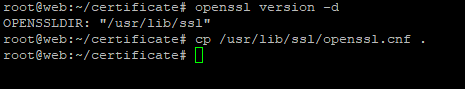
Customize the following fields to match your needs. This field will be used on the certificates:
countryName_default = US stateOrProvinceName_default = NY localityName_default = New York City 0.organizationName_default = Example Company organizationalUnitName_default = IT
-config openssl.cnf flag from the examples below.Creating a CSR
openssl req -config openssl.cnf -new -keyout ExampleCriptKey.pem -passout pass:MyKeyPassword -out ExampleCSR.pem
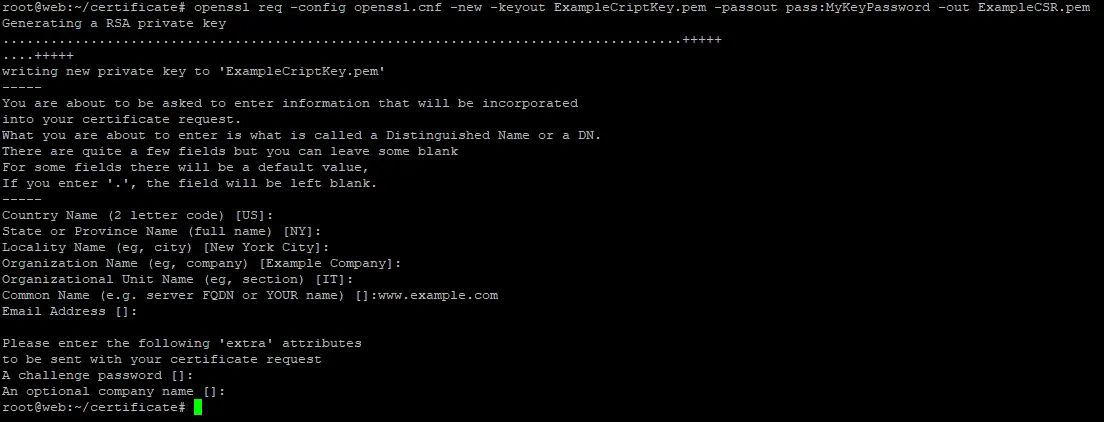
This command will create a (encrypt) private key named ExampleCriptKey.pem. The key password is MyKeyPassword. Then, a CSR will be created. To use the default values of the fields, just press enter. Note that the default values follow the values used on the modified openssl.cnf. The ExampleCSR.pem contains our CSR, which will be sent to the CA for signing.
Removing the passphrase of an RSA Key
The RSA key created in the previous step has a password. Every time we use it, we need to type this passphrase. We can remove the password (actually create a new file without the passphrase) with the following command:
openssl rsa -in ExampleCriptKey.pem -out ExampleKey.pem -passin pass:MyKeyPassword
The ExampleKey.pem file will be created, with the unencrypted RSA key inside.
Converting a pkcs12 key and certificate to PEM format
openssl pkcs12 -in filename.pfx -out cert.pem -nodes
Creating a self-signed certificate
As said before, a self-sign certificate will provide privacy (as it will encrypt the connection) but not authenticity (as it was not signed by a valid CA). But it is useful sometimes, for example for testing.
openssl req -x509 -newkey rsa:4096 -sha256 -days 3650 -nodes -keyout example.key -out example.crt
The -days option defines the certificate validity time (3650 days = 10 years from now)
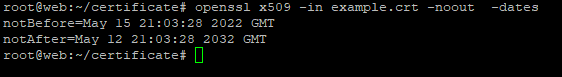
Analyzing a Certificate validity
openssl x509 -in example.crt -noout -dates
Conclusion
In this article, we’ve covered some of the most common OpenSSL commands and their usage, as well as some key terms and concepts. We’ve also included some real-world examples to show you how these commands can be used in practice.

![How to Use the fd Command in Linux ('find' Alternative) 8 $ fd [options]](https://bytexd.com/wp-content/uploads/2022/06/How-to-Use-the-fd-Command-in-Linux-‘find-Alternative-380x220.png)